Regulatory Issues with Cloud Computing: The Costs of Data Security Breaches
The Problems with Cloud Computing
Regulatory issues with cloud computing are still the main reasons that hold back business owners and company executives from putting their data in the cloud. The way vendors present it, cloud computing provides the most desirable solutions for companies to fast-track on their roads to recovery, especially if they’re still reeling from the effects of the recent recession. It will allow business organizations to participate globally without having to invest on software, equipment and infrastructure.
However, laws and regulations require compliance, and both providers and users are still unprepared to meet all the regulatory requirements. The ease of sharing sensitive or critical information online includes running the risks of being principally liable for exposing data that could be classified as controlled technical information. Service providers’ non-compliance with cloud computing regulations could implicate their subscribers and result in civil penalties of up to one million dollars or incarceration of up to 20 years as criminal penalties.
The problem about compliance is aggravated by the fact that the regulatory guidelines for cloud computing in the US are many, but they do not provide all the answers. What if a cloud user’s manufacturing data requires licensing if transferred to a foreign country?
Accordingly, the Department of Commerce’s Bureau of Industry and Security (BIS), which administers U.S. export controls on non-military items, have addressed regulatory issues related to cloud computing providers. However, not all users or owners of data processed, stored and categorized as “not unrelated to export”, in accordance with the Export Administration Regulations (EAR – 15 C.F.R. 730 et seq), are really sure if they’re excluded from the said regulatory laws.
How knowledgeable are cloud computing users in determining if their activities are classified as “unrelated to exports”? How do they know if they themselves are using data of which security issues have been addressed or compromised? Based on statistical reports, a large percentage of cloud computing providers employ controlled software or technology; hence, it is a must for users to have a thorough understanding of the entire cloud computing services.
For this purpose, the best persons to handle these types of transactions are the certified IT professionals. But then, are there enough well trained IT professionals who could meet the demands of global cloud computing compliance, if it finally emerges as a standard business procedure?
In view of these questions, the following information could give readers a wider perception about the regulatory issues with cloud computing services:
Image Credit: Πrate for Wikimedia Commons
Important Background Information About the Legal Issues in Cloud Computing
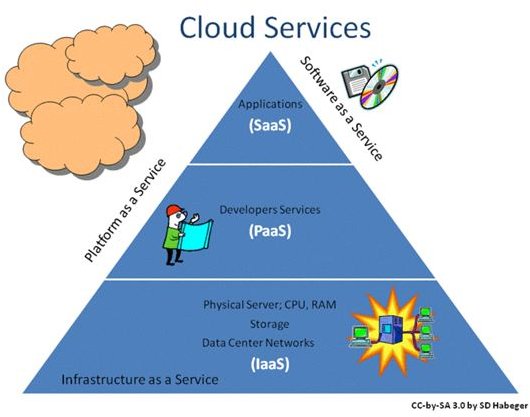
The Federal Information Security Management Act (FISMA)
FISMA implementation was established in January 2002 in order to provide concerned federal agencies with standards and guidelines regarding privacy and security concerns; but such guidelines are not applicable to matters of national security. They are embodied under publications FIPS 199, FIPS 200, NIST Special Publications 800-37, 800-39, 800-53, 800-53A, 800-59 and 800-60, which interested readers may find at the Computer Security Division’s publication page. ( Readers can find the link in the reference section located in the third page of this article.)
The Health Insurance Portability and Accountability Act (HIPAA)
HIPAA requires technical and physical safeguards to control access to private and public health care facilities, including the Veterans Health Administration. Cloud providers are required to comply with HIPAA’s legal and regulatory concerns to ensure security and privacy, and they may differ in certain jurisdictions.
Although the service providers will be held liable for any breach or leakage of data content under their cloud, the organization who hired the service providers are held mainly responsible under HIPAA.
Image Credit: Sdhabeger for Wikimedia Commons.
Please proceed to the next page for more insights about the regulatory issues with cloud computing.
Important Background Information About the Legal Issues in Cloud Computing (continued)
Feedback from IT Professionals
According to the organization responsible for developing federal regulatory guidelines, which is the National Institute of Standards and Technology (NIST), a study that involved the participation of more than 900 European and American IT professionals revealed their concerns about cloud computing. The system was implemented without their full awareness as members of their respective organizations.
They liken cloud computing to rogue wireless access points of organizational computing infrastructure that could evolve into an unmanageable mix of unsecure services arising from lack of proper governance. Hence, policies and procedures should cover standards used for design, implementation, testing and monitoring from application development to service provisions.
In addition, dealing with cloud computing services require audit mechanisms in place to determine how the company’s data is stored, used and secured as well as to validate if the service providers are compliant with the policies being enforced. In addition, risk management procedures should be performed to ensure that mitigating actions are in place. That way, the inherent and shifting risks that are present in cloud computing could be addressed even before they take place.
Examples of Regulatory Issues with Cloud Computing

Location of Stored Data – Service providers generally do not disclose the location where the service subscriber’s data are stored. It leaves users in the dark regarding the extent of protection applied to their critical information.
Although security certifications could lessen the user’s anxiety, the matter of determining if the provider’s compliance with legal and regulatory laws includes those that cover the geographical location where data is stored, aside from the laws of the areas where the data was collected.
