Cybercrime Prevention & Tools: How to Protect Against Cybercrime, Phishing and Identity Theft
Introduction to Cybercrime
Indeed, cybercrime has come a long way since the early days of 419 scams and poorly masked attempts at phishing for sensitive and personal information, or implanting email worms to distribute spam emails. As technology and the software which powers it has grown over the years, so too have cybercriminals’ methods.
Cybercrime takes on many guises, from online bullying through social networking sites such as Facebook to phishing attacks for personal information, the planting of viruses or malware, downloading copyrighted materials or even money laundering. In fact, the list of potential cybercrime offences is exhaustive, taking in a wide range of nefarious deeds.
However, the average PC user won’t be exposed to some of the darkest facets of cybercrime. They will, however, have to tread warily around certain areas where there is a likelihood they will come into contact with some dodgy Internet practices.
Any PC that is attached to the Internet is a potential target for cybercriminals, but with some common sense and the use of some free or inexpensive software, the average PC user should be able to minimise their risk of falling prey to cybercriminals and surf the Internet safely and enjoyably.
In this article, we’ll share some handy precautions and cybercrime tools and protections which can help make your Internet experience just a little bit safer.
Phishing Scams
Phishing scams are perhaps the most common type of cybercrime the average PC user is likely to encounter.
Typically, phishing scams are delivered via email to a user’s inbox – usually masquerading as a bank or other financial service under the pretence that they are undertaking random security checks or have detected suspicious activity on the user’s account. In order to safeguard the integrity of the user’s account, the email suggest that the user click a link contained in the email to be redirected to the log-in page of the bank where they can log in and change their password.
In fact, the user will be taken to a dummy-page designed to mimic the real log-in page of the financial institution, and an unsuspecting user providing their details through this page will be giving cybercriminals full and unrestricted access to their accounts.
Often, cybercriminals won’t empty the user’s account straight away. Instead, they will siphon off a small amount at regular intervals, which is less likely to be flagged by the user or bank.
-
Be suspicious of any email that is not addressed to you personally; for example, if it begins ‘Dear valued customer’ or ‘Dear bank user’. Also, if the email is addressed to multiple recipients, it might not be all that it appears.
-
Never click a link in an unsolicited email, or indeed even an email from a known source. Instead, type the URL of the link into a web browser yourself as cybercriminals can mask and redirect URLs to their own websites. They will often exploit simple spelling mistakes, domain names and extensions to host bogus sites.
-
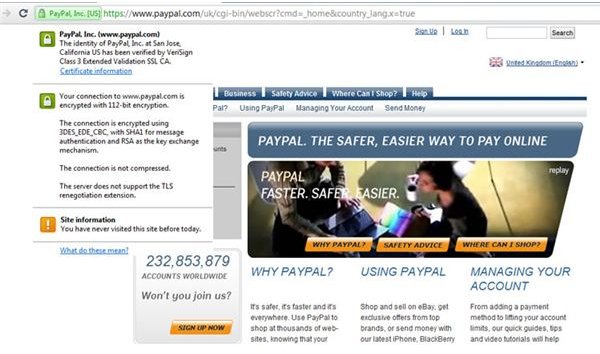
Check that the site you have landed on is secure, and if not, don’t enter any personal information into a form. Check that the URL reads https:// (not https://) – the ‘s’ lets you know you have reached a secure server.
-
Legitimate financial websites will have a security license which you can view. Depending on your browser, this method of viewing may operate in a different way, and display differently.
-
Keep a keen eye on bank and credit card statements for any unrecognised transactions. Also, keep in mind that a legitimate bank WILL NOT email you and ask that you provide your private data for any purpose.
-
Most reputable Internet security platforms now provide some protection from phishing attempts. Internet security products from the likes of Norton, BitDefender and Kaspersky have built-in phishing protection which can warn users when they are about to enter a bogus website. Some free solutions may also provide anti-phishing protection, so consider making a switch if yours doesn’t provide this.
-
If you’d rather not change from your existing anti-virus solution, consider installing an anti-phishing toolbar, such as the Netcraft toolbar, which can warn against visiting potential phishing websites, provide risk ratings for websites that users visit and detail factors such as the setup date of the website, its global location and its webhost.
-
Other useful toolbars include Reasonable’s Anti-Phishing toolbar, while GralicWrap is a desktop application which sits between your PC and web-browser to detect phishing attempts.
-
Web browsers are also beginning to include rudimentary anti-phishing measures into their releases, so it is always worthwhile to ensure you are running the latest version of your preferred browser.
Dealing with Spam Emails

Spam is a constant battle for most email users, but one which ISPs and Internet security is slowly beginning to win.
Spam is typically used to advertise goods and services, and is sent out in large volumes. Spammers make money by selling their wares to those who respond, or in the case of 419 emails, swindle the user out of money with the promise of a huge cut of non-existent cash.
Most ISPs have adopted spam-filters which prevent a large amount of spam from reaching your inbox, although it is still much more of a problem with free email services, such as Hotmail, Yahoo! and Gmail.
While most spam emails are simply details of unwanted drugs and other goods, some carry potential threats to your PC’s security in the form of attachments or links to websites. Both methods will typically result in a user’s PC being infected by a Trojan, which can be used by hackers to further spread spam emails, or a keylogger, which sends information to the hacker about a user’s keypresses – including sensitive passwords.
