Logical/Technical Security Controls - Part 2
Wireless Network Access Controls
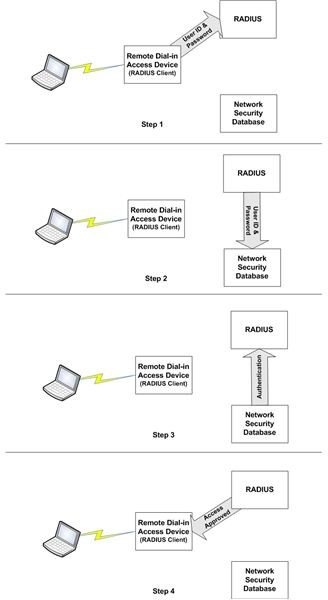
The potential for unauthorized access to your company’s network via wireless access points can be a big risk. In this article, we’ll discuss two controls to help you prevent both remote access and wireless intruders - IEEE 802.1x and RADIUS. Refer to Figure 1 for the following discussion.
802.1x is a standard IEEE protocol that controls who and what connects to the network. When an end user device wants to connect, it communicates with a portal device that serves as a RADIUS client. The RADIUS client blocks the device from connecting and instead requests information with which it can authenticate the device or the user. In our example, the RADIUS client requires the user to enter her user ID and password.
Once the user enters the required information, the RADIUS client sends it, along with an authentication request, to a RADIUS (Remote Authentication Dial In User Service) server. The RADIUS server uses the Network Security Database (Active Directory in the case of a Windows environment) to authenticate the user ID and password. If authentication is successful, the RADIUS client “opens the door to the network,” allowing the end user device to connect and the user to access authorized resources.
The 802.1x and RADIUS solution is effective for both remote and wireless access control. In a wireless network, the RADIUS client is typically the wireless access point.
This process is a good way to keep unauthorized users off the network. But what about those drive-by hackers sitting in your parking lot capturing sensitive data as it’s transmitted from the end user device to the access point. There are two ways to deal with this problem.
Figure 2 depicts the first - encrypting the data as it moves back and forth between the end user device and the access point. Note that the data is encrypted only between the access point and the end user device. The two most commonly used wireless encryption standards are the Wired Equivalency Protocol (WEP) and Wi-FI Protected Access (WPA).
WEP is the original wireless encryption algorithm. It’s supported in both static and dynamic modes. In static mode, the key used by the access point and the end user device doesn’t change. This presents a big opportunity for the hacker in your parking lot. Using any one of a number of free tools downloadable from the Internet, he can crack the encryption and obtain your WEP key in less than 60 seconds. One of the reasons for the low work factor is a weakness in the WEP encryption algorithm.
In a dynamic WEP implementation, you can set the AP to automatically change the key on a regular cycle. By making the cycle time short enough, you can increase the hacker’s work factor to the point where he might pack up and move to the parking lot down the street.
WPA doesn’t suffer from the weaknesses of WEP. It ships with newer APs. In addition to supporting stronger encryption, WPA also uses the Temporal Key Integrity Protocol (TKIP) to change the key with each packet sent. This makes the packets much harder to crack. But there’s a catch. The stronger encryption and the use of TKIP stress a system’s processor and NIC. Performance may suffer. If you plan to use WPA, ensure your systems are robust enough to handle the additional processing load.
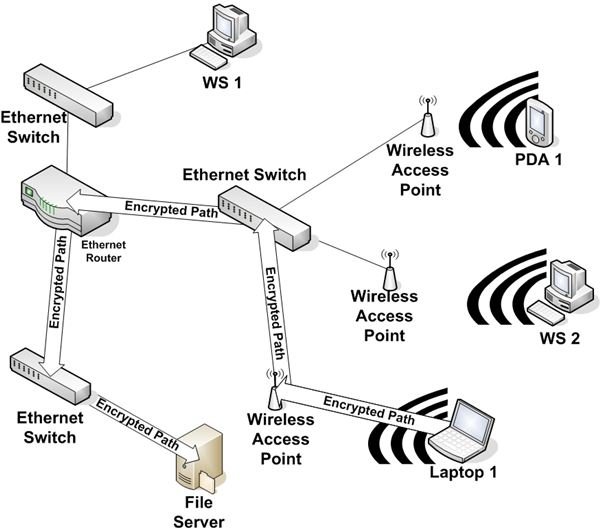
The second solution for wireless eavesdropping defense is VPN. Figure 3 shows an example of a wireless network implemented with IPSec VPN. A VPN tunnel is built between the wireless end user device and a device on the internal network. In our example, it’s a file server. In most cases, the VPN termination point inside your network will be a router, a firewall, or a VPN concentrator.