Companies should be concerned where their data go and should make sure they do not go beyond the territories where the EAR or ITAR (International Trafficking in Arms Regulations) restricts transfer of technical information.
The service subscribers’ ignorance regarding the destination of their stored data does not discharge them from their obligations to comply with the regulations governing transfer or export of controlled technological data—nor from the penalties resulting from any such violations. The EAR imposes $250,000 per transaction or twice the amount of the transaction violated, whichever is higher.
One example provided by the NIST is the European 15 data protection laws, as it requires additional procedures in the handling and processing of data transfer from European Union countries to the US.
Archival and Retrieval Capabilities – An organization constrained to produce electronic documents like electronic mail and/or its attachments or any metadata relevant to a particular cloud document, for purposes of satisfying audit examinations, regulatory assessments or as litigation evidence, could be frustrated from doing so. A service provider may not have applied due diligence in its preservation or is capable of altering or obstructing presentation of evidence, thus impairing the cloud user’s compliance abilities. This of course, could negatively impact the results of any inquiries regarding the subscriber’s business, which could likewise entail civil or criminal penalties.
Image Credit: Rico Shen for Wikimedia Commons
Breach of Trust from Within – Intentional or unintentional non-compliance with regulatory issues that govern cloud computing regulations widens the range of possible sources of insider threats or malicious attacks. The movement of data, the use of outsourced applications, and the uncertainty of security controls observed to carry out the cloud operations by a network comprising contractors, other cloud users and the provider’s organizational members, including those that resigned from the computing network’s organization, are beyond the subscriber’s control.
Any laxity by one component can expose a large number of shared data to threats of malicious insider attacks.
Image Credit: Ramu50 for Wikimedia Commons
Find more information on the next page about other possible consequences regarding non-compliance with regulatory issues with cloud computing.
Examples of Regulatory Issues with Cloud Computing (continued)
Ambiguous Terms Used for Data Ownership Agreements – There are existing controversies arising from social networking sites over the privacy and ownership rights of the parties involved, e.g.:
“Our offer to allow you to access the Service is conditioned on your agreement to all of the terms and conditions contained in these Terms, including your compliance with the policies and terms linked to (by way of the provided URLs/hyperlinks) from this Agreement, such as our Copyright and Privacy Policy – Your use of any of the services constitutes your agreement to these terms.”
Technological industry representatives contend that requiring stronger standards other than those already developed by the National Institute of Standards for digital security applications could limit further technological developments. Others contend that information is a commodity; hence, different points of view regarding ownership rights could stir controversies and subsequently result in lawsuits.
Reliance on Composite-Based Cloud Computing Services – Cloud service providers that rely on third-party service providers could easily compromise the services being extended to cloud computing subscribers. Yet guarantees regarding performance or the extent of a provider’s responsibility could be unclear or even unspecified, since users could be kept in the dark about the network’s reliance on composite based services.
Image Credit: Sam Johnston for Wikimedia Commons
Limited Visibility and Lack of Transparency to Allow Subscriber-Initiated Audit – Understand the possible legal implications of not fully knowing how the cloud service provider facilitates or carries on its business, or how security control features are being processed or implemented, or the provider’s diligence in complying with the regulatory issues that pertain to cloud computing.
However, subscribers should also understand the reasons why most cloud service providers limit their visibility and the traceability of their operations, inasmuch as putting their systems in full view could be used as a means to attack their site.
I****mplementing Security on the Subscriber’s Side – Compliance with privacy and security protection controls should work both ways, since attacks to the cloud network could be launched form the user’s site. Hence, service providers’ operations could be impaired and threatened if the subscriber and the members of its business organizations do not observe security protocols. The liability of the service subscribers will be definitely stated as part of their agreement to the terms and conditions, since this, in a way, institutes the cloud network’s control over the client’s organizational components.
Image Credit: Компания “Мегаплан” for Wikimedia Commons
Summary
There’s a long list of privacy and security breach incidents that serve as examples of real threats and risks due to non-compliance with regulatory issues that govern cloud computing technology. Such incidents have adversely affected both providers and subscriber-users. Hence, NIST emphasizes the importance of negotiating workable solutions, provisions, procedures and incident responses before entering into any cloud computing service agreements.
In addition, cloud computing requires the employment of highly skilled and well trained IT professionals who are likewise well versed in different federal laws, aside from those previously mentioned, as they could affect or be affected by cloud computing technology, e.g. the Clinger-Cohen Act of 1996, the National Archives and Records Administration (NARA) statutes, including the Federal Records Act (44 U.S.C. Chapters 21, 29, 31, 33) and NARA regulations (Title 36 of the Code of Federal Regulations, Chapter XII, Subchapter B, Office of Management and Budget (OMB) Circular No. A-130, particularly Appendix III, the Privacy Act of 1974), the Payment Card Industry Data Security Standard (PCI DSS) and the Freedom of Information Act (FOIA), which are only a few of all regulatory issues that govern cloud computing in the U.S. Subscribers may be constrained to look up the Canadian and European Union laws as well.
References:
- Publications: NIST.gov Computer Security Division, Computer Security Resource Center, created July 03, 2007 and last updated February 22,2010 https://csrc.nist.gov/publications/ .
