IBM Cloud Computing - Excerpts From IBM Cloud Whitepaper
A Prologue
This article on IBM cloud computing is actually a compilation of important points from a whitepaper on IBM’s Infosphere Guardium. These excerpts from IBM cloud computing show how they manage their clients’ databases so that clients need not worry about their databases once they start using Infosphere Guardium.
In the words of IBM, “More Global (1,000 organizations) trust IBM to secure their critical enterprise data than any other technology provider. The fact is, we provide the simplest, most robust solution for safeguarding financial and ERP information, customer and cardholder data, and intellectual property stored in your enterprise systems.”
The IBM cloud computing whitepaper also says that their security platforms stop unapproved and doubtful activities - be it on part of the insiders having access privileges or hackers. The IBM Infosphere Guardium also monitors your database for frauds by end users of your own company or from the employees who work for other companies. Normally, it would be easy for anyone using the Oracle e-business suite and PeopleSoft to break into cloud-based databases. However, IBM cloud computing is designed to prevent such access attempts. While protecting your databases from unapproved access and hack attempts, Infosphere Guardium optimized operational efficiency with an easily scalable architecture that automates and centralizes the compliance controls across the entire database and associated applications’ infrastructure.
Further, IBM claims that Infosphere Guardium does not have any negative impacts on applications or database performance. It does not require changes to your databases. Another feature of Infosphere Guardium is that it is not reliant on native database logs and audit resources for securing and maintaining your databases
The following section presents the features of IBM cloud computing and the IBM Infosphere Guardium as per the whitepaper.
Features of IBM Infosphere Guardium
As per the IBM cloud computing whitepaper, Infosphere Guardium is the only solution that meets the needs of the entire database security and compliance lifecycle. It come with a unified web console and workflow automation that helps you with many tasks.
Infosphere Guardium features include:
- Helps you search and classify information in the database;
- Assesses database vulnerabilities and configurations flaws;
- Makes sure that the databases are locked after each operation that requires access;
- Offers you an audit trail so that you can get maximum visibility into database transactions;
- Tracks activities on related file sharing platforms such as SharePoint;
- Automates the entire auditing process; and,
- Helps you scale from a single database to protecting several thousands of databases across the world by way of distributed data centers.
The image below, further details the features of IBM cloud computing (click to enlarge).
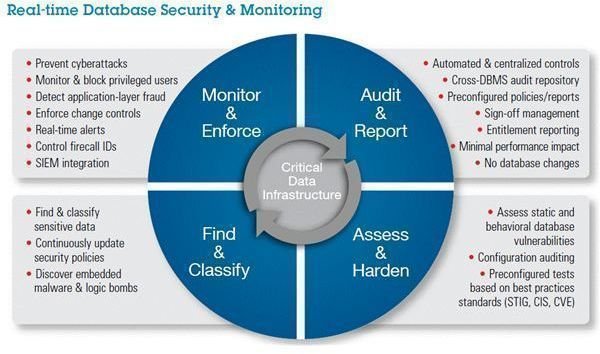
In the words of IBM cloud computing, “Built upon a single unified console and a back-end data store, InfoSphere Guardium offers a family of integrated modules for managing the entire database security and compliance lifecycle.”
The above image divides the functioning of IBM cloud computing into four major parts:
-
Find and Classify
-
Monitor and Enforce
-
Audit and Report
-
Assess and Harden
Securing your Databases with Infosphere Guardium
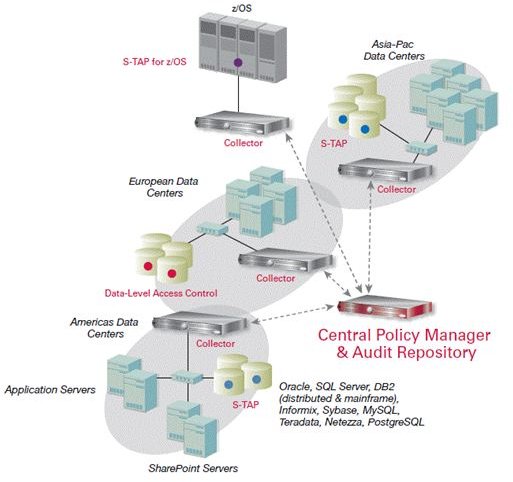
This section talks about the four major aspects of IBM cloud computing as shown in the image on the previous page.
Find and Classify
IBM says if you use Infosphere Guardium , you get resources that help you research and classify information into different data types. It enforces security policies according to the classification of data to make sure that only authorized people can access the data. The database is checked on a regular basis to make sure that all the data is indexed and no data is left out.
Monitor and Enforce
Infosphere Guardium offers you with real time policies that help you in tracing and avoiding unapproved or suspicious activities. These policies are effective for both internal users and external hackers. These policies also track the different applications that access the databases to make sure that no application or the person using the application is trying to access data that the application or user is not authorized to view. These processes eliminate the need of Database Admins (DBA). IBM emphasizes on the term - real time - when referring to these processes and policies.
Audit and Report
Infosphere Guardium offers a real time, regular log of all database activities that can be analyzed and filtered to produce the information required by auditors. These reports help in assessing the security and performance of the databases. For example, one can trace attempts from an unknown user, or an unapproved application to access data. Based on these log files, one can take action as required. The Infosphere Guardium also has a rich set of 150 templates for your reporting needs. In addition to these, it offers the capability to produce custom designed reports using a drag and drop interface.
Assess and Harden
One of the major benefits of using Infosphere Guardium is that it contains a module that continuously scans the entire database for vulnerabilities. This is useful as every database, be it on a local server or on cloud, is open to threats in some way or the other. The Infosphere Guardium process not only scans using a set of industry standard rules, it also offers recommendations to further strengthen the database on the IBM cloud.
♦Image Courtesy: [IBM Whitepaper on Infosphere Guardium](/tools/IBM Whitepaper on Infosphere Guardium).
This was a collection of important points from the IBM cloud computing whitepaper. If you wish to know more, please feel free to leave a comment below for more details. Also comment if you wish to share your experience with IBM cloud computing - whether or not related to Infosphere Guardium.
This post is part of the series: The Best Cloud Clients
This series covers best cloud clients based on the whitepapers released by the related companies. It includes: Microsoft cloud computing, IBM Infosphere, Ubuntu One, Enterprise Vault for BPOS, and Oracle Fusion for building your own private clouds.
