Conducting Physical Security & Risk Assessments
Physical Threats – Devastating but Remote
Any company can have threats to its existence. Economic threats are the ones that a company usually worries over the most. The nature of physical threats is that they can have a long-term impact. However, you must gauge a physical threat against the likelihood that it will occur. For example, take a physical threat like a fire or tornado hitting the building(s) that house a business; is such a threat real? Possibly, but it is also remote.
On the other hand, some threats, like a break-in, are not as remote; and the threat may not be as devastating as a fire.
To handle physical security and threat assessments, a security engineer should look at how the physical threat could manifest itself. Then he can decide how to address such an issue. In most cases, if the threat is that devastating, then the security engineer should develop a disaster recovery plan.
Image: Petri..co.il.
Physical Threats - Social Engineering
Many infamous hackers tell the story that if you want to break into a network, ask someone with access to let you in. Forget the password cracks or the specialized hardware or software that will allow access–it is easier than that. In other words, the physical threat of a break-in does not occur by stealth, but by invitation.

Social engineering occurs when people perform actions or divulge confidential information by someone “sweet talking” information out of someone else rather than by using some technical hacking technique.
These threats are real, and they more likely to occur because people are too trusting. In that event, the security engineer must make a physical threat risk assessment whether the job or jobs require watchful skepticism.
Image: Noticeboard
See Also: Human Behavior: A Critical Security Threat
Physical Treats - Exposure to the Internet
Another real physical threat can occur through a connection to the Internet. The threat is that a break-in and compromise can occur because the network is open and exposed. This can occur through hackers’ accessing the internal network, or by not having the protection needed even to protect against viruses and malware.
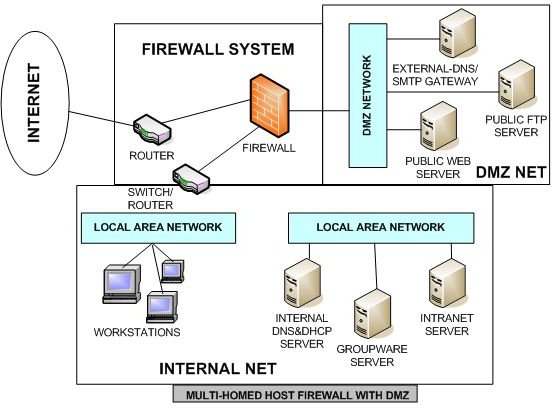
In such a case, the physical threat risk assessment takes the form of what protections are in place; what software or hardware must be available to minimize or block any physical threat.
For starters, a firewall must exist to protect the network from intruders. A demilitarized zone should exist that separates the internal part of the network from the public side. This zone can consist of a firewall, plus a NAT (network address translation) device that converts a private IP address into a public one, and vice versa. This keeps the public away from the internal part of the business network.
Image: Axigen
See Also: A Closer Look at Network Security Threats to Organizations
Summary
Assessments to physical threats depend on the seriousness of the threat and the likelihood of it occurring. Some threats can be devastating to a business, but the chance that they will occur is remote. Conducting physical security threat assessments usually involves a disaster recovery plan as it can focus on the threat and provide a realistic assessment.
A different physical threat comes from the people in the business who are not careful in what they do or say to others or to strangers. Creating a social protocol about how to behave in all circumstances and training personnel on that protocol will help assess the level of risk from social engineering.
Finally, by understanding the physical dimensions and limits of the business network, the security engineer can begin the physical assessment of the risks and exposure of the network.