Product Review: ZoneAlarm ForceField
Introduction
Back in the mid 1990’s, there were many different ways people accessed the Internet: IRC (Internet Relay Chat), FTP (File Transfer Protocol), POP/SMTP (Post Office Protocol/Simple Mail Transfer Protocol), and HTTP (HyperText Transport Protocol through a web browser). Each of these different ways of reaching the Internet were accessed using a specialized program designed primarily for that function. The general masses weren’t really very verse in all these, so only those that were technical or somewhat technical used them.
Today, almost everything on the Internet is done through the web browser. Although there are many flavors of browsers out there, the general means by which content is delivered are basically the same. Users see everything through their browser, they navigate, watch video, listen to music/radio, check e-mail, and chat on the Internet through their browser. Everyone today experience what the Internet has to offer through their web browser!
Because the web browser is so easy to use, everyone with a computer on the Interenet uses it. Whether the user knows about computers or not, the browser is used by novice computer users on a daily basis to run their daily digital lives, as well as their normal lives. It is for this very same reason that the browser has become the perfect vector from which to attack unsuspecting users with phishing, spyware (with keyloggers), and unsolicited downloads.
As such, this may very well be the very reason Zone Alarm developed ForceField. In the next few sections, this article will provide a review of this product, and in the process hope to help you determine whether this is something you may need in your arsenal of computer security tools.
Overview
This review will cover the following areas:
- ForceField as marketed by CheckPoint
- User experience
- ForceField put to a couple of tests
- A phishing test
- Search for spyware/keylogger
- The verdict and recommendations
This review will not cover how to use the product and will not provide feedback on its private browsing feature. As some of you might know, private browsing is a feature some browsers (like Internet Explorer 8) provide as a core security function, and as such doesn’t add more value.
ForceField as Marketed by CheckPoint
According to CheckPoint’s ZoneAlarm ForceField site, the product is designed to protect your online life. It is there to provide protection for your computer and personal data against threats from phishing, spyware, and dangerous file downloads.
Specifically, their online brochure states ForceField provides a shield for your browser since it keeps you safe from the new generation of web threats as you surf. It also states that you can shop and bank safely. I’m assuming that they are referring to protection from bogus bank e-mail and shopping deals one might get in their mailbox that redirects one to a phishing or a spyware site. Lastly, it provides the ability for one to browse in private–meaning that a browsing session doesn’t leave a trail on the computer for others to read.
You can purchase ForceField for $29.95. There is a try-it now link on their the ForceField page, but there is nothing there that would allow you to download ForceField by itself. However, you can download a 15-day trial of ZoneAlarm Extreme Security and give ForceField a try that way. Believe me, I checked everywhere, and I could not find a place where I could try ForceField as a stand-alone product.
User Experience
Once you have ForceField installed, there isn’t really much to do. You get a toolbar on your web browser as shown below:
The toolbar only has three function buttons: Protection Activity, Site Status, and Private Browser. They are all pretty easy to use. Aside from these, the only thing you really need to do is just browse the web and the product will attempt to do its job.
Of the three toolbar functions, the least useful is Protection Activity. If your are bored and just curios about ForceField had done for you, click Protection Activity, and you will get information about how much potentially dangerous data ForceField has deflected away.
The next useful tool is the Private Browser function. If the computer you are using is used by others, this comes in handy because it allows you to browse the web without leaving a trace of your browsing activity for others to see.
The Site Status provides a visual indication of how safe the site you are visiting is. If you click it, ForceField will display information about the site you are visiting (e.g. where it is, how long it has been around, and if it is a safe site to be in).
You’ll probably rarely use these, if at all, especially if you are the only user on your computer. With ForceField, you just need to worry about browsing, and it will tell you in very clear terms if you are about to visit a dangerous site.