The common sense approach to dealing with spam is in most ways the same as it is for dealing with phishing attempts. Avoid clicking on links or attachments contained in unsolicited emails.
Other common sense tips to employ include:
-
Don’t respond to, or click the ‘unsubscribe’ link in emails. These confirm to spammers that your email address is active, and so you’ll increase your likelihood of receiving even more spam.
-
Use multiple email addresses, keeping one email for personal correspondence. Use others for more public use, such as forum participation, online shopping and mailing lists. Consider spending a little money on a dedicated email service, or cheap web host – even if you don’t plan to ever build or host a website. You’ll get added anti-spam protection from the webhost, as well as the ability to create multiple email accounts for different purposes.
-
Avoid using your private email address and make it difficult to guess. Spammers use combinations of obvious names, words and numbers to create possible email addresses. By making it hard to guess, it becomes more difficult for spammers to replicate your email address.
-
If you must use your private email address, type it in a fashion that can’t easily be read by automated email harvesting tools. For example, write john-dot-doe-AT-mydomain-dot-com, rather than the actual email form.
In most cases, a user’s ISP and internet security solution make a pretty decent go of keeping their mailbox relatively free of spam. However, there are additional tools that can also help.
-
POPFile, for example, is a powerful email proxy solution that can be used to filter and categorize spam and genuine emails.
-
Mailwasher Pro uses multiple methods to determine spam emails from legitimate emails and can prevent a user’s email client from downloading spam emails to their PC. All email can be previewed prior to downloading, so the user saves time and bandwidth by only downloading genuine emails.
-
Spambully is another anti-spam tool which, like Mailwasher Pro, uses multiple methods to determine and categorise what is spam. It integrates well with Outlook and Windows Mail, but doesn’t support IMAP protocol.
Dealing with Malware and Viruses
Malware and viruses can happen at any time, and a user can become infected simply by visiting a malware-infected website, downloading an infected file or by using an infected data storage device.
Malware and viruses can be targeted to do many things, including stealing personal data, corrupting data, taking control of a user’s PC for the purpose of sending out spam or forming part of a botnet.
The most common sense approach any PC user should take is to install a reputable anti-virus solution. There are both free solutions (eg: Avast!, AVG, Avira) and paid solutions (eg: BitDefender, Kaspersky, Norton, Nod32 among others), and whichever one is chosen the user should take steps to ensure it updates regularly and that regular scans are run.
In addition to anti-virus and Internet security suites, using stand-alone anti-malware products can help safeguard against malware and viruses. Like anti-virus, there are both free and paid-for solutions, such as Lavasoft’s Ad-Aware, Malwarebytes, Emsisoft’s A-Squared and Webroot’s SpySweeper. Again, these should be kept regularly updated, with regular scheduled scans.
Consider using a software firewall to limit which software programs have access to the Internet. Like anti-virus and anti-malware solutions, there are free and paid services available. If you choose to use an Internet security suite, it will probably come with a firewall program. Some free firewalls options are Comodo Personal Firewall, PC Tools Firewall, ZoneAlarm and Agnitum.
Users should also ensure their operating system is fully patched with the latest security updates, in order to close points of exploit for potential hackers.
For operating systems where user policies can be defined, users should make a separate account on their PC for everyday use. This will limit the effectiveness of any malicious program that does make it through onto a user’s PC by denying it access to valuable system data and resources. Only use the administrator account when installing software
Make regular backups of system data to a CD, DVD or external hard-drive or pen-drive. That way, if a user does become infected, you’ll have clean copies in safe storage.
And, as with spam emails, avoid opening attachments in emails or clicking on suspicious links.
The Importance of Passwords
A weak password can be easily guessed, and many people automatically set passwords on sensitive accounts that could be guessed through information they make freely available, such as the names of their children, pets or favourite place.
The more personal details a user shares on social networking sites, such as Facebook, can give a hacker another clue to the user’s password for a host of services, so it is important to ensure they are as strong as they can be.
Many peoples’ primary concern regarding passwords is that they might be forgotten, but passwords should be changed regularly and shouldn’t be easily guessed. By all means, make passwords memorable, but consider substituting letters for numbers, such as using ‘5’ instead of ‘s’ or ‘8’ instead of ‘B’.
-
Use a mixture of lowercase, uppercase and numbers in the password, and don’t store them in a file on your computer. If you have to write them down, do so in a notebook and keep it safe.
-
Don’t tell anyone your password. Never, ever share personal data online or over the phone, unless you are absolutely sure of who you are dealing with. Just because they say they are with ‘XYZ bank’ doesn’t mean they are!
-
Use different passwords for different accounts. If a hacker discovers one password, they will use it on other accounts you might have. Also, don’t recycle passwords – make each one unique.
Useful Resources
In addition to the wealth of information surrounding Internet security and cybercrime on Brighthub, there are many resources available elsewhere online which can help to further explain methods of staying safe online and also provide tools to safeguard against cybercrime.
Some useful resources to help inform users about cybercrime are:
Softwin, the company behind BitDefender also commissioned TV personality and mathematician Johnny Ball to host a series of short videos explaining ways which PC users can help themselves stay safe by explaining some of the more dizzying terms and jargon surrounding Internet safety.
Entitled ‘Web without worries’, the videos are available to view here.