Malzilla Review: An AntiMlare Tool for Windows
What is Malzilla?
Malzilla, by Boban Spasic is piece of software (malware hunting tool) helpful in analyzing malicious websites including their techniques and scripts used. Malzilla it is not a web browser but emulates web browsing. It downloads a web site’s code so that drive by downloads can be examined in a safe environment using decoding and deobfuscation.
System Requirements, Download & Installation (3 out of 5)
Malzilla has been designed for 32-bit Windows operating systems. I had no issues running it on Windows Vista and Windows 7 based test systems.
The most difficult part of the install is choosing the right download … Visiting the Malzilla homepage on sourceforge.net defaults to InnoBF.zip, which is a brute force password cracker. To get the Malzilla application under consideration click View all Files, and then select malzilla_1.2.0.zip.
Malzilla runs without installation, just by clicking the Malzilla.exe executable in the downloaded folder which is only about 4 MB of size when extracted.
Interface, Help & Support (3 out of 5)
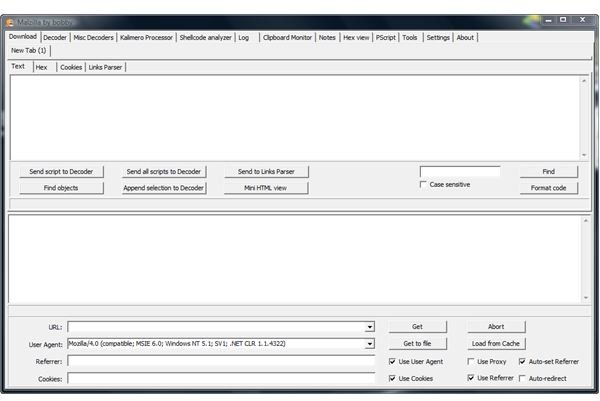
When you start Malzilla for the first time you will see a proprietary interface. Unless you are a hard core malware analyst you will likely be overwhelmed by the software’s complexity and dash for the manual. Unfortunately, the amount of information provided by Malzilla.pdf is very limited. Along the same lines does Malzilla online help and its associated Open Discussion forum only have about ten posts in total.
I doubt that the lack of instruction can be compensated by the option to open a support request ticket. Most of our readers will probably close and forget about Malzilla at this stage, and I can really understand them. Unless you are very interested in malicious web page analysis this software definitively isn’t for you.
Features & Performance (4 out of 5)
When “browsing” web sites using Malzilla you can specify whether you would like to be recognized as if you were using Firefox, Internet Explorer or another user agent to study the mechanisms malicious website employ to infect their visitors with drive-by downloads. To help tricking the web site you can define and mimic any referrer, that is the information which web site you are coming from.
Malzilla shows you the entire source code of a website including full HTTP header information. Moreover, it permits you to decode and deobfuscate Java scripts which, for instance, can be very helpful for analyzing websites selling fake software such a performance optimizers and antivirus programs by means of a rogue system messages.
The malware hunting tool works with proxies. However, as most proxies have difficulties processing advanced scripts and/or modify http header information you may want to use Malzilla without a proxy unless you have good reasons.
Price to Value (5 out of 5)
Malzilla is open source and completely free.
The Bottom Line
Malzilla is helpful for malware analysts, IT experts and students in a higher education interested in Web page and JavaScript deobfuscation. As a best practice use an isolated test systems which has no real data when analyzing malicious websites. This is a general safe measure not restricted to the Malzilla malware hunting tool.
Reference and More Firefox Add-ons Reviews
-
Adblock Plus: An Ad Blocker for Firefox (Recommended)
-
TrackMeNot: The worst Security Tool Ever?
-
FEBE: Firefox Environment Backup Extension
-
FoxyProxy: An Open Source Proxy Switcher
Screenshots taken by the author
Author’s own experience