Windows Azure Security - Is Windows Azure Really Safe?
Windows Azure Security - An Introduction
Windows Azure is actually a Microsoft ‘operating system as a service’. People can use Windows Azure from anywhere as it is cloud hosted by Microsoft. It offers programmers and developers with on-demand computer and storage access to host and manage web applications on the Internet. This is achieved by Microsoft data centers that also offer SkyDrive and Office 356 facilities.
As Windows Azure hosts programs and data of its customers, it is the responsibility of Microsoft to take care of all the data security issues - predictable and unpredictable. Though the cloud is considered safe, there has been some news that some data on Microsoft Office 365 servers was recently compromised. Microsoft took some steps to secure the data and to avoid data leaks/hacks on all of its cloud computing services following the data leak from Office 365.
This article discusses the effectiveness of Windows Azure security. We look to our readers to deduce whether these measures are sufficient and inform us so that we can pass on your thoughts to Microsoft for evaluation and implementation.
The Basics
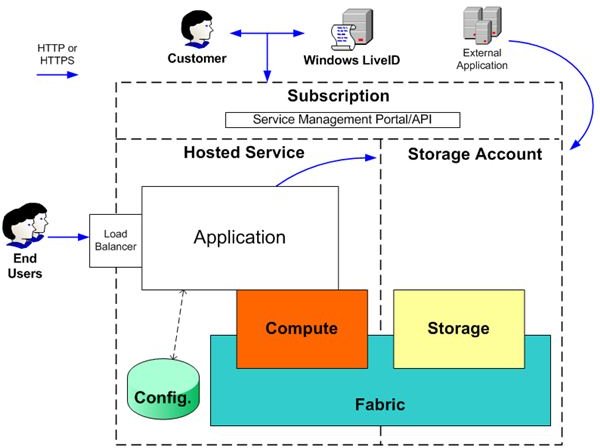
Windows Azure is designed to abstract the infrastructure that underlies different applications (servers, operating systems, web & database software, etc). This section will deal with the basics of Windows Azure security - as seen by consumers when they approach the Windows Azure cloud. The figure depicts the basics of the Windows Azure model.
Per the figure, Windows Azure offers two basic functions: application hosting and data storage. Consumers build and manage their applications upon these two basic functions. To use Windows Azure, consumers will need a subscription. This subscription is created by associating the consumer credentials with a credit card number. Access to subscriptions are controlled by the consumers’ Windows Live ID and password. Microsoft considers these factors as basic security tools (the subscription number and Windows Live ID plus password).
Customers can upload the developed application and manage their accounts through the Windows Azure website or they can use the Service Management API (SMAPI). The SMAPI authentication is based on the consumer-generated public/private key and a self-signed certificate that needs to be registered on the Windows Azure website. Thus, Windows Live ID offers security when a consumer wants to access his/her data using the portal and the SMAPI authentication comes into play when the consumer wants to use the API to interactively manage his/her data. According to the Microsoft Whitepaper, “The Service Management API queues the requests to Windows Azure Fabric (ref image) so that the Fabric can provision, initialize, and manage the consumer application being hosted.”
For accessing their storage in Windows Azure, the consumers need a Storage Account Key (SAK). Each SAK is unique per storage account. Consumers can reset the SAK if they lose it or if they feel a need to change it.
Image Courtesy: Microsoft Azure.
Cloud Security Design
Being a cloud service provider, Windows Azure must provide for security for hosted applications and storage data. This page expands upon the security features mentioned on the previous page. Microsoft, in the whitepaper on Windows Azure, acknowledges that it should provide confidentiality, integrity, and real-time availability of customer data. The following sections check out how Microsoft aims to achieve this in Windows Azure.
Confidentiality
Microsoft makes sure that each data is available to the consumers only by authorized personnel. For this, Windows Azure employs the following measures:
- Identity and Access Management ensures that only authenticated people can obtain access.
- Isolation makes sure minimized interaction with data by keeping the containers physically separate.
- Encryption is used within Windows Azure for protecting control channels. Encryption is offered on demand for customers who need more data protection
Integrity
The Integrity of data on Windows Azure allows the consumer data to be protected from unauthorized changes. The Windows Azure fabric acts as a virtual machine and each virtual machine is connected to three virtual hard drives:
• The D: drive contains one of several versions of the Guest OS, kept up-to-date, selectable by the customer.
• The E: drive contains an image based on the package provided by the customer.
• The C: drive contains configuration information, paging files, and other storage.
The virtual drives E: and D: are read-only and are updated only by the Windows Azure operating system from time to time. This design preserves the integrity of both the operating system and customer application.
Only consumers with the verified digital certificates can access and change the configuration files using SMAPI or the Windows Azure portal.
For Windows Azure storage, security is implemented by the applications that access data. This means that the hosted applications should also contain integrity checks. This also means that a part of Windows Azure security for storage is dependent on the consumers. Other than these, we have talked about the SAK on the previous page.
Availability and Accountability
For the data and applications to be readily available, Microsoft uses a number of servers. While one of them is the main server, others are used for backup. Thus, the application and data are replicated over different servers. In case the main server is down for some reason, the control is given to one of the backup servers. Any changes made are updated as soon as the main server is up again. The real time backup ensures that the end users get the latest version of the hosted application and that no data is lost during the outage.
This article offers just a bird’s eye view of Windows Azure security. If you have any doubts, or if you wish to share anything about the security features in the Windows Azure cloud, you are welcome to post comments.
Reference courtesy of Microsoft’s Whitepaper on Windows Azure Security (Charlie Kaufman and Ramanathan Venkatapathy), 2011, retrieved at - https://www.microsoft.com/windowsazure/whitepapers/papers/default.aspx
Related Reading: Office 365 Comparison