Database Security
A database management system, or DBMS, is a tool that creates and manipulates databases. Examples that are used regularly are Google Spreadsheets and Microsoft Excel. Other programs that are more widely used by database developers include MySQL, Microsoft Access, and Microsoft SQL Server. Unfortunately, there are many people out there who would like to get into your database for your information. Learn how to secure your information here.

How Current Is Your Data Security Knowledge? Take Our Quiz and Find Out!
Data security is becoming one of the most important tasks as hacking is on the rise. Do you have what it takes to keep your data safe? Test your skills and knowledge with our quiz on modern data security issues!
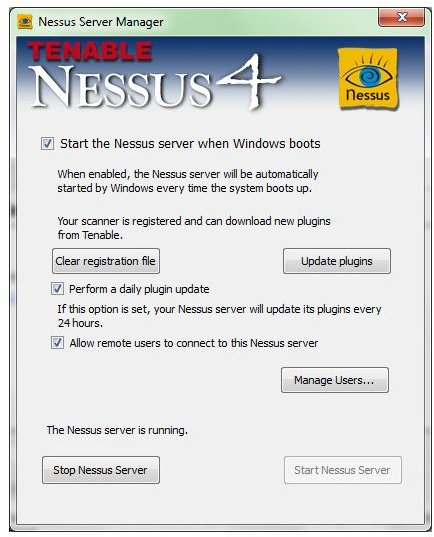
Network Scanning Tool Tenable Nessus Reviewed
A top rated network auditing tool with a free version for home use? It must be Tenable Nessus!

How to Use the Tenable Nessus Scanner: Page One
Knowing what’s up with your hosted website can help in ensuring stable uptime, that your TCP ports are set without risk of vulnerabilities and that any database stores (like with MySQL) are functioning properly. We can learn of these with Tenable Nessus, and we’re guiding you through the software.
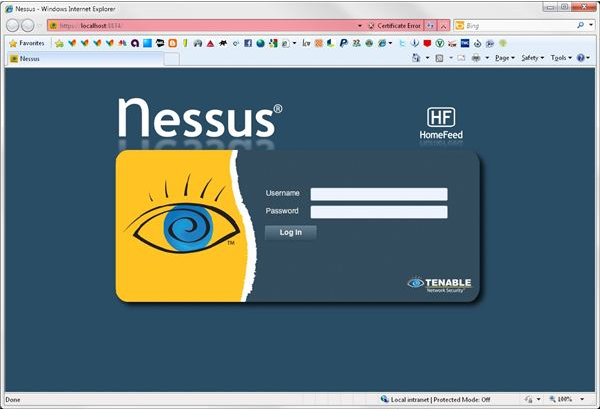
How to Scan a Database with Nessus -- Page One
Knowing what’s going on with your hosted website is crucial to ensuring that uptime is stabilized, TCP ports are set without open vulnerabilities, database stores are functioning properly and that everything is running like it should, and Tenable Nessus detects and shows it all by level of severity.
Nessus vs. Nmap - Comparing Vulnerability Scanners
Looking for a vulnerability scanner that will do the job, yet not burn through your limited budget or resources? Look no more. Check out Nessus or Nmap. Both have capabilities, but one is better than the other. Nessus vs Nmap - which one to use?

Storage Security Policies:A 101
This article will describe some key elements to consider when drafting a storage security policy. It will look at how process management and user effort can affect the security of data storage.

Phishing Protection: Don't Become a Victim
Fishermen purposefully bait their fishing lines with tempting food to catch unsuspecting fish, but computer phishers aren’t legitimately trying to catch dinner when they set traps for computer users. Instead, computer phishers are trying to steal their next meal–at your expense.

List of the Best Free Security Software for Windows and Mac
Free security tools are not only popular but effective, handy and useful. This article will be updated often with list of security programs to try when you need them.

BHO Remover Review
Spyware and legitimate programs can add component as Browser Helper Object in a browser and you might want to find out whether it’s a known safe BHO using BHO Remover.

A Guide to Changing the Destination File for Windows Updates
This article will discuss how to change the destination file for Windows Updates temporarily. Windows Update is a service by Microsoft that allows systems to either manually or automatically download updates for their operating system
