Forewarned Is Forearmed: Hacking Tools and Techniques
Know Your Hacker
Forget the old stereotype of the lone misanthropic geek wreaking havoc on the world from a basement lair. While certain lone
hacking ‘’exploits’’ still do occur, more often than not it is to build a coder’s reputation, which they can then convert into an $80,000 a year job as ‘‘White Hat’’ IT security consultants. The theory is that a coder hacks into a bank, calls the bank the next day, and tells them how he got in, and then asks for a ‘‘consulting fee’’ for revealing the security hole. A bit tricky, but then again, how else would someone of the hacking persuasion get into the corporate world? Many ethical hackers choose to remain as freelancers (why get dressed for work when you can expose security loopholes from home in your underpants?), making a living off the money companies pay them for exposing security weaknesses. The companies usually pay, as it’s very foolish to make an enemy of someone who has demonstrated an ability to infiltrate your network. In network security as in war, the more you know about your adversary, the better positioned you are to beat him off. Many network security professionals got their jobs via ethical ‘’exploits’’ like that above, so the best way to protect yourself from hackers is to LEARN how to do it!
- Read This First
- Why Hack? Hacker Motivations 101
- The Benefits of Ethical Hacking
- The Best Sites to Learn Legal Hacking
- Hackspeak 101: White Hat, Black Hat, etc
The Tentacles of The Dark Side are Long Indeed
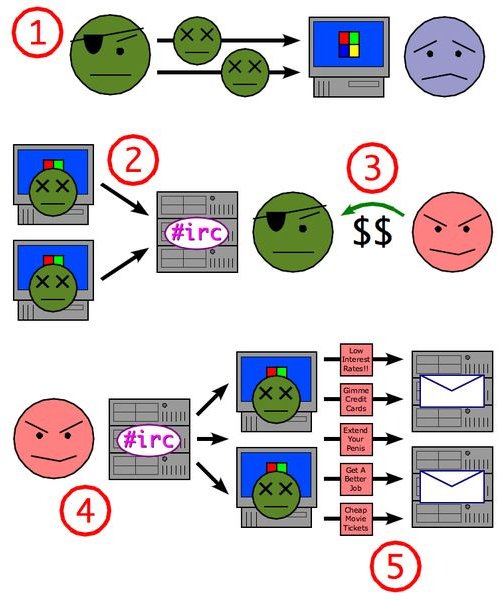
It is the world of ‘‘Black Hat’’ hacking that is out to rip you off. The hacking threat now includes organized criminal groups that are essentially the online arm of the international mafia. These groups uses online scams, phishing, and spam trojans. Unlike the ethical hacker of our first example, or the hackivists who at least have a cause, these groups are out the steal your money or data by any means necessary. These groups can employ dozens of coders as distant as Cambodia or Nigeria. If you have ever spent a dollar online, you are a target for them.
- Common Online Fraud Trends
- 10 Ways to Protect Yourself From Malicious Hackers
- Major USA Cybercriminals
- How to Avoid Falling for ‘‘Social Engineering’’
- Common Phishing Techniques
- Hall of Shame: List of Cybercriminals and How they did it
Hackivism…. At Least Somebody’s Doing It
Targeting a much narrower base is the more unpredictable ‘‘Hacktivist’’ community. Hacktivists target companies and organizations they find unsavory with methods including denial of service (DDOS) attacks. They are not after your money, it’s your reputation they are out to savage (granted, most targets are involved in shady or gray activities anyway). Even large and well-funded companies have been got the better of by hackivists. For example, when Blackberry manufacturer Research In Motion indicated that it would hand over private user data to the British police during the recent riots there, a team of hackivists hijacked RIM’s homepage and replaced the content with a strident manifesto threatening much more to come if RIM continued to cooperate with the authorities.
Of increasing importance is the loosely organized ‘‘Anonymous’’ group, best known for successful DDOS attacks on such controversial groups like the Church of Scientology and waging an all-out cyberwar against anyone trying to oppose wikileaks (pretty much all the world’s governments). Anonymous’ activities to keep wikileaks alive illustrates how hackivists are currently filling a vacuum in society; when something is getting the truth out to the people, but is opposed by the entire global elite, who else can have the will and ability to support it? While the criminal hacking threat affects every internet user, you probably need not worry about the hackivists unless your company is aiding oppressive governments, ripping people off, despoiling the environment, or displaying false advertising.
- Are Businesses Targeted by Hackivists?
- The LulzSec Hackivist Group: Exploits and Method
- Think Your Site May Become a Target? Learn How to Defend it Properly
- Recent Hacking Statistics
The Hacker’s Arsenal
The days when a lone coder could manually enter a major network are mostly behind us now. Present-day security protocols and increased encryption levels dictate that intruders require the technology to burn through these defenses. Most of the software and other technology hackers use for this are available on the open market for their intended reputable function. The good news is, since many of these tools are easily accessible, network administrators can easily figure out what they are up against, and strengthen network defenses accordingly
- The Anatomy of a Wireless Network Hack
- Types of Wireless Hack Programs
- Keyloggers: The Black Hat Hacker’s Best Friend
- How Facebook Can Be Used By Hackers
- Data Security Infiltration Techniques
- Common Hardware and Software targeted by Hackers
- Programs Used to Hack Through Public Networks
Anti-Hacking Tools and Techniques
Hacking has come a long way from the early days of getting long distance calls on someone else’s dime. The scope for theft and a general ability to wreak havoc is now more widespread than ever before. By becoming familiar with the different breeds of hacking threats out there, it is possible to shortlist the threats most likely to target your interests. Make use of the ethical hacking resources listed above to minimize your risk. After all, now that hackers have created a career niche for themselves, it’s best to make use of the available resources. Remember that other than maintaining a round-the-clock IT security staff, the best way to defend against hacking attacks is to know what network sectors they target and defend them accordingly.
- Learn the Hackers Techniques: Go to Hacking School
- Top Ways to Protect Your System From Hackers
- Common Hacking Procedures Stopped by Strong Encryption
References
-
Photo credit:
Previously Published at:
http://commons.wikimedia.org/wiki/User:McCormack/gallery
This file is licensed under the Creative Commons Attribution ShareAlike 3.0 License
-
Linked Articles