How to use PsLogList
The Challenge
Microsoft Windows platforms can generate a large number of Event Log entries, spanning application, security, and system events. And these logs are no different than other sources of event tracking. If you don’t review the information or if meaningful data is not easily extracted, the value of logging to system management and enterprise security is greatly reduced. Since logs are one of the best ways to track real time events and to reconstruct past events, inability to effectively use them is a big gap.
Many log management solutions exist with medium to high price tags. However, PsLogList is a quick and effective way to access and organize local and remote log data. And it’s free.
PsLogList
PsLogList is a command line utility with a long list of parameters, parameters that make it very flexible. The utility’s usage and syntax are shown in Figure 1,
Using this free utility is pretty straight forward. Let’s walk through some examples.
Default (no parameters)
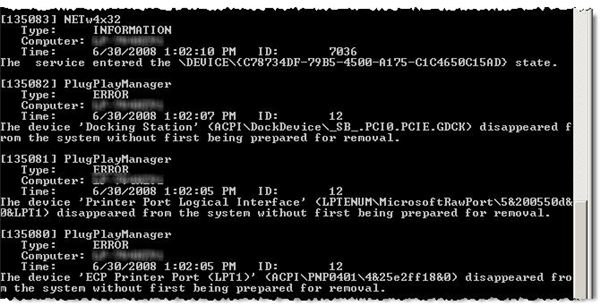
If you run PsLogList with no parameters specified, it automatically selects the System log, listing all entries to your command line window, as shown in Figure 2.
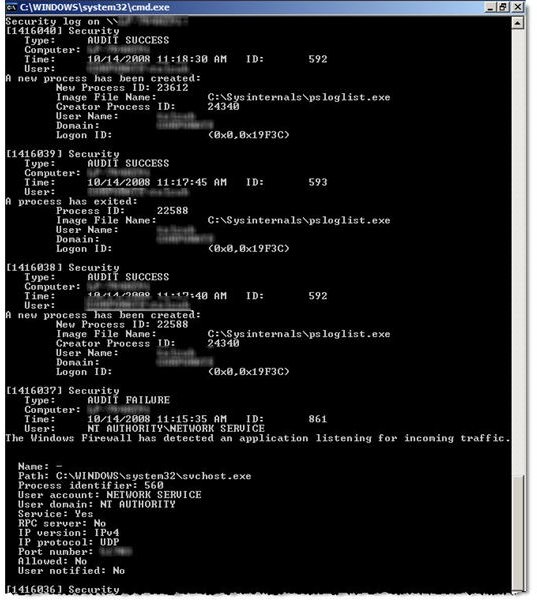
Security Log
Figure 3 shows what happens when you select a specific Event Log. I sent the output to the “more” command to let me page through the results instead of watching them go past in a blur. The command line looked like
PsLogList Security | More
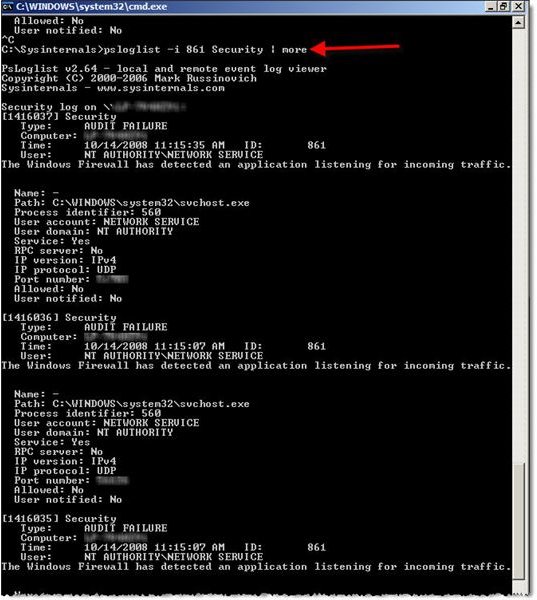
This is great if you want to peruse everything instead of targeting specific events. The following syntax provides a listing of all security log events with an event code of 861, as shown in Figure 4:
PsLogList -i 861 Security | More
Exporting results for analysis
This is all great, but who wants to spend everyday skimming through logs when the process can be automated with scripts or other tools. The following syntax reformats the output into a comma-delimited format and redirects the output to a text file:
PsLoglist -i 861 -s -t , Security > EventListing.txt
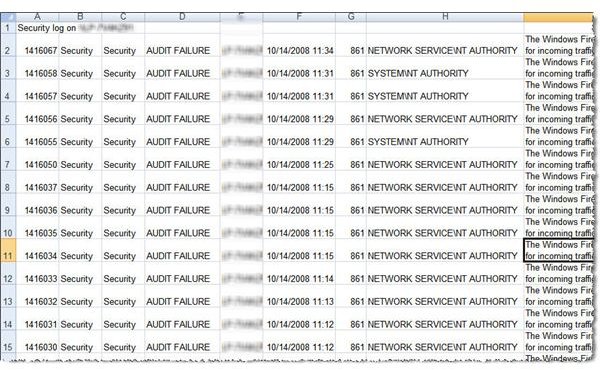
The resulting text file can be imported into Excel, as shown in Figure 5, or used as input for a script.
The Final Word
This is a powerful log analysis utility, especially when used to access remote system logs. It also supports user ID and password strings to access hardened target systems. In addition to checking for system or network anomalies, PsLogList is also useful during forensics analysis, providing a quick look to confirm if one or more users are violating policy and when.
Tables and Figures (Hover for caption, click to enlarge)
This post is part of the series: Use SysInternals security utilities to manage network and system security
SysInternals provides free security utilities for managing Microsoft Windows networks and systems. Available for download from Microsoft, they provide a powerful set of applications for oversight and protection of network assets.
- Validate System Access with AccessChk
- Streamline Kiosk Operation with Auto-logon
- Enumerate Windows File and Folder Access with AccessEnum
- LogonSessions and PsLoggedOn to Oversee and Manage System Access
- Use Autoruns to Improve Performance and Identify Malware
- Manage, Monitor, and Kill Windows Processes with Process Explorer
- PSExec: Free Security Testing and System Management Tool
- PsLogList: Free Utility to Parse and Review Windows Logs
- Map System Configs with PsInfo
- Use SigCheck to Validate System Files