Database Security Concepts | Database Threats | Dealing with Database Threats
Database Security – Scope of Threats
While speaking of database security, the first thing that comes to mind is to protect it from unauthorized users. However, the scope of database security is far wider than just protecting it from unauthorized users. Still, the database security is only a sub domain of the overall computer security. Computer security starts at the root of the individual data expanding to the database, and then to the network that finally expands to the individual computers on the network.
In other words, problems with individual computers or any network device can also corrupt your database. In addition, there are malicious users who can log on to the network and access your database to steal data, modify data, or even delete the entire database. In short, the database is at risk from several angles and any damage(s) can either be initiated due to the ignorance of the user or due to malicious intentions of any person who may or may not be authorized to use the database. While you have to make the database secure so that no one unauthorized can get into it, the accidental damages can be reduced by training the users and imposing penalties on breach of rules such as leaving a system unattended while being logged in.
It is not necessary that only people outside the organization are threats to the database. Even people using the database pose risk to the organization. Some may be selling off confidential data to the competitors for extra income. Others may be helping their colleagues in improving their statistics by altering the data in the database. When it comes to the question as who can be a threat to the database, the only answer is that literally everyone is a threat. Hence, encryption of data is an essential part of database security plans.
Before you create a database security plan, you need to understand the following equation: Important Data + Vulnerability= Threats. Hence, you have to check out the different vulnerabilities while creating a database security plan, some of which are mentioned above. While deleted data can easily be traced, if data is stolen or modified, it can do much damage to the organization before the error is discovered. Your database security plan should also focus on identifying modified data before it creates a disaster.
While there are several components that aid database security, including authentication, authorization, access restrictions, and auditing, we will focus on the primary database security concepts in the following sections. Based on these concepts, you can build the above mentioned aids for use with your database protection plan.
Overview of Database Security Concepts
As the equation specified in section says, the importance of data combined with vulnerabilities is responsible for the extent of threats to the database. While some methods to counter such threats are briefed in the above section, they are not comprehensive. The best method is to check for possible vulnerabilities and create modules to further enhance the security of your database. To check these vulnerabilities, one needs to have an idea of security concepts that are divided into the following categories:
· System Security Concepts;
· Data Security Concepts;
· User Security Concepts;
· Password Management Concepts; and,
· Auditing Concepts.
Once you understand each concept, you will be able to create better methods for authentication, authorization, access restrictions, encryptions, and many more elements that should be incorporated into fool proof database security policies.
Database Security Concepts - System Security
Every organization has one or more database administrators based on the size and number of its database(s). These administrators bear the responsibilities of the database security administrators and have overall access and all rights pertaining to the database. These security administrators create policies so that the database is used in a secure environment. Some of the policies decided and developed by the database security administrators are mentioned in the following paragraphs.
User Management Policy: Under this policy, the administrators have to create user groups so as to allow users to access the database. The policy should also include a <strong>good system of user authentication</strong> using one of the many secure methods. Besides, the user management policy should make sure that the users cannot create, modify, or delete data files that are not related to their logon. This can be achieved by restricting their access to the operating system and network file system.
Tips for Enhancing Security at User Management Policy: The database security administrators should keep a record of user activities. Hence, introducing a logging system is recommended per user. It is also recommended that the user login is deleted on the same day when the user leaves the organization. This needs active communication between the security administrators and the HR. A system of active communication among the different entities of the organization helps in achieving better results for implementing security plans.
The next page details the other modules of the Database Security Concepts at 101 Level.
Database Security Concepts - Data Management
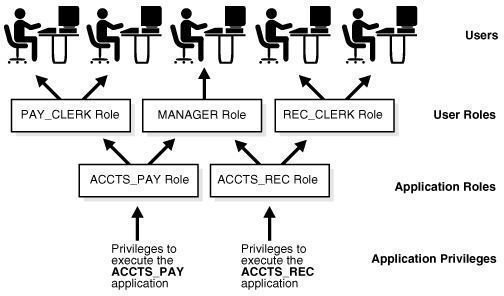
The Data Management Concept decides the privileges of a user account or group, based on their job requirements. These privileges take care of the different types of actions that the user can perform on the database such as viewing only, changing records, or deleting a record. For example, a simple data entry operator need not have access to even view the records. She/he is presented by a form through which she/he enters data into the system. Another example is an employee who needs access to previous records so that she/he can print reports. For this job, the user can be granted view-only access to the required level of database. Data encryption is also considered in this module of database security concepts so that users cannot copy paste data for personal or illegal use.
Tips for Enhancing Security at Data Management: The database has several levels and ONLY the database security administrator should retain rights to these levels. For other users of the database, it is necessary to assess the type of access required. It is recommended not be flexible while determining privileges. The distribution of user rights should be done in a way that the user can access data only from a particular portion of database after caching it in a temporary file until the final operation is performed. Once the action is performed, based on the needs, the temporary file can be used to update the database. This saves your database from any accidental errors.
Database Security Concepts – User Security
Once the user groups are created and rights are granted, the security of the user accounts has to be considered. This can be divided into the following categories: General User Policy; End User Policy; Admin Security; Application Programmer Security; and, Application Admin Security.
The General User Policy defines the database access and modification rights as well as the authentication process. The passwords should be set to expire at regular intervals so that the users are forced to change the passwords. This prevents unauthorized access in case the user leaves the organization and the account is left undeleted.
The End User Policy deals with the privileges that each user of the organization should be offered. While it is more secure to grant privileges at user level, for big databases, it consumes much time. Hence, grouping of users with similar needs is done and privileges are granted per group.
Admin Security comes into picture when the database is very big. Under such cases, the tasks of the database security administrators are identified and accordingly, they are given the roles for better management of the database.
Application programmers may require access to certain portions of the database for fetching data as well as updating, modifying, or deleting data or records. The Application Programmer Policy should decide whether the rights should be given directly to the programmer or should they be processed upon requests received by the database security admin. Though the latter is more secure, it depends upon the type of application being developed. For example, if an application has to access the same portion of database each time, the programmer can be given the rights else it is recommended to keep the rights with the database security admin.
Under the Application Admin Policy, the requirement of application is determined and rights are granted accordingly. In most cases, this is the same as the Application Programmers Policy.
Database Security Concepts - Password Management
This module deals with creation of passwords and storing them with encryption to avoid theft or forgery of the passwords. Blocking the passwords after a certain number of attempts is included here. The policy also deals with retrieval of passwords and changing them under pre-defined circumstances.
Database Security Concepts – Auditing
Finally, there should be a regular process of auditing the database as a whole or in parts at a time. This helps in determining forged data. As said earlier, data deleted can be traced immediately. However, data modified illegally is hard to catch. The process of auditing should be designed in a way that helps in identifying such activities. One method is constant backup of database along with date and time. The audit compares the original database with backups and helps in determining how certain records were changed, thereby exposing frauds (if any).
Using the Database Security Concepts
Now that you have understood the main components that form the basics of database security concepts, you can create a good plan to provide ample security to the database. As mentioned earlier, the security plan works best when all the different units of the organization have active communication. Starting by identifying the critical data and the possible vulnerabilities to the data, you can create measures or policies that protect your data from different angles. A good security plan will also contain a disaster recovery plan in case the original database goes corrupt. You can create continuous backups to different locations to meet this end. External factors such as virus and hackers are also to be considered. These in turn, demand good anti-virus and firewall. You may also customize the database security concepts to produce an effective data protection and integrity strategy.