The big difference between AP encryption and a VPN is the portion of the data path over which the data is encrypted. In a VPN, the data is encrypted between the end user device and an internal VPN termination point. This is a good solution for highly sensitive data or if you are unable to implement something stronger that static WEP.
Another issue associated with wireless networks is the possible presence of rogue APs. A rogue AP is a device installed in your network without your knowledge or consent. One of your employees may install an AP to facilitate wireless access in a lab or conference room. If the AP conforms to your security policies, including encryption, this might not be so bad. But most rogue APs are simply plugged into an available network jack with no protection at all, creating a gaping hole in your wireless perimeter.
A worse scenario involves the intruder who surreptitiously enters your building, locates an unused but active network jack, and plugs in her own AP. If she hides the AP well, you may never know your perimeter has been compromised. So what can you do?
There are two solutions to this challenge. First, ensure that all unused network jacks are either disconnected from the network or are connected to an unused VLAN. Anyone connecting to the jack won’t have access to any other devices. Second, implement a software solution that identifies the presence of rogue APs. Make sure employees understand your policies pertaining to APs and the consequences of not adhering to them.
Another consideration for minimizing wireless access threats is attempting to hide from the outside world the presence of your APs. This can be done in three ways. The first method is to prevent your APs from broadcasting your wireless network SSID (Service Set Identifier), an identifier assigned to each wireless network. By default, the SSID is broadcast in the clear to make it easier for authorized wireless end user devices to locate and use wireless service. But this provides an intruder with a beacon guiding him to your network. Although blocking the SSID broadcast is often touted as a “best practice”, it does not prevent someone from capturing the SSID as it passes unencrypted between the access point and an authorized end user device during the initial connection process. Consequently, SSID hiding has limited value and should not be considered a strong security control.
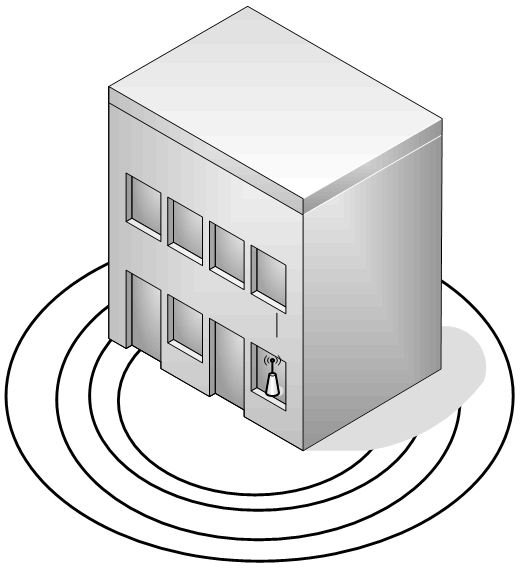
Second, consider turning down the power on your AP radios. Only use the power necessary. Also, place your APs to minimize the portion of the effective coverage area that extends beyond your building. Figure 4 shows how NOT to position an AP. Setting it in the window maximizes the extent to which the AP can communicate outside. A better location would be in the ceiling near an inside wall.
In some cases, you might not be able to reduce radio power or locate the AP in a more secure location because of coverage issues. The third method of hiding your APs, using directional antennas, helps meet these challenges. A directional antenna replaces the standard AP antenna. Once installed, you physically adjust the AP’s coverage area by shifting the direction the antenna is facing. This provides for good coverage where you need it without serving the needs of data thieves in your parking lot.
See the rest of the series…
Tables and Figures (Hover for caption, click to enlarge)

Key Terms
VLAN (Virtual Local Area Network) - A VLAN provides additional flexibility to a network configuration. Using a sophisticated switch, a network administrator can combine several machines that might not be physically located together into a single broadcast domain. In other words, the devices in the same VLAN act as though they were connected to the same wire, even if on separate physical network segments. One advantage of VLANs is the capability to move a machine from one physical location to another while keeping it on the same VLAN.
VPN Concentrator - A VPN concentrator is a device that is designed specifically to help build VPN tunnels.