Removing Fake Microsoft Security Essentials Alert Trojan
Fake Microsoft Antivirus on the Loose
Rogue software distributors are known to create fake user interfaces and exploit popular trends. The
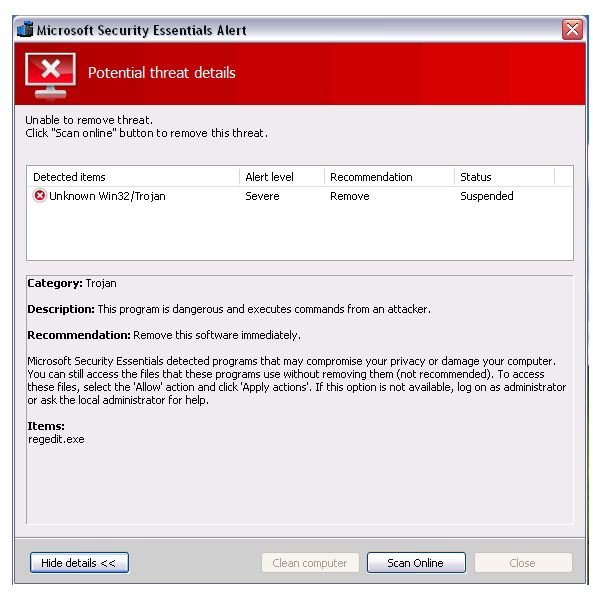
newest victim of bogus software is the free antivirus program from Microsoft. The fake Microsoft Security Essential alert is installed by a Trojan. The rogue program will immediately appear if you try to open any of the useful utilities in Windows, such as the registry editor, task manager or system configuration utility (MSCONFIG). It will also drop defender.exe in the startup program in Windows and replace it with antispy.exe file.
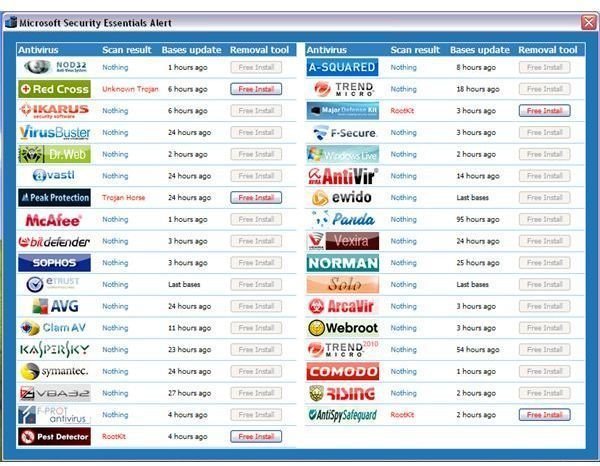
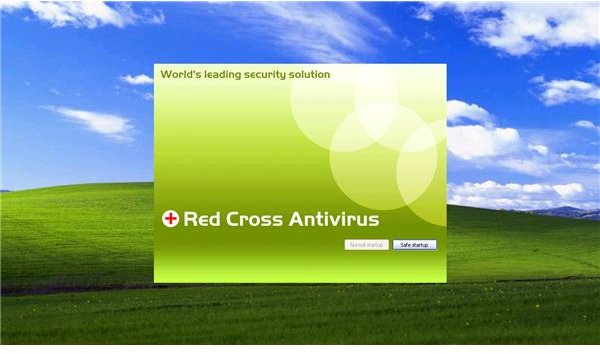
Unsuspecting users who click on the “clean computer” or “apply actions” button will be offered an online scan while the fake threat is in suspended mode. Upon clicking on “scan online”, a new window is opened by the rogue program that will display another fake user interface, offering the free installation of 5 rogue antivirus programs such as Red Cross, Peak Protection, Pest Detector, Major Defense Kit and AntiSpySafeguard. If the user clicks on any of the “free to install” rogue antivirus programs, the computer will immediately restart.
