Information Security Primer - Part 2
Information Security
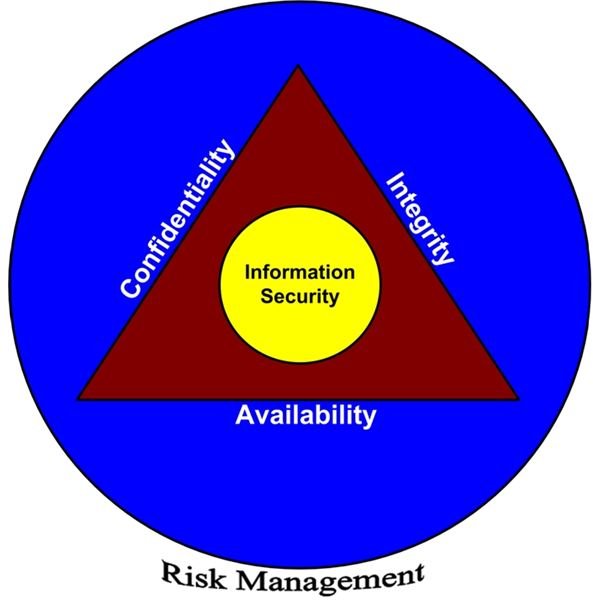
Put simply, the proper application of information security ensures the confidentiality, integrity, and availability of information assets, in a reasonable and appropriate manner, through the proper application of risk management. Figure 1 depicts the relationship of these elements.
Confidentiality
Confidentiality is the protection of information from unauthorized access by people, processes, or systems. Examples include access by employees who do not require the information to perform their daily tasks and access by non-employees for either malicious or non-malicious purposes.
An organization’s information can usually be divided into that which the world can see and that which only employees can see. Employee viewed information should be further classified so that a “need-to-know” approach is effectively applied. Security design in both processes and systems must include access controls with sufficient granularity to accommodate and restrict access to multiple information classification levels.
It isn’t necessary to complicate information classification. I like to use three classification levels: critical, confidential, and public. Critical information includes documented intellectual property and information governed by regulations such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the Sarbanes-Oxley Act of 2002 (SOX). All other business information is included in the confidential category, unless specifically marked as public.
There are many threats to confidentiality. The following list includes some of the most common ways information is compromised as well as ways to protect your business:
- Unprotected Downloaded/Uploaded Files - Information is stored in environments with controls commensurate with its classification level. This information may be moved or copied to another server or network. When this happens, the security controls of the new environment should be equal to or greater than the original environment.
- Crackers - A cracker is someone who bypasses an organization’s security controls for the purpose of personal gain, revenge, or some other malicious intent. Strong layered prevention and detection controls must be in place to help defend against this type of attack.
- Unauthorized User Activity - Users with authorized access may intentionally or unintentionally browse sensitive information, information they don’t need to perform their daily tasks. Access controls tuned to information classification levels and employee roles help to protect against this type of threat.
- Social Engineering - Social engineering is one of the most serious threats to an organization. Managers can spend millions on sophisticated prevention and detection mechanisms only to have an unauthorized person obtain access to sensitive information through a simple telephone conversation or email exchange. The social engineer uses deception to obtain sensitive information directly from an unsuspecting employee. A manager can do two things to help protect against this type of threat. First, ensure need-to-know is built into every access control. This limits the information any one employee can potentially compromise. Second, train your employees to properly handle requests for information. Security awareness training is your most effective defense against social engineering.
- Trojan Horses - A trojan horse is a type of malware that looks and acts like a normal application. A user might download it from the Internet as part of an application installation. However, a trojan will also perform some malicious activity. It might allow an unauthorized user to gain access to your network, or it might automatically copy files, over the Internet, to an attacker’s storage device. The best defense against trojans is to restrict the installation of software to only authorized personnel. Management should implement this defense through the combination of policies, processes, and technology. Another critical defense is the use of anti-virus software. Under no circumstances should a system connect to a business network that is not running an updated anti-virus program.
- Spyware - Spyware is a relatively new threat. It’s normally downloaded, without user request, from Internet sites visited by users. Some spyware is installed without malicious intent. Other spyware may be installed to collect sensitive information and send it to an attacker’s location. In any case, spyware will affect the performance of the system on which it’s installed. The safest approach is to eradicate spyware wherever it’s found on your network. You should also take steps to prevent its installation. Prevention steps include implementation of anti-spyware appliances at the entry points to your network from the Internet, the use of host intrusion prevention systems, or the implementation of anti-virus products that incorporate the identification and eradication of spyware.
- Masquerading - Masquerading is the use of an authorized user’s ID and password by an unauthorized user to gain access to a network. Protecting passwords as well as employee security awareness training, focused on protecting network access information, are a good start in thwarting this threat.
See other articles in this series…
Figures (Hover for caption, click to enlarge)
Key Terms
Malware - Malware is short for Malicious Software. Malware includes viruses, trojans, worms, and any other software deployed with malicious intent.
Host Intrusion Prevention System (HIPS) - A HIPS is installed on a server, desktop, or laptop system. It may be configured to prevent certain actions from being performed or to report suspicious activities. Blocked actions include copying or moving files, deleting files, installing applications, etc. Any attempt to perform one of the restricted activities may result in a log entry or system administrator alert.
This post is part of the series: Information Security Primer
This series introduces those new to information security to the basics. It is a good start for entry-level security professionals or those who need to know a little more about the subject.