What are Trojan Generators?
Creating Trojan using Trojan Generators
There are Trojan generators sold to cyber-criminals that save them the time of coding their own malicious code or software. A Trojan creator isn’t new as they were discovered by antivirus researchers 3 or 4 years ago. What makes the Trojan generator a security threat is that it allows cyber-criminals to customize their malware before compiling it, and can hide their criminal activity by using infected computers as part of a botnet. Botnets are computers that were infected by Trojans, and the end-user does not realize that their computers are now one of the a network owned by cyber-criminals.
How Trojan generators work?
Depending on the version or build of Trojan generator, the tool to create Trojans can be customized as follows:
- Specify which data or file to steal from an infected computer. It can be passwords stored in your browser or e-mail accounts.
- Choose the protocol and port numbers to use in retrieving stolen information e.g. SMTP, HTTP or as a file.
- Customize how the Trojan will run; e.g. as a service, dll, an exe file, or with the ability to change its format from dll to exe, and vice-versa.
- Specify whether the Trojan should act as Keyloggers, turn the victim’s PC into a proxy or turn the infected machine as part of an IRC bot network. It can be customized also to make a Trojan that has rootkit capability, a backdoor, password stealers, or any other types of Trojan horses that the criminal wants to have.
- Other options in using Trojan generators are to specify which antivirus or Windows service to shutdown, to display fake alerts or warnings, or modify the favorites, bookmarks and trusted site zone entries.
- There’s also an option to make a Trojan to act like computer worms so it can distribute itself.
- It allows cyber-criminals to encrypt the Trojan before compiling it to have a new executable that is now ready to distribute; a Trojan.
An example of a Trojan generator is called Pinch software. Most antivirus and anti-malware vendors will detect Trojans that were created using Pinch tool as Trojan.Pinch, Trojan.LDPinch, or Spyware.Pinch.
Examples of Trojan horses created by Trojan generators
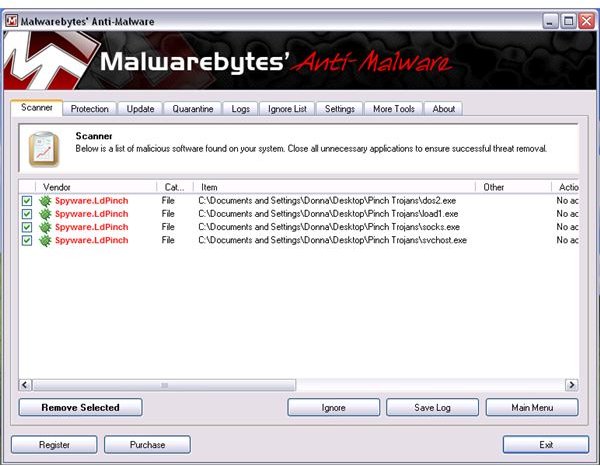
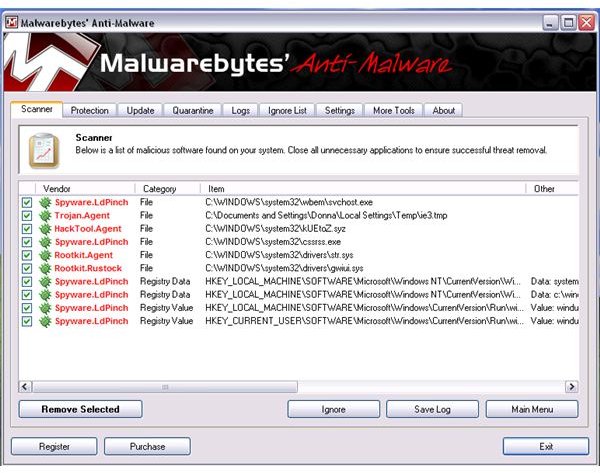
This screenshot is the malware sample that was created using the Pinch tool. Once the files are executed in Windows, the computer will be infected by Rustock rootkit, Spyware LD Pinch, Hacktool or Rootkit agents:
The image below displays the malware scan result using Malwarebytes’ Anti-Malware, after I executed the malware samples that were created by cyber-criminals using Trojan generators:
How to prevent Trojan infection?
Most antivirus programs provide protection, detection and removal for many types of Trojans, as long as you are running an up-to-date and supported antivirus software, in real-time. However, it is best to add extra layer of security because there is no single malware scanner that can detect all types of threats, especially if the malware is a variant or new. Keeping the computer up-to-date with security fixes and by not using unsupported operating system or service packs will help in securing valuable data and prevent infection by Trojans or other malware.
It is also important to regularly backup the computer in case System Restore is disabled by Trojans that were customized by Trojan generators to shutdown or not to run again.
Image credit: Screenshot taken by the author.