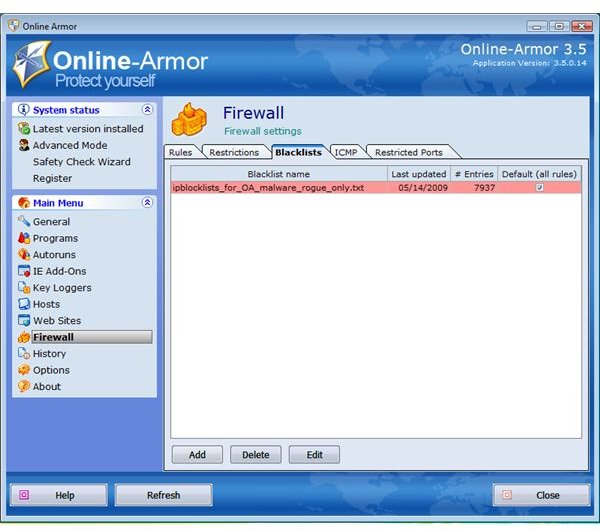
Blocking Malicious IP Using Blocklist Manager
Blocking of IP Addresses
Computer administrators and advanced users block IP addresses from communicating to networks or computers to secure them from known IP address of malware, rogue distributors and attackers. Blocking by IP address is more powerful than blocking by domain name or URL. When blocking a malicious IP address, you can block many websites that share the IP address and you are protected from new malware domains that use the same IP address.
Advantage and Disadvantage of Blocking Malicious IP
Any type of security solution has pros and cons. The advantage of blocking by IP address is simple: You are protected from known attackers, malware or rogue websites that are assigned or using their own servers. Blocking an IP address is more effective than blocking by domain name because existing and new domains that use the same IP will not be able to communicate with your computer.
When you use an effective solution to protect the computers or network from a malicious IP, there is a drawback. Any reputable websites that share the same IP address with malicious sites or servers are also blocked. In addition, some malware distributors and internet attackers will use the fast and double flux techniques. To learn more about the said attacks, please refer to the security advisory by ICANN in *PDF format or view the HTML version using via Google website.
How to Block Malicious IP Addresses
There are several methods to start blocking malicious IP addresses:
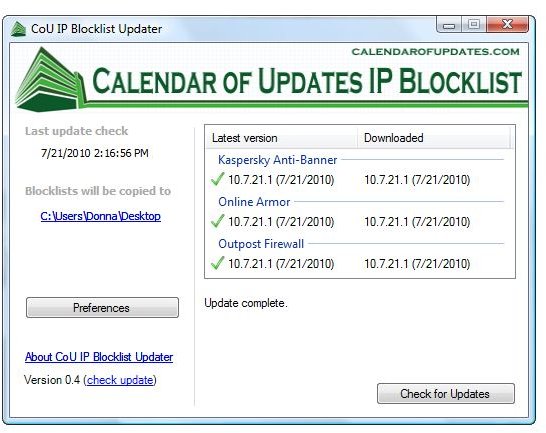
- Use an antivirus or firewall program that lets you block malicious IP address. Examples of firewall software with IP Blocking are Online Armor Premium by EmsiSoft, Outpost Firewall by Agnitum, Kaspersky Internet Security and PURE’s Anti-Banner. You can use CoU IP Blocklist Updater to download the blocklist file and import to the said firewall programs.
- Standalone IP Blocklist program like Protowall, PeerBlock and PeerGuardian. You can use the BISS Blocklist Manager to download and subscribe to several types of blocked IPs.
- Use <strong>ZonedOut</strong> to add blocked IPs and websites for Internet Explorer. You can use any list that is in text file. Example: download the CoU IP Blocklist for Kaspersky Internet Security or Kaspersky PURE. Import the blocklist file to IE restricted zone using ZonedOut program. Note that when visiting blocked IP address, IE will display the page but is in restricted mode.
- Using IPSeccmd in Windows XP - You will install IPSeccmd from XP SP2 installation disk. For detailed instruction, please see Microsoft KB813878
- Using IP Security Policy Management in Windows 7 and Vista - This is already built-in to Vista and Windows 7, but you need to add the IP Security Policy Management snap-in by typing mmc in the Run box in Vista. Next, click File > Add/Remove snap-in. Locate IP Security Policy Management in the list of available snap-ins then select it to add. You can use this snap-in to start blocking IP addresses.
Important note: Using IPsec utility in Windows is for advanced-users only. An incorrect usage of IP Security Policy Management might put your computer at risk. If you are unsure what to do, use third-party firewall in blocking IP malicious addresses.
Can You Add IP Address in Windows Hosts file?
A hosts file lets you block a malicious website’s domain name but cannot be used to block IP addresses.
Using best practices in computing and internet together with customized hosts file, blocking IP using blocklist manager or blocklist file, antivirus, firewall programs and using up-to-date operating system and applications will greatly help prevent attackers.
Image Credits: Screenshot taken by Donna Buenaventura