ForceField put to a couple of tests
To get a feel on how the product handles, I ran the following tests:
- Phishing test
- Spyware/Keylogger test
Phishing Test
Within the last couple of months I’ve received two bogus PayPal e-mails. On one e-mail PayPal is informing me of an issue with my account. This is typical of phishing scams designed to have you divulge your PayPal account information. The e-mail has a link that looks like it will take you to a PayPal page but instead takes you to https://173-29-115-105(dot)client(dot)mchsi(dot)com:84/ which, of course, no longer exists; probably got shutdown as soon as it was discovered. When I clicked this link, I didn’t get anything back from ForceField; I’m not sure why, but I’m assuming it is because it needed to see the page from that site, and when it couldn’t, it had nothing to report. However, the browser itself reported that the URL for the link had a suspicious format.
The other bogus notification from PayPal says that they needed for me to update my PayPal information. This one is a little more interesting as it has an HTML attachment (restore.html), which if downloaded and opened would show a form. The attachment has no virus, but it has a form which if completed and submitted would run a script at https://122(dot)102(dot)5(dot)38/qweasdzxc/libraries/transformations/done4.php. The form asks for everything under the sun: your name, address, credit card, credit card expiration, credit card security code, social security number, and so on–basically everything known to man to help steal your money and identity. When I downloaded the attachment, Yahoo e-mail didn’t detect any virus, and ForceField allowed the file to be downloaded. I opened the file and filled it in with bogus information which I then submitted. ForceField had no reaction to it at all. Again, I’m guessing the site where the script is hosted has probably been shut down. I’m giving ForceField the benefit of a doubt that it is designed not to do anything for a link that leads nowhere.
I really needed to find a real and active phishing site. So I did searches on the web and found one. I attempted to browse it and I got ForceField to respond, as shown in the image below.
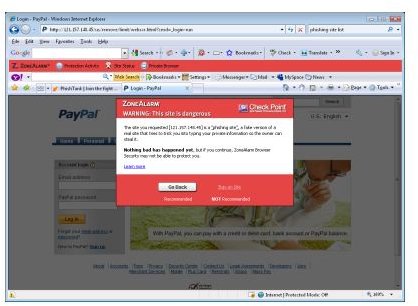
As you can see, it is very obvious with all the red color that you’ve hit a bad site. You have the option to stay at the site, but the default selected option is “Go Back”. I clicked “Go Back” and it gave me this:
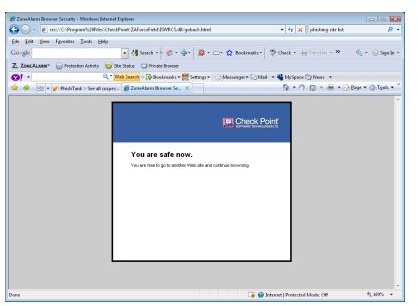
This gave me a sense that danger has been averted.
Spyware/Keylogger Test
To do this test, I searched for a list of known spyware sites. One such site listing these “bad” sites is the Rouge/Suspect Anti-Spyware Sites list. The sites listed purport to provide information and tools to help prevent spyware, but instead infects your computer with spyware. I also found a site that is purported to be a known spyware site–https://www**(dot)brothersoft(dot)**com/keylogger-download-34907.html. I also got a reaction from ForceField on this. See below.
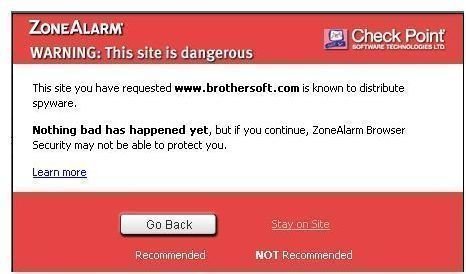
With an “in your face” red alert dialog box, most user will click the “Go Back” button.
The Verdict
ForceField is very easy to use once installed. Basically, once it is installed, there isn’t much left to do, except browse the web with less fear of ending up in a phishing or spyware laden site.
My basic tests seem to show that if a destination link no longer exists (even if it was once a phishing site) ForceField will not do anything as there is no content to scan. For the active phishing and spyware sites, ForceField seem to do the job.
The product seem to perform as advertised, and I would recommend adding it as part of a layered security solution for a computer. However, for what it does and what competitors (like AVG’s Link Scanner, BlueCoat’s K-9 web protection) provide for free, I would have liked to see the product price be less than $20.
