Understanding the Scope of Phishing – History and Statistics
Overview and Scope of Phishing
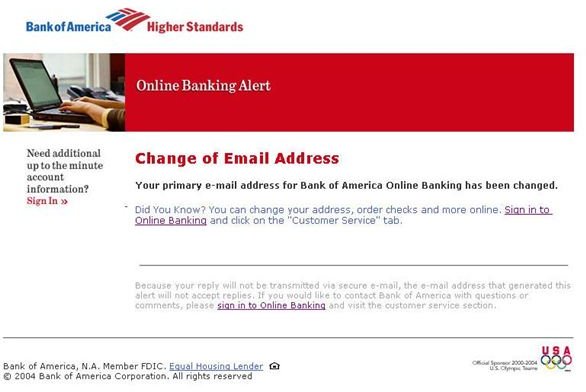
I’ve covered some aspects of phishing in earlier articles (Understanding Social Engineering – Techniques Used and Top Tools to Spot a Phishing Scam) but to recap, phishing is a way for unscrupulous people to attempt to gain user credentials, personal information or money from an unsuspecting victim.
Although it’s extremely difficult to narrow down the amount of damage done by phishing attacks, some statistics have emerged. According to Gartner, the number of victims who lost money due to phishing scams in 2008 was over 5 million US consumers. The average loss was approximately $351 per consumer affected. Some other statistics at popular security company M86 show that 1-2% of all mail are phishing related. They also have a nifty phishing statistics blog letting you know who the top-targeted businesses are along with a breakdown of where much of the phishing mail originates. You can find the info here on M86’s site.
Another useful site is Phishtank.com. They allow users to report phishing attacks as well as getting automated phishing site reports via OpenDNS. As an example of how huge this problem is, the total number of active phishing scans currently is 2,508 (as of this writing). The number of inactive scams is currently over 526,000. You can find more information – including phishes listed by targeted brand here.
Phishing History
Enough with the statistics – where did phishing come from? How did it turn into a cybercrime responsible for millions of dollars in lost productivity and money each year?
In 1997, Tatiana Gau –then vice president of integrity assurance for AOL was dealing with an issue of hackers – sometimes referring to themselves as “phreaks” creating fake AOL accounts and selling them to other hackers. It is believed Tatiana coined the term “phishing” when interviewing for an article with the Florida Times-Union in March 1997. In the article as reported by Ed Stansel, Ms. Gau said “The scam was called ‘phishing’ — as in fishing for your password, but spelled differently.” Hackers would impersonate AOL staff asking users for account information and, trusting as us humans are, they succeeded more often than not in getting the information they sought.
AOL shortly thereafter instituted measures to crack down on the number and ease of setting up “phish” accounts. After the hackers were turned away from AOL, they realized quickly they could use the same technique against financial institutions.
According to Wikipedia, one of the first phishing examples that targeted a financial system was E-gold in June of 2001. As time marched on, hackers were able to very successfully emulate the look and feel of emails so they looked like they were indeed originating from a specific institution. In the early phishing time frame (2001-2003), most emails were sent blindly to large email lists. This was referred to as “whale phishing” – you send out a bunch of emails in a huge net and hope to catch a few small phish. With today’s sophisticated technology and the ability for people to look up previously private information, phishers now target select groups of people. For example, when targeting a bank, it doesn’t make sense for a phisher to send out emails to people who don’t have bank accounts with that institution. They now perform “spear phishing” targeting emails to only those people who do have accounts at the targeted bank. Today, most phishing scams still target banking institutions but social networks and other premium paid sites are targeted as well. With a little bit of technology and common sense, it’s relatively easy to not get trapped by the phishers.
The following sources were used to write this article: