How to Design a Secure Internal Network & Remote Access Using Encryption
Network Security Design Considerations
Designing network security for a SMB requires following the same basic principles as those governing large enterprise security.
- It’s all about the data. When securing your network, always consider the sensitivity of the information stored, processed, or passing through your network.
- Secure information accessed remotely. In today’s business environment, customers, employees, and business partners often require access from offices, hotel rooms, and homes.
- Segregate remotely and publicly accessed systems from the internal network.
- Safeguard wireless access. The most important thing to remember about wireless is that it is inherently insecure, unless you take steps to protect the data wireless devices exchange in public as well as private locations.
- If appropriate, segment your network. Network segmentation, dividing your network into two or more logically separated networks, helps prevent the spread of malware, hinders intruders into one system from getting to other systems, and helps enforce access control efforts.
- Encrypt when appropriate.
I believe that using pictures is a good way to explain technology. So we’ll base our examination of network security design using two diagrams representing examples of remote access and a typical SMB internal network.
Designing a Secure Internal Network
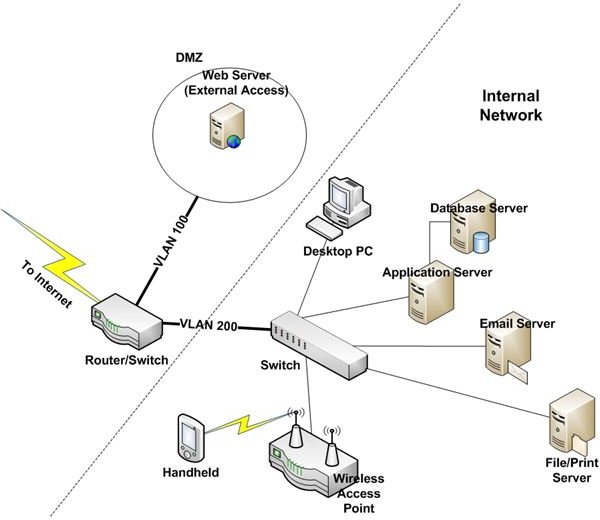
Please refer to Figure 1 as we walk through considerations for securing your network.
This is a good conceptual representation of the network needed by most SMBs. Since most small and medium businesses use the Internet as their connection to the rest of the world, including customers and business partners, I don’t discuss point-to-point circuits or complex router configurations.
Let’s start with the perimeter device: the router.
Routers must be placed between the cable modem–or other communication medium–connecting your business to the Internet. In our example, the router is used to connect to the Internet and to segment the company network. (For detailed explanations of routers and switches, see Introduction to Local and Wide-area Networks, Part 4 and Part 5.)
In our example, we have two virtual local area networks (VLANs). VLAN 100 is used to access a public Web server. No systems with sensitive information reside on it. All internal devices containing critical applications and sensitive information reside on VLAN 200. A security control known as an access control list (ACL) determines who and what can travel over each.
For example, an ACL would typically prohibit remote devices from accessing the internal devices on VLAN 200 while allowing access to the Web server. If the internal switch supports it, you could create additional VLANs to segregate the application, database, email, and file/print servers.
Going Wireless
Wireless devices attach to wireless access points (WAPs). You should encrypt wireless access networks and consider establishing a separate VLAN for wireless devices. Information on encryption and other wireless security issues is available at Wireless Access Controls. For more information about wireless points and routers, see Wireless N Buyer’s Guide to Choosing a Router.
Finally, the best approach to preventing network infection is to block bad stuff at the perimeter. Standard routers are not equipped to handle things like email filtering. Products like those from Astaro or hosted services like Postini can help keep email borne malware away from your servers and workstations.
Remote Access Solutions
It’s a given that someone, maybe you, will want to access the network from a remote location. There are several traditional ways to do this. However, in this article I focus on two: VPN and SSL.
VPN, or virtual private network technology, enables an encrypted connection over the Internet. In other words, it allows you to create a private network while using the public Internet as your external connectivity method, as shown in Figure 2.
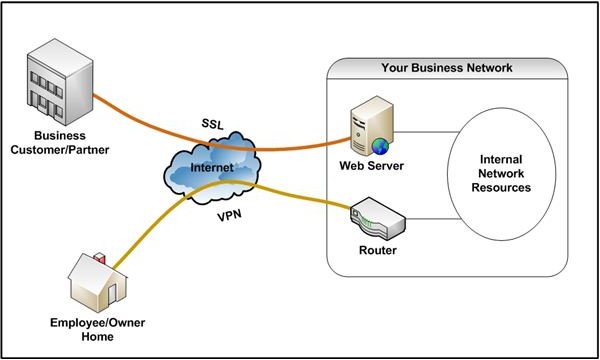
VPN comes in two forms: SSL VPN and IPSec VPN. IPSec VPN is the traditional approach to establishing a secure remote connection. However, it typically requires the installation of an application on the remote system. And when compared to SSL VPN, it provides far less flexibility when configuring access controls. Further, SSL VPN is typically less expensive to implement and manage.
Non-employees, or individuals needing only access to your public VLAN, can connect securely by using the underlying security technology of SSL VPN, secure sockets. The secure sockets layer, or SSL (known as TLS after SSL 3.0), is built into all popular browsers. All you have to do is purchase a certificate from a certificate authority, install it on your Web server, turn on SSL, and you have a secure, encrypted connection. In addition to providing encryption, SSL enables server-remote device authentication, if needed.
In the next section of this SMB security manual, we’ll move from infrastructure design to logical and physical access controls.
This post is part of the series: A Security Manual for Small/Medium Businesses
A how-to manual for implementing reasonable and appropriate security in small/medium business, using clear, non-technical explanations of how to integrate emerging standards (PCI DSS, HIPAA, etc.) into security spending decisions.
- Introduction to SMB Security
- Security Planning: Data ownership and classification
- Security Planning: Data Storage and Sharing
- Security Planning: Regulatory Considerations
- Endpoint hardening and defense: Overview of layered security
- Protecting desktop computers
- Protecting laptop computers
- Choose Encryption Wisely
- Designing Network Security
- Locking Down the Network With Access Controls