Internet Security: Intrusion Detection Systems
The Internet is like a parallel universe and just like our real universe, it seems to be expanding at a rapid pace. A computer system or a network is supposed to secure our data, help us get our work done, and keep our businesses running the way they should. But just when we think that we are living in a ridiculously benign world, we have threats and all sorts of attacks ruining the efficiency that you wanted in the first place. An IDS (Intrusion Detection System) might just be messiah that might purge the evil from the virtual world.
What Is an Intrusion Detection System (IDS)?
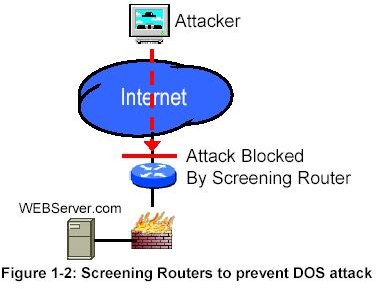
When threats happen or when outsiders have intentions to attack, companies have to take precautionary measures to rebuff and counter the same. An Intrusion Detection System is one such counter measure that companies can employ to extend their security Infrastructure and set it up such that the organization’s data and networks remain shielded from these attacks.
An Intrusion Detection System is built to sniff out any anomalous, incorrect or suspicious activity and works in tandem with the security systems employed by the company.
How does an Intrusion Detection System Work?
IDS Systems
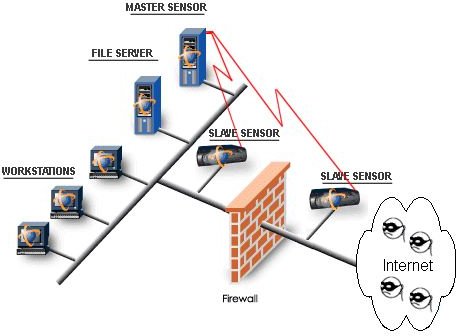
Based on how the IDS is set-up and configured, and the type of Intrusion Detection System being used, the system works by trying to understand the normal process or data flow in and out of a company’s computer network and tries to assess the ‘normal behavior” of the said flow. Once this is accomplished, it can then spot out any anomalous behavior or abnormal behavior which usually occurs when there is a log of suspicious activity, breach of the computer system, data theft, or any other form of attack.
Intrusion Detection Systems usually have sensors: a console that can help monitor events and an engine that records and stores the event data into set databases following certain rules and generates alerts when these rules are not met.
An IDS (and its various types – active Intrusion systems or Passive Intrusion detection systems), hence, can help protect the company’s computer systems, data and network from misuse, theft or any sort of compromise. It can also be used to audit the networking systems, run routine checks and keep the business processes uninterrupted.
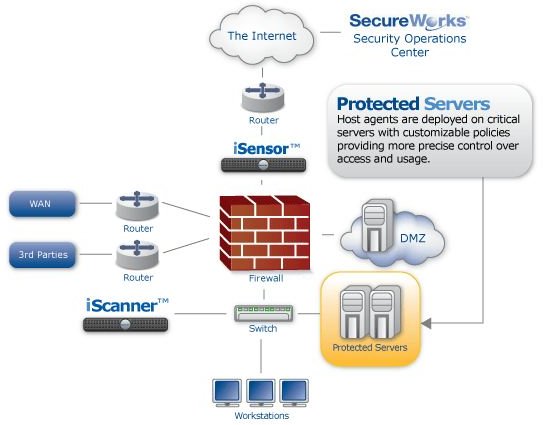
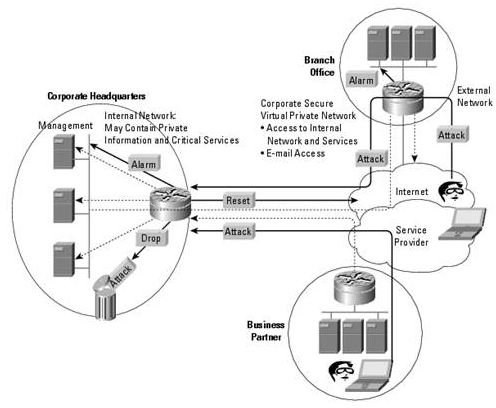
Illustrations
Related Content
Google Bombing, Reputation Attacks and More : How Do You Want Me to Harm You?