How Phishing happens: Know Your Enemy (Man in the Middle Attacks)
Phishing can cripple businesses beyond repair and hurl individuals into an abyss. The more you know about it, the better it is for your business and your personal data security. There has been a lot of talk about phishing and how it can harm your system and yourself, if you aren’t careful about your security while you are online.
The Internet is being used widely, with new countries (developed and developed) setting up camp online; new businesses being launched everyday; new users taking to the Internet in droves and an increasing pool of users throughout the world. Which means that the number of phishers increases too. The threat wagon isn’t going to stop anywhere soon.
The term Man – in – the – Middle has been in use since the Year 1994 and has variations ( That Man in the Browser Can Kill You). This form of attack simply means that the program is placed between the sender and the recipient. Man-in- the-Middle, however, is a complicated Trojan program that places itself between the user’s server (system) and the Attacker’s system (server) to record, analyze and even take action sometimes. Also called “Session Hijacking Attack”, this is a way for the attacker to intercept the session to access any valuable information revealed in that session.
Think of this point as a vantage point from where he can keep tabs on everything you do – including using your bank details to log in and do what ever he pleases.
How does it work?
An Illustration of MITM
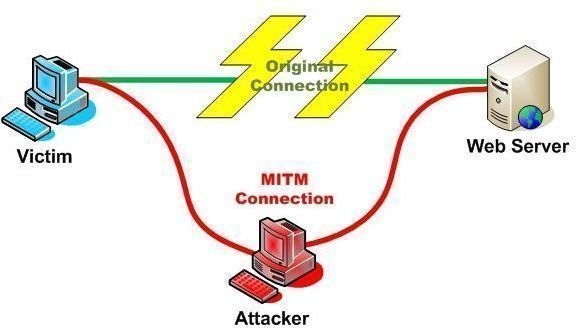
For a Man-In-The Middle Attack to happen, the proxy connection from the attacker must be able to intercept and loop-in the connection to the main application server(the bank/financial/Trading account server) that the user is trying to access. For HTTP access (the common type on the Internet), the attacker intercepts the original connection while simultaneously making another connection to the real server. For https:// connections (used for financial transactions), a SSL (Secure Socket Layer Certificate) is first established and then the usual process follows. It can be done in the following ways:
-
By Building Transparent Proxies : By using brute-force and coercing all of the outgoing http:// and https:// data from a user’s Internet connection, the data outflow can all be intercepted by a proxy server which lies en route to the real server (like that of the bank or Company Intranet). Sometimes transparent proxies can be established on resident networks too.
-
By Poisoning the Domain Name System Cache: A Domain Name System is the most important part of the Internet, without which it can all come to a screeching halt. Each website (like yahoo.com) is also known and represented by a string of “octets” like 123.345.24.56 or something similar. Since it is extremely difficult to remember such strings of numbers, we have domain names like yahoo.com and brighthub.com, which make it easy for us to remember these sites. DNS Cache Poisoning, then, is the act of modifying or altering the DNS resolver caches, so that when an input or request goes to the server for a particular domain, the attacker’s domain shows up, instead of the original domain. This fake domain can be used for the attacker’s efforts to grab the data the attacker has been looking for.
How to Prevent a MITM Attack?
The Man in the Middle Attacks can be checked and prevented if certain things are taken care of, for Instance:
- Usage of PKI (Public Key Infrastructure) and Strong Authentication with a Trusted CA (Certifying Authority) can achieve flawless electronic transactions. Most of the traditional risks associated with the Internet can be curtailed by using the combination of PKI and a Trusted CA. (Like Verisign, for example).
How PKI works with VA
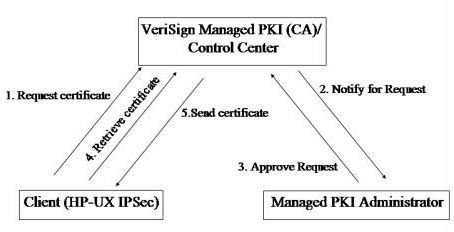
A specific security tool like Tricipher (there are many more) can be used to ensure trust and robust authentication using the Vault-like features of these tools. See specific details in <em>How Tricipher helps in Preventing Man in The Browser Attacks.</em>
Related Resources
A series of other informative articles have been published about phishing ( Ignore Phishing and You are a Dead FISH). Together, all of these articles, along with detailed enunciation of each of the attack types or vectors- as they are technically called, should arm you against any possible breach of security. Please see below
5 Ways to Avoid Phishing
Common types of attacks that you should know
Phishing Delivery Mechanisms: Know Your Enemy (URL Concealment or Obfuscation Attacks) – Part 4