Protecting Desktop Computers: How To Protect Your Desktops Against Internal and External Attacks
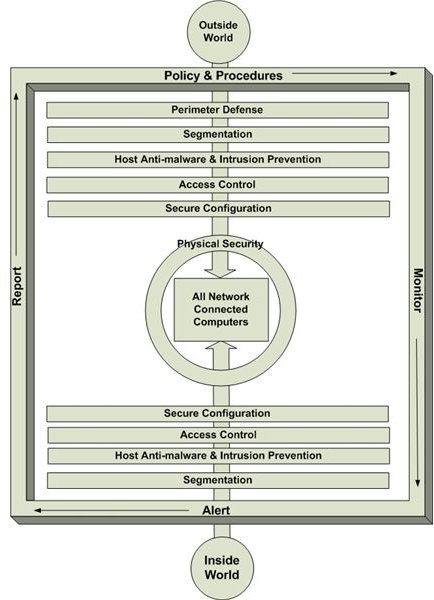
A strong desktop computer defense consists of administrative, technical, and physical controls designed and implemented at various crucial layers. The following graphic depicts these layers and their relationship to each other and to a network-connected desktop system.
We’ll examine segmentation when we look at overall network security. The rest of the layers are discussed below.
Policies and Procedures
The first step in designing desktop computer security is understanding actions employees are or are not allowed to perform on company-owned equipment or with company-owned services. A description actions allowed, prohibited, or allowed under specific conditions is contained in an acceptable use policy. (Download a sample acceptable use policy.)
Employees must be aware of the contents of the acceptable use policy. Ideally, the do’s and don’ts contained within it are included in a documented security awareness training program. Further, fair and consistently applied sanctions for not adhering to security policy should be in place.
Another important set of policies should describe the organization’s approach to configuring and implementing end-user devices. One of these documents should include change and configuration management expectations intended to ensure secure system rollouts with little risk of breaking one or more business processes.
Finally, be sure all policies are supported by documented procedures. It’s the procedures that ensure all desktops are configured and secured consistently, in accordance with management’s expectations.
For more information on policies, see Security Basics - Overview of the Security Program and Security Basics - Components of Security Policies.
Perimeter Defense
Perimeter defense, covered in a subsequent section, begins with network-level controls. Reasonable and appropriate effort should be taken to prevent bad things from the outside getting to your desktop systems. However, no control is perfect. Further, many attacks come from inside the network perimeter. And let’s not forget that your users might invite malware in or leak data out by unknowingly visiting malicious or infected Web sites. For these reasons, building a security perimeter around each end-user device is a good idea.
A desktop security perimeter consists of several components, all working together to detect, alert, and potentially block unwanted system behavior, including:
- Anti-virus and anti-spyware protection as well as intrusion detection, alerting, and prevention (see Host Anti-malware and Intrusion Prevention).
- Personal firewall. A personal firewall prevents unwanted external connections or attempts to install unwanted software. It also stops already infected desktops from connecting with an attacker’s server.
- Employee awareness. Regardless of how many controls you put in place, careless use of desktops will inevitably find a way around your security. A strong security awareness program is a key element of end-user defense.
- Secure configuration policies and processes (see relevant topic later in this section).
- Appropriate access (see Access Controls and Physical Security)
In essence, all the layers identified in the opening graphic work together to provide a tight perimeter around desktop computers.
Host Anti-malware and Intrustion Prevention
Desktop monitoring and alerting include a number of activities, including scanning for malware, spyware, and malicious attacks. There are a number of solutions on the market today which provide this layer of protection, including McAfee’s Total Protection Service. TPS is a software-as-a-service (SAAS) offering providing the following features:
- Updated and managed by vendor
- Proactive scanning of applications and other files to prevent them from executing or being stored on the desktop (intrusiton prevention)
- Integrated firewall
- Protection against visiting malicious or questionable Web sites
- Email scanning/filtering to stop spam, phishing, etc.
- Central management and monitoring
If you prefer to host the solution in-house, SkyRecon’s StormShield suite is worth a look.
No matter what vendors may tell you, no anti-virus or intrusion prevention solution is perfect. When they occasionally fail to prevent compromise of one or more systems, the best recovery method is to wipe the hard drive and start over. Products like Acronis True Image enable creation of system images, incremental backups of user-created data, and centralized management of backup activities. If you’d rather not manage backup systems yourself, online backup services exist. For example, Mozy performs regular backups to a vendor-hosted server. Users can easily retrieve lost or damaged files.
Access Control
Access control takes two forms: physical and logical. The purpose of physical security is to deny an intruder easy physical access to critical infrastructure or sensitive data. Note I didn’t say prevent. A determined intruder will find a way around fences, motion sensors, locks, etc. The intent of a good physical security design is to raise the level of effort needed to reach a target higher than the target’s value. If that isn’t reasonable or appropriate, then the controls should detect and delay intrusion so the intruder can be apprehended.
Unless all sensitive information on a physically compromised system is encrypted, a skilled intruder who can actually put his or her hands on the device will get your data. For more information on physical security planning and design, see Overview of Physical Security.
Logical access control limits who or what (the subject) can access an information asset (the object). A subject can be a person, an application, a process, etc. For desktop systems, the most important control is taking local administrator control away from your users. Employees logging on to their computers with full access are conduits through which attackers can install malware, retrieve sensitive information, or simply take control of one or more desktops for later use (i.e., enlist them in a botnet). So never leave the local administrator account password blank, give the account a strong password, and let only a limited number of support staff know what it is.
We’ll look at logical controls in more detail when we discuss overall network access.
Secure Configuration
Possibly the most important desktop security control is proper configuration and patching of desktop operating systems and applications. Most attacks take advantage of weaknesses caused by configuration misses or errors in programming. Vulnerabilities from both can be managed, even though preventing them increasingly looks impossible.
In general, make sure you understand what your operating system vendor considers a secure desktop OS config. This includes service settings, open ports, etc. Further, keep your eye on announcements from all your desktop software vendors about patches or workarounds for known vulnerabilities in their products. Applying patches as they’re released can be a time-consuming process, but it is one of the best ways to deny attackers pathways into your systems and your network.
For detailed information about this control layer, see Intrusion Defense - Part 2.
The final word
SMB network administrators often focus on servers, firewalls, and other network components when they plan for security. These are all important. However, desktop systems can be your biggest vulnerability and present the largest risk. One or more compromised desktops can act as a launching site for attacks against other areas of your network. They can be used to collect passwords, account IDs, and other sensitive information stored on or passing through employee computers. Make sure you don’t forget them when working on your information security budget.
This post is part of the series: A Security Manual for Small/Medium Businesses
A how-to manual for implementing reasonable and appropriate security in small/medium business, using clear, non-technical explanations of how to integrate emerging standards (PCI DSS, HIPAA, etc.) into security spending decisions.
- Introduction to SMB Security
- Security Planning: Data ownership and classification
- Security Planning: Data Storage and Sharing
- Security Planning: Regulatory Considerations
- Endpoint hardening and defense: Overview of layered security
- Protecting desktop computers
- Protecting laptop computers
- Choose Encryption Wisely
- Designing Network Security
- Locking Down the Network With Access Controls