Sysinternals Process Explorer - Manage, Monitor and Kill Windows Processes
The Challenge
Today’s Microsoft Windows-based systems are relatively easy to monitor using tools provided out-of-the box with Windows. However, when a security issue arises, which requires knowledge beyond which wizard to bring up, we often have to resort to process analysis. In some circumstances, we might have to work backward, from registry keys or DLLs to processes that created or use them. Without the right tools, this is a daunting task.
Task Manager, a free utility provided with Windows, is not intended for serious process analysis. It can get you started, but dependencies and other critical information are not available. However, you don’t have to spend your entire security budget for the right tool. Microsoft’s Sysinternals Process Explorer is a great way to achieve process visibility–and it’s free.
Process Explorer
Process Explorer has the same functionality as Task Manager and a lot more.
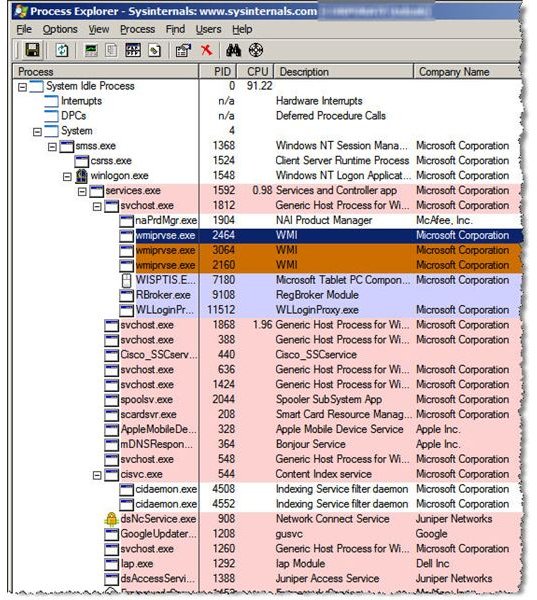
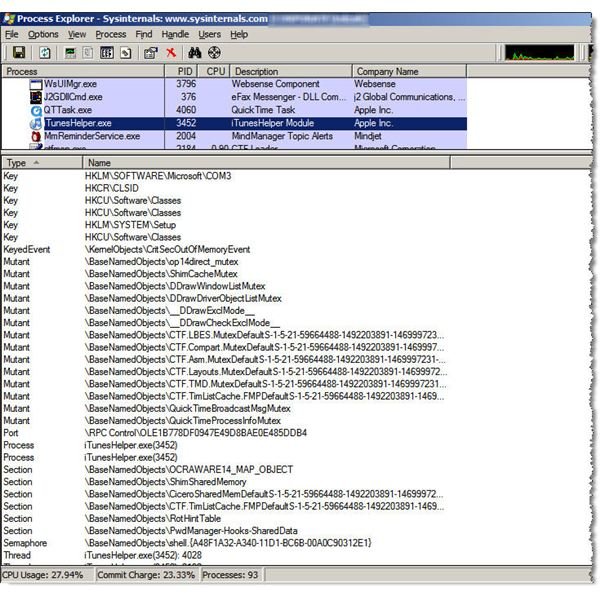
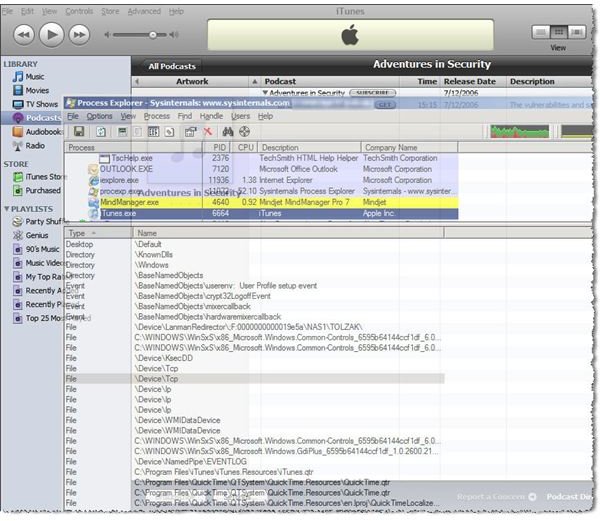
Installing Process Explorer is easy. Just download, extract it from .ZIP format, and your ready to go. Double-clicking on the executable brings up the windows shown in Figure 1. Choosing to display a bottom pane provides additional information on a process when you click in the main display. As you can see in Figure 2, the lower pane provides detailed information about system use of the iTunes process, including:
- Threads
- Registry keys
- Ports
- Events
- Files
- Directories
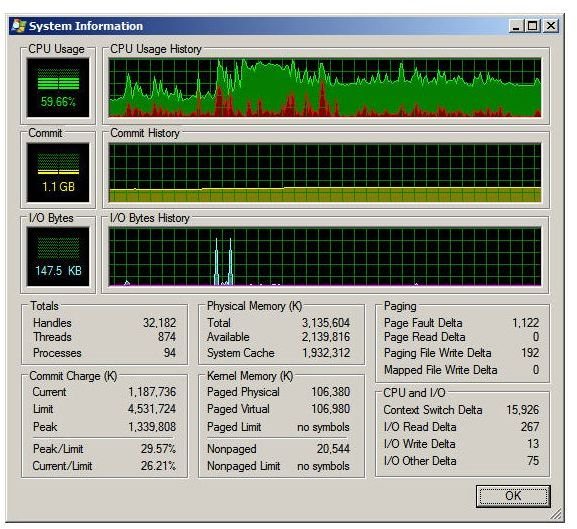
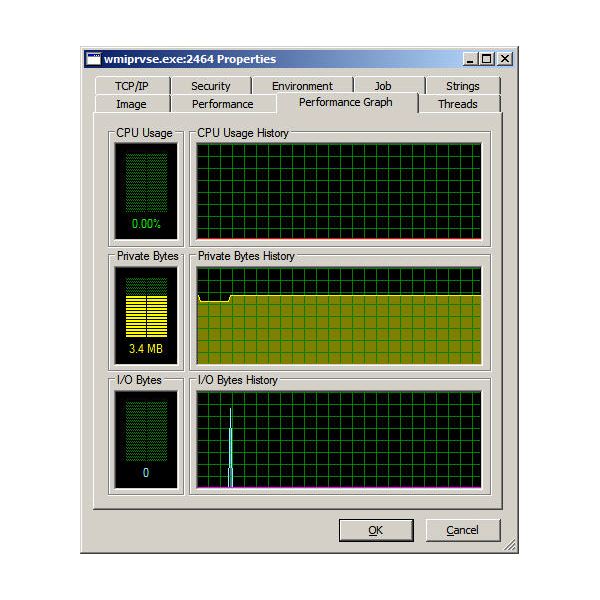
If you need overall system information, as shown in the Performance tab of Task Manager, Process Manager provides that too–with a little more information. See Figure 3.
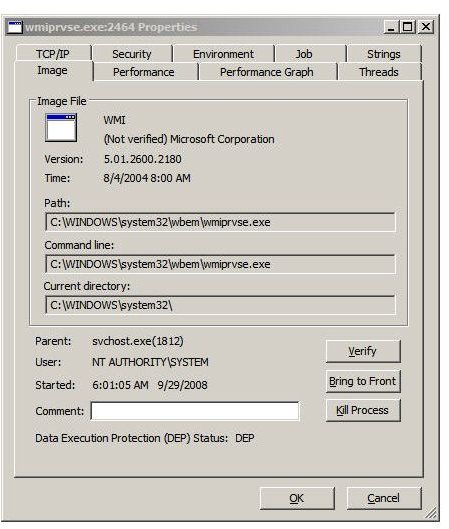
