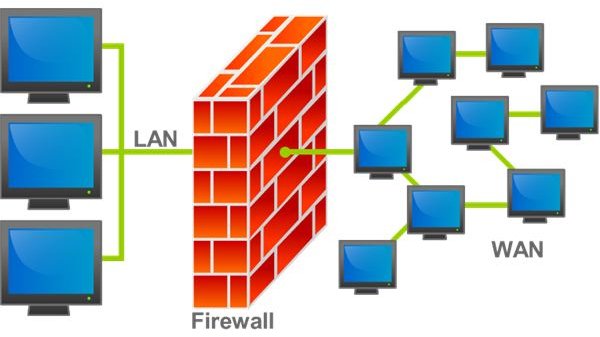
Computer Network Security Problems and Solutions - Possible Threats
Computer Network Security Problems and Solutions - External and Internal Threats
Computer network security problems should be given thought during the planning phase of any network, be it a huge organizational LAN or a small home network. All kinds of computer networks face different types of security problems. Solutions are available for each kind of threat. You just need to understand the threat and act accordingly to reduce, if not eliminate, the impact of that threat.
If you already have a network which you built without a thought on computer network security, you need not worry. It is still possible to reduce the computer network security problems using some solutions after you have created and implemented the network.
Threats to any computer network arise from both external and internal entities. External threats include unauthorized access by outsiders such as hackers, virus attacks etc. Among internal threats is exploitation of the network by its users - knowingly or unknowingly. Internal threats arise due to malicious intentions and/or ignorance of the users of your computer network. For example, a person can leave the computer unattended exposing it to others who are not authorized to access the information. Another example of internal threat can be a person downloading something from the Internet that results in a malware attack.
Solutions to Computer Network Security Problems
This section talks about solutions to computer network security problems when you have an existing network. It also applies to people who are considering building small networks.
First of all, you need to develop a plan to assess the vulnerabilities of your network. A vulnerability assessment plan should cover the key areas that, if affected, can bring down the network or create huge data loss. These items include
1 - Server protection (the main computer in case of peer to peer networks),
2 - Firewalls and antivirus on the server,
3 - The method your server employs to communicate with other computers, and
4 - How other peripherals on the network (computers, printers, etc) can pose a danger to the network.
Please note that this list is not comprehensive. There can be several other points to consider - based on your network type and configuration.
There is some good software available that helps you assess network problems. The software can scan each component of the network and give you a detailed report so that you can work on the vulnerabilities. Some software can go a step further and patch the vulnerabilities. GFI LanGuard is one example.
Creating a vulnerability assessment report is top among the solutions to computer network security problems. Note that performing a vulnerability assessment is not a one-time task. The network admins need to perform the assessment on regular basis. Admins should assess the vulnerabilities and make changes to the network accordingly. After the changes, they should again check for vulnerabilities so that they can better secure your computer network.
The following points offer some more discussion on computer network security problems
- As your server is the main point for data entering and leaving the network, you need to be extra cautious about it. You might need to keep it updated and always patched. Use a reputed firewall that keeps hackers away from your network.
- Use a software that creates log of all the activities on the network. Normally, your firewall provides you with the list of programs trying to access external entities via the server. You can check these logs regularly to study if any program is behaving abnormally, thereby assessing if the server or any computer on your network is affected by malware. The logs also help in determining suspicious user activity.
- The server (the main computer in case of peer to peer networks) needs to have powerful anti-malware. Plenty of free computer security suites are available on the Internet. You may select one from them or go for a paid security suite that contains anti-malware and a firewall.
- As data leaves your server to external destinations, people may be sniffing at the open ports to steal the data. To prevent data theft, use an encryption software. SecureZip is a good program that allows you to encrypt and compress outgoing data packets.
- Check out the peripherals on your computer. If you have printers, scanners and photocopiers on the network, make sure they are not accessible from Internet. To achieve this, place them behind a firewall. You may add them to the network as independent components instead of connecting them to the main computer. Some printers and photocopiers store data to physical disks and thus may leak out data if someone accesses them through the Internet or otherwise. You should also change the default passwords for these devices before plugging them to the network.
- Make sure there is only a single entry and exit point for data to travel through/fro your network. This also means that other users should be able to connect to the Internet only via the main computer or server. Network security is always at stake if people can connect to Internet directly from a local computer.
- Other than the server, you should also have anti-malware on each computer on your network. This makes sure that even if the main computer misses any malware, the other computers can catch it. It is better to have an antivirus on network computers which is different from the one on the main computer or server. However, never install more than one antivirus on the same computer as they may create conflicts resulting in a computer crash.
- Create a user profile for each user of the network. This way, you can avoid using the administrator account all the time. Use the admin account only to troubleshoot, install or remove network components and software. A password of eight characters that contains at least two digits and a special character makes it virtually impossible for hackers to break it.
- Always update the operating systems on all the computers of your network. This helps in further reducing the vulnerabilities as the operating system developers identify and patch any weakness in the operating system.
- Finally, educate the users of the network about possible threats to the network and how to deal with them. The training should include lessons such as scanning attachments before opening them and locking down the computer if a user intends to leave it for a while.
This rounds up our discussion on computer network security problem and solutions. If you have anything to share, please leave a comment.
References
Image from Wikimedia Commons by Bruno Pedrozo
Blogs and Whitepapers from International Computer Security Association, https://www.icsa.net