Understanding Botnets - What They Are and What They Can Do
What Is a Botnet?
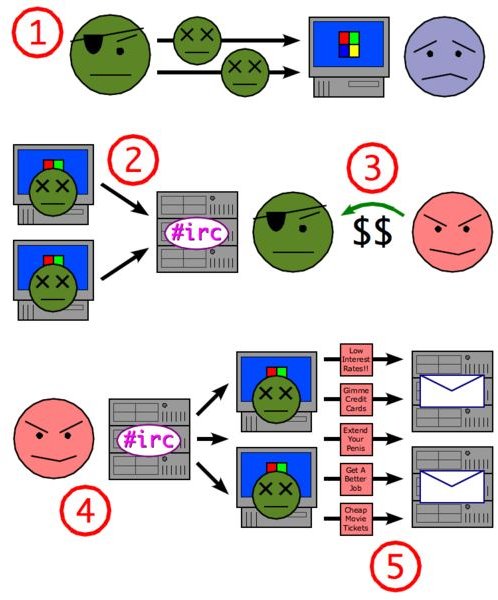
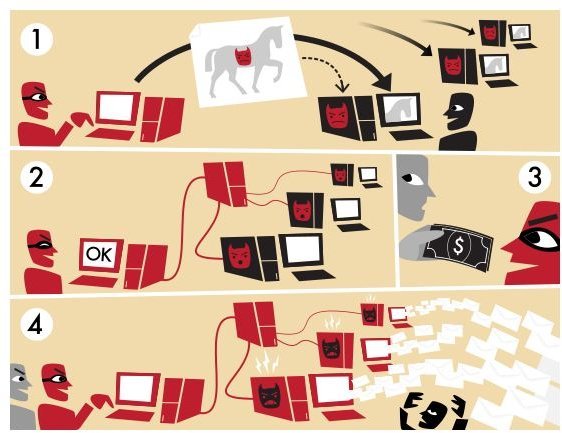
A Botnet is a fairly simple concept. It refers to a large network of “bots.” Bots are computers that have effectively been stolen. It may still be sitting on your desk, but the computer itself has nasty malware on it that has enslaved it for a bot master’s use. Computers inside a botnet are even called zombie computers. Hopefully that can help you visualize things a little better.
Botnet’s are used for a lot of different purposes. For the sake of organization, we’ll cover those in a second. In general, you can think of a botnet as an army for a cyber criminal. Once your computer has been infected with the appropriate malware, he can use it to remotely carry out tasks online. There are two major reasons for building a botnet.
First, upgrading one’s processing power is fairly expensive. Instead of trying to build up a mythical supercomputer, hackers and cyber criminals just round up some outside machines to divide the labor. The potential power of a large network is quite amazin.
Second, a botnet can act as a shield. To painfully stretch out the army example, the general can just sit back in relative safety while his agents go to work. The computer is basically operating in the same manner as if you were running it. Most people won’t notice their infection either. By using these infected computers, the bot master keeps a layer of machines between him and any investigation.
What Are Botnets For?
To be perfectly honest, I’m sure that I’ll miss a few points in this section. Botnets can do a lot of things and I’m sure a few more inventive ideas will come around shortly after publishing this. Since a botnet is just a mass of controlled computers, the options are effectively infinite. A few common uses stand out though.
Probably the largest known use of botnets is for spam emails. Most major spam operators use ridiculously high amounts of bandwidth. All those little emails add up really fast. Spam emails are also frowned upon by just about everyone, so once again, spammers prefer to use someone else’s computers. One very famous network is the Storm Work Botnet. This botnet is believed to have millions of computers under its control that all send out spam to inboxes around the world.
Another possible and popular option is to build up a botnet to allow for successful DoS attacks. Denial of Service attacks aren’t complicated. It’s a fairly simple way of overloading a website and making the server shut down. For another analogy, just imagine that you and a few thousand friends all rush into a deli and start shouting orders. Of course they can’t handle any one order, so a jam forms and continues to build. It won’t take long until the shop just shuts down until they can figure out just what’s going on. Having a botnet on hand allows a cyber criminal to send out large numbers of simultaneous results to a website to waste it’s bandwidth and shut it down. For another example, we can return to the Storm Network’s activities. As discussed here, the botnet carried out DoS attacks on an antivirus website as a means of self preservation. The sites were able to stay online, but they had to dedicate staff, software and hardware to defending themselves. Since the attack was basically free for the assembled botnet, it was a good way to harm an enemy.
