Network Security
Network administrators are in charge of creating and maintaining a company’s network to be safe and secure at all points. If you need something set up or secured, use our guides, tips, and tricks written by experts.

Top Five Network Admin Apps for Computer Network Administrators
Working as a computer network admin means you have a lot of responsibility in keeping your employer’s lines of communication open. Here are five apps that can make your job a lot easier.

Fighting Against Cyber Security Risks
The article highlights how you can make your business network, business devices, and storage all more secure. Cyber security is growing more important are people are sacrificing security for convenience. With these tips, you can bulk up your security to avoid falling victim to a hacker.

Reasons Why You May Want To Use A VPN
Simply put, a Virtual Private Network (VPN) enables remote access to a group of networked computers through a public interface, such as the Internet. VPNs are often used by businesses and schools to grant authorized employees or students access to network resources.

Measures Your Business Can Take to Help Prevent Credit Card Skimming
Skimming is theft of credit card information used in an otherwise legitimate transaction. Very often customers measure the reputation and integrity of a business by the measures a business takes to help prevent credit card skimming and related issues that place the customers at risk.

A Guide to Network Security for the Small Business
Network security is the sum of all policies and measures adopted to monitor and prevent unauthorized access and use of the organization’s computing resources. In the age where security concerns are at an all-time high and attracting front page news, network security becomes a critical function.

Test Your Security Terminology Knowledge!
Are you a network security administrator? Do you know your SNMP from your MRTG? How about your IPS and your IDS? Take this security terminology quiz to see just how much you know in this quiz on security terminology.

Guide to Buying Security Software For the Home or a Small Business
Finding the best security software is not an easy task – you need to know if it’s the right choice and if you are getting a good deal. There are also system requirements to note when choosing software. You’ll save a lot of time if you delve deep into this guide to buying security software.

Do Hacktivists Hack Businesses?
The recent spate of cyber attacks has brought the role of hacktivists into center stage. Hacktivist groups such as Anonymous and LulzSec have claimed responsibility for much of the major high profile hacks in the recent past. But is there a method in the madness? Whom do hacktivists target?
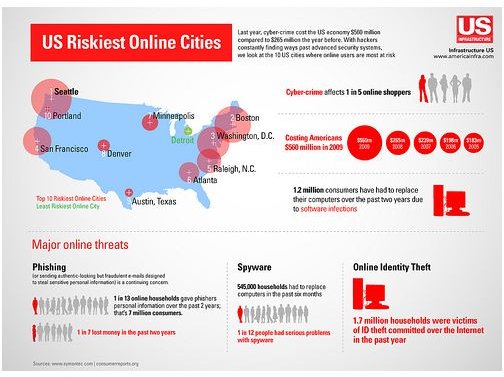
A Disaster Plan for Customer Privacy Rights Breaches
The advancement in computing and networking has made things easy, but also increases instances of cyber crime. Leveraging the benefits offered by technology requires posting and storing sensitive private data online, but cyber criminals stealing such data for their nefarious ends is commonplace.
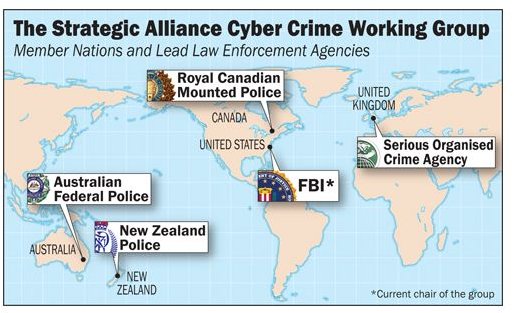
Can the Computer Security Procedures of Forensic Investigations Uphold Privacy Protection?
Find out how computer forensics investigators perform the tasks of building evidence against cyber criminals without having to violate privacy policies. The recent cyber attacks launched against high-profile organizations have renewed the call for upholding privacy policies for data protection.
