Spam is not just trash mail - It can kill if you aren’t vigilant
Beware: SPAM !!!
Spam is driving people to believe that email isn’t trustworthy anymore, just when the world is preparing itself to embrace the digital “workhorse” messengers. While we think that the security industry’s efficiency has come of age and when we seem to be stuck to our lazy chairs, we have a new burst of ultra-sophisticated “Malware” and all sorts of other new security threats that seem to have rendered the previously impenetrable security practices, obsolete. Spam went up by a whopping 100%; the “self-defending Bot networks” have been introduced (Storm Trojan) and really, a virus isn’t the threat anymore. The multi-pronged attacks have ensured that the legacy anti-spam software systems gag and throw-up, unable to withstand the force of such attacks. Plain vanilla anti-spam, anti-virus and security protocols are redundant and new threats call for war like action. Here are the trends that should make you shudder and re-think spam defense.
Attachment Types galore: While the years 2005 and 2006 saw limited types of attachments being using predominantly for spam attacks, from 2007 there has been a mind-numbing range of attachments being used – a whopping 20 types and counting. Some of which are so complicated that the email spam defense engines can’t do a thing about them.
Come here and get infected: Trends in the year 2007 floored the security industry and left it gasping for breath as new ways of spamming emerged. Spammers are now not just trying to sell drugs and products/services, but are actually shooting out seemingly innocuous messages that have nothing but a pitch and a URL. This is typical “Fishing with bait” and getting you to go out and get your own computer infected.
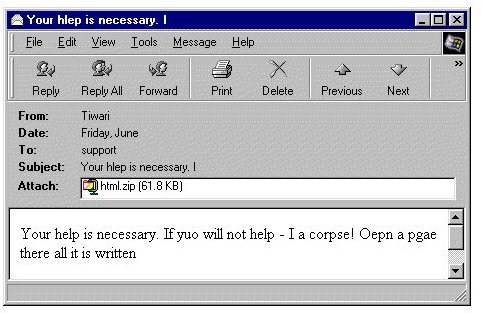
The “Feebs” mass Mailing Worm: “Feebs” is a self-propagating email worm that enables the attackers to access your computer remotely and allows them to set-up their home base on your computer so as to retrieve your personal information. Give out your card or bank details and see what happens next, if you haven’t fainted, that is. Once deployed onto your system, the “feebs” takes on a stealth mode and keeps a vigil on the outgoing SMTP Connections and will upload an infected Zip file into the system’s own messages, which the recipient is likely to click and open as they come in from a trusted source. Once it is present on an infected computer, the worm will listen for incoming connections, accept commands to retrieve files from the local computer, upload new virus templates to propagate and retrieve new executable programs to run.
The Storm Cometh: Social Malware is the new wave in spamming and it is the stark ugly reality we will have to contend with until the wave cools out. The “storm” class of malware is a sophisticated social malware that borrows attributes from the social networks of Web 2.0. The Storm links various technologies together and attacks with the sheer magnitude of all these technologies together and with an alacrity and speed that you wouldn’t expect from it. It uses both the web and email to proliferate and attack. What makes it especially dangerous is that it is self-propagating – sends massive amounts of spam in multi-phases to spread by baiting the users to multiple URLs, which are dynamic and always changing, but contain storm malware. First detected on January 17, 2007, has reportedly grown to sizes hitherto unseen. Storm is also known to propagate through peer-to-peer software.
Mal Where? : A Google study, released in May 2007, analyzed the presence of malware across all pages indexed by the Google search crawler. It was reported that one in ten web pages are infected with malicious code, and that 70 percent of Web-based infections were found on “legitimate” websites (those with a neutral to positive reputation). Corporations should now not just keep email on the high vigil but also the legitimate, usually trusted sites. The simple fact that the malware is ubiquitous should send a shiver down the spine of every IT executive, entrepreneur and CIO, now that the sophistication has reached new heights and the spam is still an ugly reality that has to be contended with.
Other Editor’s Picks from this Author
>» 10 Terrific ways to boost productivity of your Windows PC
>» Common PC Defragmentation Myths Busted
>» 5 Steps for a Robust Computer Virus Clean-up
>» Get away from your PC once in a while: Getting the most from Remote Access software
Images