The rogue program will modify the Winlogon registry key by adding “shell” registry values and the PC will not load the taskbar unless the user clicks on the rogue program’s “safe startup” command, which is also a fake command. The new scanner will start to display non-existing threats and continue to display a fake balloon warning message.
Note that if you are using the genuine Microsoft Security Essentials, the free antivirus from Microsoft, you will notice that the alert is different from the fake MSE alert added by a Trojan. See the sample alert by MSE in this Microsoft Security Essentials Review.
Remove the Fake Microsoft Security Essentials Alert
The variant of the rogue program that I installed on a test system does not prevent opening the legitimate anti-malware. To demo
which anti-malware program will successfully detect and remove the rogue program that displays a fake Microsoft Security Essentials alert, I allow 6 free anti-malware program to scan the infected system:
-
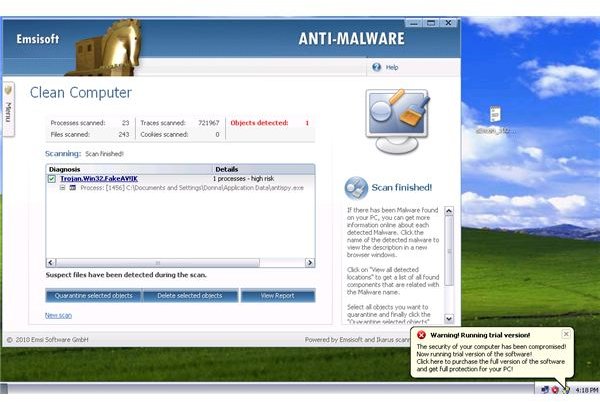
<strong>EmsiSoft Anti-Malware</strong> detects the rogue infection but it failed to detect the registry value in Winlogon key and the temp.exe which is in the same location of antispy.exe. EmsiSoft will remove the rogue program but will leave temp.exe and the shell registry value.