General scamming also puts botnets to use. Remember that having a bot on hand allows them to make use of someone else’s computer. While they wouldn’t really need a network for this task, being able to use an apparently unrelated machine would certainly come in handy. Naturally there are creative variants. It was suspected that an early use for Storm was to send out “stock tips” to artificially inflate a stock’s price so that they could make a quick buck before the bubble burst.
Of course, there are other creative uses. I have heard rumors of people using botnets to stealthily (or so they think) click the ads on their own webpages to defraud advertisers and Google. Some botnets are supposedly used for private piracy networks. If the master has the appropriate script for his botnet, then they should be able to create fake accounts on facebook and myspace for phishing activities.
These are just some of the options of course. Now that you understand just what a botnet can do, check the next page for how to keep your computer safe.
Negative Effects of Botnets
We can start from the common ground that you do not want to be part of a botnet. Basically, you’re part of the problem. By allowing yourself to be part of the botnet, you are helping spammers and hackers inconvenience others. Even if you aren’t putting yourself in direct legal danger, you would be annoying a lot of other people out of laziness. Plus, the behaviors to avoid being part of a botnet will translate well to generally staying safe online. Let’s look at a few of the more concrete reasons.
It is possible that you might barely notice any real change to your computer itself. As mentioned in this article on cyber crime cases, hackers sometimes have malware that actually makes a computer run better, since the criminal wants to have a fast and reliable computer in his network. Even if you don’t notice any problems, it is certainly a bad thing to be in a botnet.
First, they’re using your bandwidth. This isn’t a huge problem for the time being, since most people aren’t even close to their bandwidth limits (businesses and Technology Editors do need to watch it though- Ed). It’s still a problem though. They’re taking up part of your allotment and that’s never a good thing, just on principle alone. Using your bandwidth and your computer will also likely lead to slowdowns when they’re operating.
Second, they’re using your computer. While you obviously can’t be blamed for your infected computer being in a botnet, it could cause problems for you. You can suffer serious problems with your email if your IP is spitting out an onslaught of spam emails. It’s not uncommon to be blocked or listed as spammer yourself though to your knowledge you’ve done nothing wrong. You also might have this problem if your computer is used in a larger scam.
Finally, it’s just not a good idea to have a compromised computer. Once you’re infected, you are incredibly vulnerable to any other malware that they feel like shoving into your machine. While the botnet itself may not cause you problems, keyloggers and nasty spyware can cause you serious headaches and even lead to identity theft.
How to Avoid Being Put in a Botnet
This is actually not the difficult part. Largely, you just need to have some standard malware defense in place. As usual, I will recommend a free anti virus program. My personal favorite is AVG Free, although Avira and Avast are good options too (We already did a rundown of the three top free anti virus programs). We also have a new article covering free virus removal tools.
Another important step is to do the Windows updates. A lot of these botnets just use fairly simple loopholes and exploits in Windows. Windows does patch these through their automatic updates, so keeping your system patched will keep you fairly safe too.
Be safe when you browse. A favorite tactic of hackers and scammers in general is to buy domain names that are just one letter away from very popular ones. They get traffic and viewers through misspellings and then attack the user with lots of malware. So be careful with where you go. Also be very careful about opening up spam emails. A number of these are set to automatically infect you once they load. Email programs are getting better at not allowing these scripts to load, but you can’t always trust them. Just throw away spam emails or report them.
If you’re already infected, then you’ll need to find a way to kill it. It is difficult unfortunately, since a number of programs trash or block existing antivirus options as their first act on your computer. You should be able to find an external program to scan and remove an infection though. We have a full list of online virus scanners and a guide for removing the iBotnet program.
Related Articles
If you’re interested in other articles on botnets, then look at these other related articles on Brighthub.
Malware - This dictionary article has some information on botnet agents
Image Credits
Images from Wikipedia Commons