Information Security Primer - Part 3
Integrity
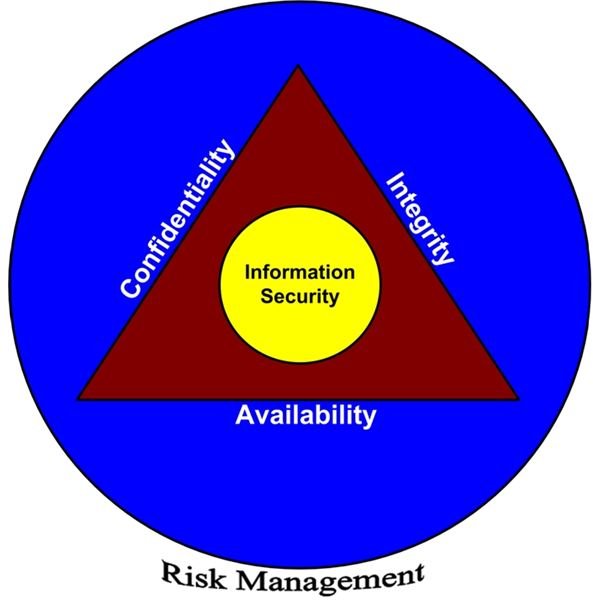
Integrity is the second of the three objectives of information security. All three, and their relationship to security and to risk management, are depicted in Figure 1.
Protecting information integrity goes beyond preventing unauthorized viewing. It requires the implementation of policies, processes, and technology that prevent or detect the unauthorized modification of data. Threats against integrity are similar to those that may compromise confidentiality. But there are additional steps managers can take to ensure data is not changed without proper authorization.
- Enforce Least Privilege - Users should have change access only where necessary to perform their day-to-day tasks.
- Separation of Duties - No single employee should be able to perform all tasks associated with a single transaction. For example, an employee in Payroll shouldn’t be able to:
- Create an employee account
- Enter a manual payroll check
- Approve the manual payroll check
- Pick up the check for the named employeeAny one of the first three tasks moved to another employee will significantly reduce the risk of fraud. Separation of duties is based on the belief that the probability of two or more employees colluding to perform an unauthorized act is much less than a single employee performing the same act alone.
- Rotation of Duties - One of the best ways to prevent or detect unauthorized changes to data is rotating employees through different roles. If an employee knows someone else will have access to the work she’s done, she’ll be less likely to perform an unauthorized or illegal act.
- Application-only Data Access - User access to data should be restricted to application interfaces. Direct database access should be allowed only for those directly responsible for database health, such as database administrators. Even then, managers should implement controls that monitor database management activities.
Availability
Protecting the confidentiality and integrity of information is important. But a business can’t operate unless its employees can access that information. The concept of availability addresses the ability of users to access information when and where they need it. There are two primary availability concerns when implementing information security in your organization: denial of service (DoS) and business continuity.
-
Denial of Service – DoS is typically caused by the actions of humans or software. In DoS, the attack agent uses all available processing resources. Authorized users are unable to access or process business information. Controls to prevent or detect DoS attacks include:
- Application of critical security patches
- Implementation of firewalls that drop all packets except those intended for verified and authorized connections with internal resources.
- Implementation of intrusion prevention/detection services
-
Business Continuity - Business Continuity is concerned with natural and man-made events that may result in the loss of processing capabilities. Included are earthquakes, fire, floods, terrorist attacks, strikes, chemical spills, hardware or software failure, etc. Business continuity events can range from a failed hard drive to the destruction of the data center. Some of the actions you can take to mitigate their effects include:
- Development and testing of a Disaster Recovery Plan to restore services after a catastrophic event
- Installation of fire detection and suppression systems designed to protect electronic equipment
- Implementation of fault-tolerant hardware systems that allow the processing of data in the event of a hardware failure
- Implementation and enforcement of a Change Management Process to ensure changes are made to production systems while mitigating the risk of accidental system failure
- Performing regular backups of data with off-site storage for backup media
- Implementation of physical and logical controls to prevent unauthorized access that might lead to disruption of processing
- Development and testing of an Incident Management Process, enabling rapid service recovery when a business continuity event occurs
Risk management, the governing principle that ties together all the elements of information security, is the topic of Part 4.
Read or review all the articles in this series…
Figures (Hover for caption, click to enlarge)
This post is part of the series: Information Security Primer
This series introduces those new to information security to the basics. It is a good start for entry-level security professionals or those who need to know a little more about the subject.