-
<strong>Ad-Aware</strong> by Lavasoft will detect all the executable added by the Trojan but like EmsiSoft, it failed to detect the shell key registry value in the Winlogon registry key in Windows:
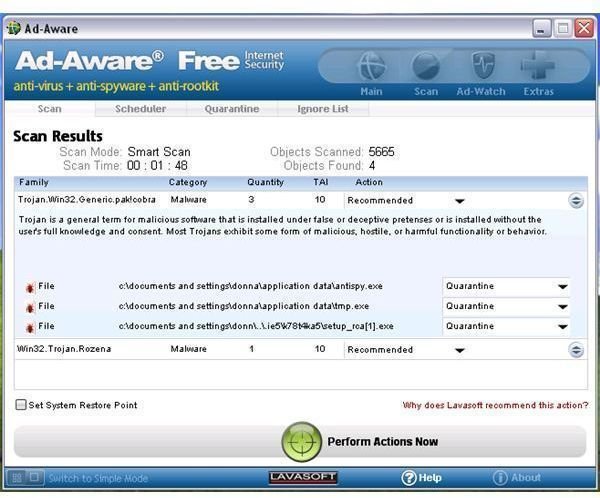
-
<strong>SUPERAntiSpyware</strong> only detected the “shell” registry value and not the executable and running processes. It only detected a malware trace which is not a correct detection since the rogue program is actively running and installed:
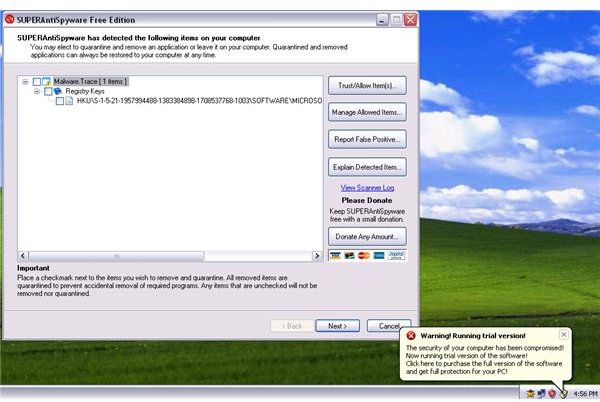
-
Unfortunately, Spybot-S&D and <strong>Windows Defender</strong> did not detect this rogue program even while it was actively running in Windows:
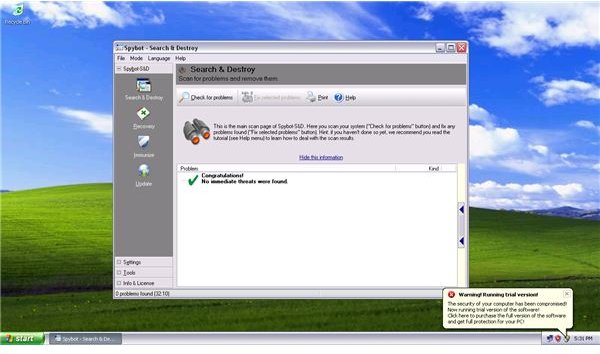
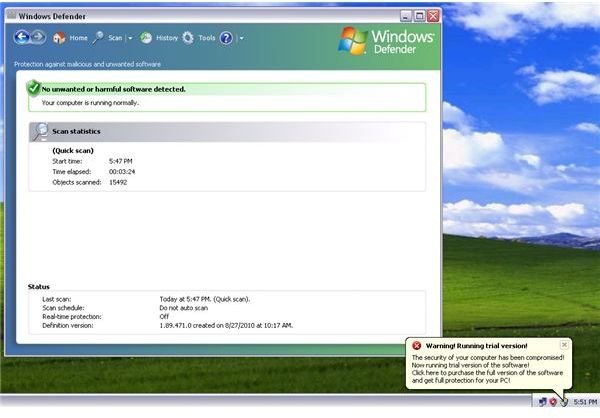
-
<strong>Malwarebytes Anti-Malware</strong> is spot-on in its detection. All executables and the registry value in Winlogon registry key were detected:
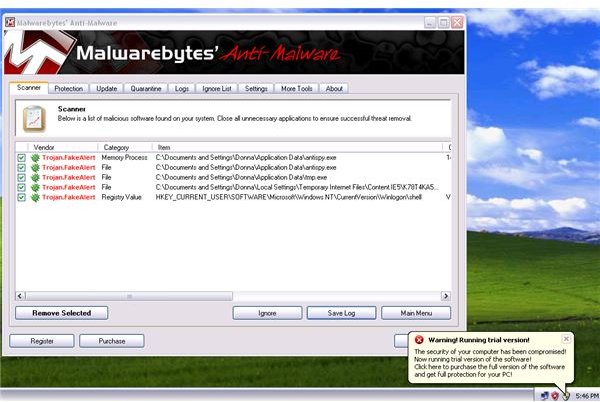
Manual Removal of Fake Microsoft Antivirus Alert
If your antivirus and anti-malware program will not open, you have the option to manually clean the computer by deleting the following files, folders or registry entry.
-
Restart the computer in safe mode
-
Open the Registry Editor in Windows by typing regedit.exe in the run command/box, then hit OK.
