Biometrics in IT Security: Questions, Options and Solutions
Taking a Closer Look at Biometrics
Biometrics is a science based on human identification. There are biometric devices (see the section on biometric devices) that can identify and distinguish people. They use an authentication technique that determines who a user is by taking into account a person’s body or behavior uniqueness. Biometric devices are considered by many IT security experts to be the one technology that works best (i.e., it’s effective, reliable, and accurate) for secure authentication.
“Biometric technologies are [today] the foundation of an extensive array of highly secure identification and personal verification solutions.” [1] Nowadays, many organizations are utilizing biometrics to help protect their information and assets. In addition, they are placed in secured areas and to access computers or networks.
In order for a biometric device to work, it requires two stages: enrollment and authentication. As for enrollment, users will need to have their biometric data collected through the device. This will record distinctive characteristics of the user. The users’ data is encoded and stored for later use in the form of a template that will be setup to link to the user’s identity. The authentication process, instead, involves either identifying or verifying the user. By identification, a biometric device will compare the data of the user to many stored in the database. Verification will indicate whether a person is who he or she claims to be.
Biometrics in IT Security
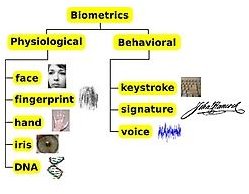
Biometrics helps provide physical and network security by providing authentication, encryption and access control. It eliminates the need of using a username or an account ID. Biometric devices are used to recognize physiological and behavioral characteristics of a person to help protect information resources from outsiders and to block access to unauthorized personnel. They can use a print, an image, or the voice of a user.
In short, biometrics in IT security is a two-step process: Identification and authentication. It requires both in order for a user to be able to gain access to a system or area.
Biometrics is an ideal solution for any organization requiring IT security. Not all biometric devices are needed or necessary, but system administrators can choose between many different types to find the most suitable to the environment they need to secure.
For businesses interested in using biometrics, here are a few biometric solutions…
Precise Biometric Smartcard Readers
Biometric Employee Time Tracking Software
Biometric Devices
There are many biometric devices that exist (as shown below in the image section). The biometric devices most often used today are those that can examine fingerprints, facial characteristics, and iris patterns.
What’s unique about biometric devices is that they draw on patterns and measurements (characteristics that are unique to users) for authentication. Although the chacteristics examined may appear different from each other, they work similarly to record distinctive biometric characteristics of a user so they can either be identified or verified.
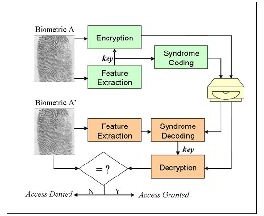
As an IT security tool, fingerprinting remains the most popular biometric authentication device. It is fairly secure (i.e., it is hard to replicate or share), yet it is an easy-to-operate method to gain instant access to a PC or area. For an idea on how fingerprinting works, see the illustration in the image section below.
Of all the biometric devices used today, the Iris scanner is said to be the most accurate and secure since it is not subject to users’ physical changes.
Source & Useful Web Sites
Source:
[1] NIST (About Biometrics): https://www.itl.nist.gov/div893/biometrics/about.html
Useful Web Sites:
The Biometric Consortium (Research Database): https://www.biometrics.org/research.php
Biometrics Glossary: https://www.biometrics.gov/Documents/glossary.pdf
Types of Biometrics: Physical and Behavioral (Image Credits by MIS Biometrics). Also shown ~ The Process of Securing Biometrics: Fingerprint Authentication, Encryption and Access Control (Image Credits by MERL)
Related Articles
Biometric Technology and Privacy Issues
How Biometric Recognition Works
10 High Tech Spy Devices (biometrics in daily life)
This post is part of the series: Using Biometrics
Are you aware that biometric devices can identify an authorized user from one that is not? Well, they can… Each device is different, but they do have one thing in common: Biometrics considers users’ physical and behavior traits to verify their identities.