AccessEnum GUI Provides View into Filesystem Security
The Challenge
You will often run into circumstances where certain files and folders should only be accessed by certain people. This is a valuable tool when it comes to security in the workplace as it prevents just any old person opening up files on your computer and easily stealing valuable information.
System administrators are continuously asked to verify user permissions to specific files and folders. This isn’t always an easy task when looking at a document or collection of documents buried deep within a folder hierarchy. Often, multiple levels of share and NTFS permissions exist, with inheritance adjustments over time creating a security labyrinth. A tool is frequently needed to check the current security posture of a folder or its contents as well as whether it has changed. AccessEnum is a tool that allows system administrators to do this quickly and easily, so you can spend your valuable time on other more important matters.
How It Works
AccessEnum is a free Sysinternals utility, available for download from Microsoft. It provides easy-to-use GUI access to the standard Windows security API. Figure 1 shows the results of a quick scan of my Windows XP SnagIt download folder. The results window columns contain the path scanned and each domain\user with READ and WRITE access. A third column, DENY, is not shown in this graphic.
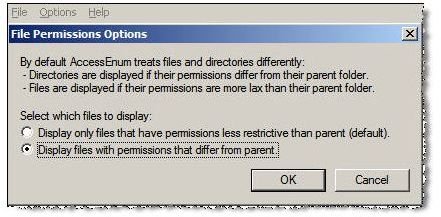
An administrator can change the type of scan via the options drop down menu, shown in Figure 2. An important function is the ability to show how access to the scanned object differs from its parent–a good way to check inheritance issues.
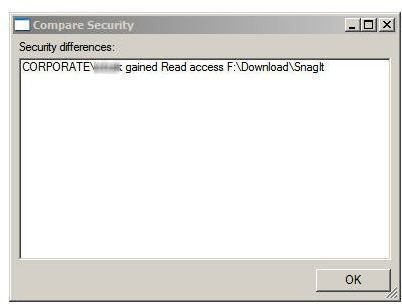
Figure 3 demonstrates the results of another important AccessEnum feature. Administrators and security analysts can use saved scan results to compare previous to current permission settings. And since scan information is stored in text files, it can act as imput to scripts which perform regular checks of folders with sensitive information.
Try AccessEnum to lighten your workload and improve security in your workplace.
Tables and Figures (hover for caption, click to enlarge)
This post is part of the series: Use SysInternals security utilities to manage network and system security
SysInternals provides free security utilities for managing Microsoft Windows networks and systems. Available for download from Microsoft, they provide a powerful set of applications for oversight and protection of network assets.
- Validate System Access with AccessChk
- Streamline Kiosk Operation with Auto-logon
- Enumerate Windows File and Folder Access with AccessEnum
- LogonSessions and PsLoggedOn to Oversee and Manage System Access
- Use Autoruns to Improve Performance and Identify Malware
- Manage, Monitor, and Kill Windows Processes with Process Explorer
- PSExec: Free Security Testing and System Management Tool
- PsLogList: Free Utility to Parse and Review Windows Logs
- Map System Configs with PsInfo
- Use SigCheck to Validate System Files