-
Navigate to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon registry key. Highlight “Winlogon” registry key at the left pane, and then delete the “shell” registry value at the right pane. Close the registry editor when done. Important: Do not delete the Winlogon registry key but delete the Shell registry value in the right pane:
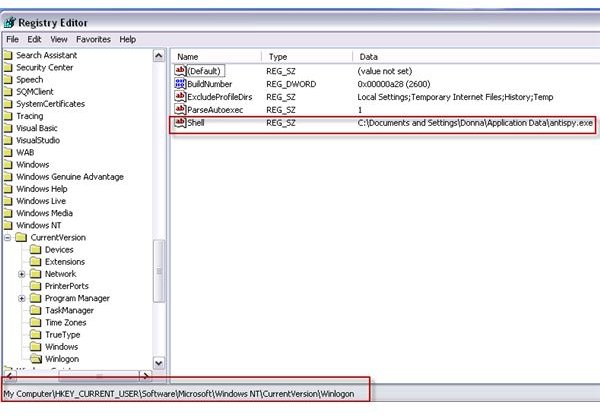
-
Locate the following folder then delete only the following exe files: C:\Documents and Settings\{YOUR USER ACCOUNT NAME HERE}\Application Data\antispy.exe; C:\Documents and Settings\**{YOUR USER ACCOUNT NAME HERE}**Application Data\**tmp.exe
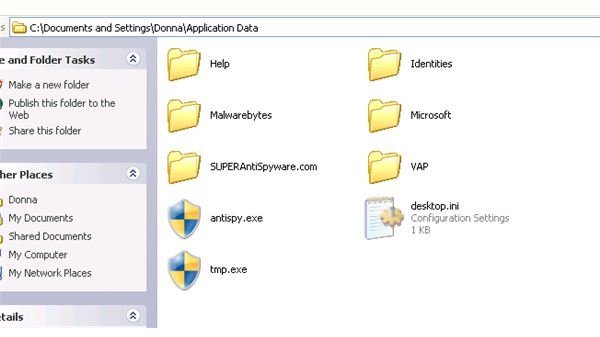
**
-
Pull up the temporary Internet files by typing %temp% in the run command/box and then delete all files in the temporary internet files folder to get rid of the setup file by the fake Microsoft Security Essentials alert Trojan.
-
Reboot the computer to normal mode. Scan the computer using antivirus and anti-malware to verify that there is no more infection.
Preventing Infection - Trojan with Fake Microsoft Security Essentials Alert
In the first page of this article, you will notice that Windows Defender failed to detect the rogue program that displays a fake MSE alert. However, if you have the <strong>Windows Defender’s real-time protection</strong> running, your PC will not be infected by the rogue program. The scanner with aWindows Defender failed to detect the rogue program but the real-time protection of Windows Defender is able to block the Trojan that will install the rogue program. Windows Defender detects it as “Rogue: Win32/PAV”
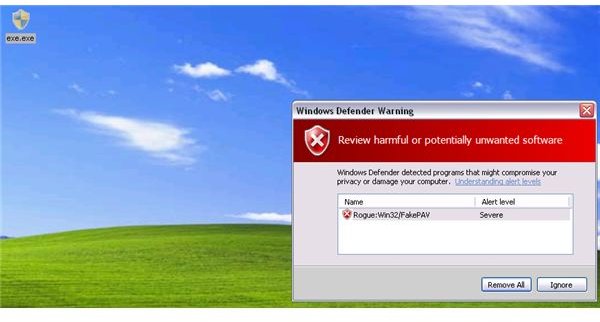
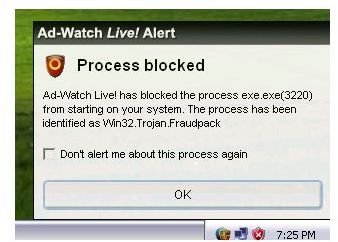
Ad-Watch Live, the free real-time protection module by Lavasoft Ad-Aware Free Internet Security program, also prevents the infection of rogue programs pretending to be an MSE alert:
The TeaTimer module in Spybot-S&D did not prevent the execution of the malware:
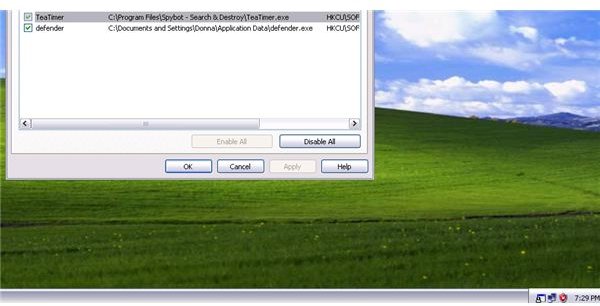
Image credit: Screenshot taken by the author