Endpoint hardening and defense: Overview of layered security
In the previous section of this manual, we stepped through network and data handling planning. In this section, we begin infrastructure design tasks by discussing how to harden end-user devices and servers against attack or inadvertent loss of sensitive information. We start with an overview of layered security.
What is layered security?
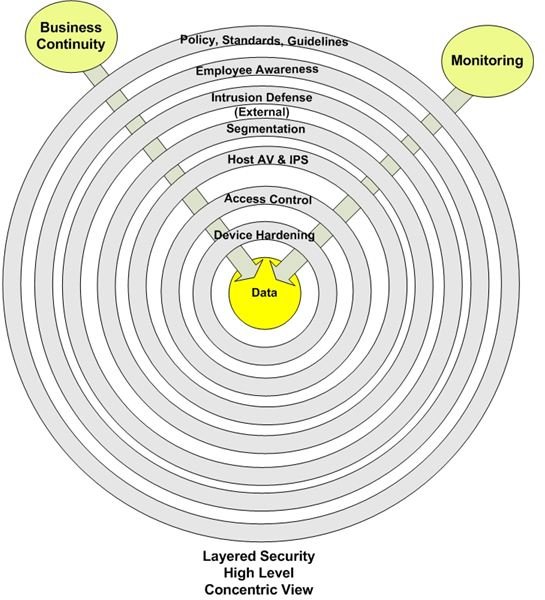
The graphic below represents a layered approach to protecting information. Note the placement of data—right in the center. This is no accident. If you take nothing else from this discussion take this: IT’S ALL ABOUT THE DATA. Everything we do to protect the network and attached devices is intended to address data confidentiality, integrity, and availability.
Surrounding the data are multiple layers of protection. Each layer provides a specific piece of the overall defense, while supporting all the other layers. The objective of this approach is implementation of controls which work to neutralize an attack. An attack attempting to compromise the confidentiality, integrity, or availability of a system must pass through several different obstacles before reaching its target.
These layers consist of administrative, physical and technical safeguards. These safeguards must extend to any device connected to the network.
Let’s take a closer look at each layer.
Policies, Standards, and Guidelines
Policies are business statements of intent, setting the direction for secure information processing and storage. Expanded into standards and guidelines, they build a framework around which a security strategy is built.
Employee Awareness
Well written policies and supporting processes have little value without user awareness and participation. Employees at all levels must understand what is and is not acceptable behavior.
Intrusion Defense
Attacks should be stopped before reaching the target portion of the network. However, this isn’t always going to happen. Intrusion prevention and detection devices, placed at strategic points on the network, are used to detect or stop attacks which sneak through other layers.
Segmentation
Device or system level access controls are a good way to block data compromise. However, it’s better to prevent attacks from getting to critical components in the first place. Network segmentation allows placement of critical systems into isolated network segments. Access controls determine whether specific network traffic is allowed on the segment or blocked.
Host AV and IPS
The layers surrounding systems and individual devices are designed to prevent or detect intrusions. However, no one layer or combination of layers is sufficient to prevent or detect all malicious activity. The final line of defense is the presence of anti-malware and intrusion prevention/detection software on end-user devices and servers. These devices, the final objective of most attacks, must be able to provide some level of self-defense to combat those few exploits that make it through the other layers.
Access Controls
There are three types of access controls: administrative, technical, and physical. Administrative controls consist of policies, standards, and guidelines which govern user behavior. Although often necessary to supplement the other types, administrative controls rely on human behavior; never rely on them as the only method of preventing access.
Technical access controls consist of user accounts, tokens, access control lists, or other mechanisms used to prevent or allow system, application, or user access to information resources. One or more technical controls should be in place to protect confidential information. However, these controls are not fully effective unless supported by physical controls.
Physical access controls prevent intruders from unauthorized access, as defined by policies, standards, and guidelines, which require actual physical contact with a system, including theft or destruction of one or more components of a system, laptop, PDA, etc.
Device Hardening
Device hardening is the most basic controls used to protect data and systems. It consists of the timely application of patches and the careful configuration of system components, removing the most fundamental security vulnerabilities. Supported by a well-designed and actively managed patch management process, proper device configuration is the most effective method of repelling exploits.
Monitoring
Appropriate monitoring tools are used to measure the effectiveness of installed controls. Monitoring requires review of alerts or logs.
Business Continuity
The purpose of business continuity is ensuring uninterrupted delivery of electronic products and services to business users. In essence, its goal is to maintain continuity of technical operations to prevent:
- Degradation in services delivery
- Loss of business to competitors
- Supply chain interruption
- Injury to customers of employees
- Loss of reputation
The final word
In the next post, we expand our understanding of device hardening as we design an endpoint security framework.
This post is part of the series: A Security Manual for Small/Medium Businesses
A how-to manual for implementing reasonable and appropriate security in small/medium business, using clear, non-technical explanations of how to integrate emerging standards (PCI DSS, HIPAA, etc.) into security spending decisions.
- Introduction to SMB Security
- Security Planning: Data ownership and classification
- Security Planning: Data Storage and Sharing
- Security Planning: Regulatory Considerations
- Endpoint hardening and defense: Overview of layered security
- Protecting desktop computers
- Protecting laptop computers
- Choose Encryption Wisely
- Designing Network Security
- Locking Down the Network With Access Controls