Facebook Phishing Tactics - Understand the Various Methods Used by Phishers to Steal Your Credentials
Facebook Profiles
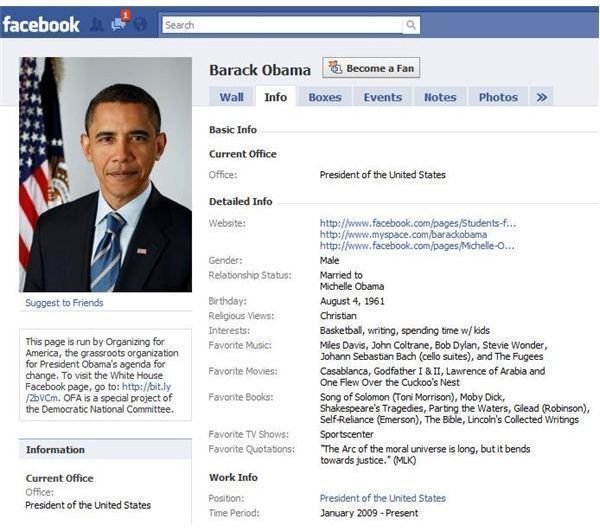
Facebook profiles have allowed phishing to be easier. Many Facebook users have still not set up their privacy settings correctly, allowing strangers to view pictures, names, addresses, phone numbers, e-mails, and any other personal information available. Phishing is easier to perform if the attacker has some baseline information to use to trick a victim into giving up their information.
Facebook profiles can help greatly in spear phishing. Spear phishing specifically targets organizations, or businesses in general. An attack could start by combing through Facebook profiles and finding employees of an organization that a phisher, hacker or social engineer would like to attack. They can find information such as the victim’s job title, work e-mail, and work number. The work e-mail can help in identifying the e-mail naming convention of the company.
Facebook profiles have allowed phishers to gather more information to work with to pull in more valuable information. It is much easier to coax information out of a victim if the phisher can relate to them using information they took off the victim’s profile. It’s also much easier to create a fake e-mail address related to the victim if the phisher knows where the victim works or lives. Even simple profile information such as the victim’s political stance could help create an e-mail that relates to the victim’s core ideas and lead them to a website that will distribute malware, or trick victims into giving up their credentials. Many people also leave their phone numbers on their phone, allowing social engineers to try another trick, vishing, to steal information.
Facebook Groups
Facebook groups are also a new feature that was added into Facebook. People with similar interests or work in the same company could join a group and talk with their peers. A phisher could create a fake account and join these groups and slowly integrate themselves into a position to gather or spread information. If a company is targeted by a spear phishing attack, these Facebook groups offer another opening for phishers to exploit.
A phisher could comb through Facebook profiles to create a fake account that uses job titles of other employees and the same e-mail naming convention used by company employees on Facebook. They can then join the company’s group, which most likely is not being monitored.
Once the phisher has joined the group, they can put up a wall post message stating that human resources has recently released a new, enhanced benefits package, with a link to a legitimate looking webpage. Employees would click the link and enter their company credentials, only to end up on a ‘Work in progress’ screen, while their information has been saved by the fake phishing website.
There are many groups out there that a phisher can join and create fake websites to advertise. Some examples include:
- Volunteering - For non-profit groups organizing events for cancer awareness, autism awareness and so forth.
- Apartments - There are apartments that have groups for residents.
- Utilities - Cell phone companies, water companies, electric companies, they all have groups for fans to join.
- Celebrity Events - Events for celebrities, or fan sites for celebrities.
A fake website asking for log in credentials can be created and shared on any of these groups, and if there is little to no moderation, they can constantly trick victims into giving up their information.
Facebook Applications

Facebook applications have grown to become quite the phenomenon. There are applications on Facebook for all types of users, whether it be games, news feeders, birthday trackers, they’re all available. Most of the time, the danger doesn’t come from the application itself, it’s the actions a phisher can perform around the application to trick users.
One phishing attack method through use of Facebook applications is to create an application that will cause a fake error message on a victim’s Facebook profile. The victim will use a popular search engine such as Google or Bing to determine why the error message is coming up. The very first result is actually a website designed to install malware or to redirect the victim to a fake Facebook log in page, or in some cases, both. The victim is either infected with malware or tries to log in and gives up their credentials.
Another phishing attack method is to combine the attack with spoofing, to create an application that will send out links to friends once installed. The victim installs the application, and the application spreads to friends. The application itself can be a game, but once the victim hits a ‘high score,’ they’re asked if they want to post their score. A fake log in screen pops up and the victim gives their credentials away.
Phishers can also develop applications that run JavaScript behind the scenes. For a split second, when the script loads, it calls to a fake Facebook site, and then quickly refreshes, changing the address bar back to Facebook. The victim doesn’t notice the difference and continues on until a log in screen comes up. The victim enters their credentials, thinking that they were logged out, and gives up his information.
Facebook Chat and E-Mails
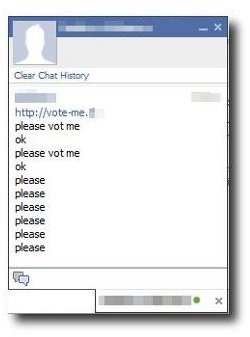
Shortened Chat Message - ‘Vote Me’ ‘Hello’ ‘Check out 121.im’
The latest feature to Facebook is the chat feature. It allows immediate communication with friends like any messaging system. The danger lies in messages from phishers to victims. It can be a simple message with a shortened URL asking the victim to vote for them for an application. The victim clicks the link and ends up on a fake Facebook site, stating that the user must log in to vote. In many cases, legitimate Facebook applications do ask users to log in using their credentials to install or use an application, making this scam that much more effective.
Pleading Chat Message - ‘Help Me’ ‘Need Help’ ‘Robbed and Need Help’
Another new tactic is for a phisher to send a message, acting as a friend, asking for help. They send a message stating that they were recently in another country and was robbed or looted, and need help to get back home. A link to a fake money transfer site or bank is also within the message. Unknowing victims would click the link and try to log in, giving away their bank credentials and allowing a successful phishing attack to go through.
E-Mail Attack
A more recent attack was through the old method of e-mailing users. An e-mail was sent to a Facebook user from a fake e-mail, stating that their password was recently compromised and had to be changed. The victim’s ’new’ password was attached to a document for the victim’s convenience. The document was actually malware, designed to steal the victim’s passwords from their computers.
This post is part of the series: Phishing - Hook, Line and Sinker
Phishing is a constant thorn in security’s side and a constant reminder of how trusting people are, even to anonymous sources. Understand how phishers take advantage by learning their attack techniques and learn how to prevent and protect yourself from being a victim.