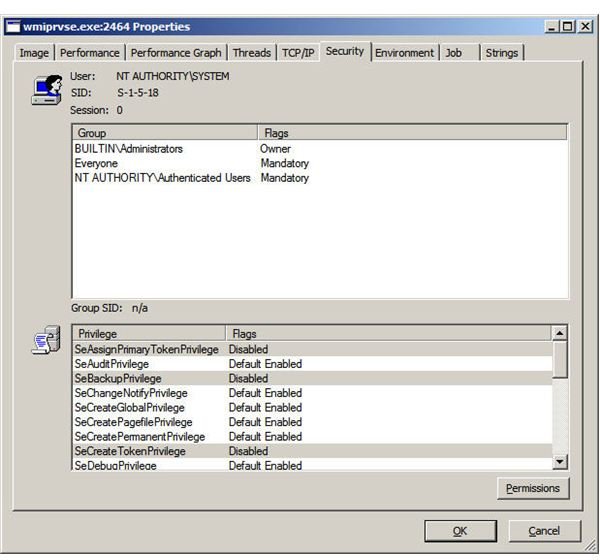
While a single click on a process refreshes the lower pane, double clicking brings up a more organized, tabbed window. Figures 4 through 6 are examples of information available unique to the target process, including security attributes.
There is another feature that might be useful when performing real-time analysis with a single display–the opaqueness setting. You can configure Process Explorer for various levels of transparency, providing a view of the running program. An example is shown in Figure 7. Apple iTunes is running in the window without focus, but is visible through the Process Explorer window I’m actively using to monitor system and process activity.
The Final Word
This is a great utility for analyzing processes running on a Windows platform. There is also a toolbar function which allows you to replace Task Manager with Process Explorer. I don’t use all the Sysinternals utilities, but this one I’ll keep.
Tables and Figures (Hover for caption, click to enlarge)
This post is part of the series: Use SysInternals security utilities to manage network and system security
SysInternals provides free security utilities for managing Microsoft Windows networks and systems. Available for download from Microsoft, they provide a powerful set of applications for oversight and protection of network assets.
- Validate System Access with AccessChk
- Streamline Kiosk Operation with Auto-logon
- Enumerate Windows File and Folder Access with AccessEnum
- LogonSessions and PsLoggedOn to Oversee and Manage System Access
- Use Autoruns to Improve Performance and Identify Malware
- Manage, Monitor, and Kill Windows Processes with Process Explorer
- PSExec: Free Security Testing and System Management Tool
- PsLogList: Free Utility to Parse and Review Windows Logs
- Map System Configs with PsInfo
- Use SigCheck to Validate System Files