How to Identify and Remove a Conficker.B, Conficker.C or Downadup Worm Infection
Update: Jonathan Leopando of Trend Micro writes, “In a very real way, threats like [Conficker] become part of the background noise that is a part of life on the Internet.” Current estimates are that between 1.25 and 5 million systems remain infected. Conficker has also “built a botnet” in order to function for its creator. Roles for the ‘bot include spam, denial of service attacks, and antivirus spoof malware (or fake antivirus).
Concerned that your PC may be infected by the Conficker or Downadup worm? Here’s a simple test. If, using Internet Explorer, you can visit Yahoo! and Microsoft, your computer does not have the virus. Since “microsoft” is in the list of website “strings” blocked by Conficker, if you can visit Yahoo! and not Microsoft, it’s likely your PC does have the virus.
And as a note, if your computer is infected and you think you can live with the inconvenience of not being able to reach certain websites, remember that Windows Update, Windows Defender, and the Malicious Software Removal Tool are also disabled, effectively leaving the barn door open for more, and perhaps more efficient or more malicious software.
If you’ve come here because you are concerned that you may have an active Conficker infection, please read the first part below about how the worm spreads and then go to the second page for some advice and links to remedies.
Update: May 2, 2009. Atif Mushtaq of the FireEye Malware Intelligence Lab says that Conficker is not behaving in the furtive manner in which a notorious botnet might be expected to act. “The creator of the worm has only been in direct competition with security researchers. Due to the method of propagation, and the lack of a working dynamic update mechanism, the AV industry hasn’t had a problem keeping up with the different binaries.”
Update: April 1, 2009. The midnight hour of March 31 has passed, and it’s now April 1, April Fool’s Day. So far things are quiet. According to F-Secure, infected computers have activated and begun to “phone home” to Conficker’s remote master(s), but so far no further malware activity has been detected. Could this be like the big 2YK scare that fizzled into unimportance even before millennial hangovers eased? There’s no evidence so far that the worm has mutated. All indications are that the preventive and corrective measures already known will continue to function.
Update. March 31, 2009. Within 24 hours, we should learn what the purpose of the Conficker.C or Downadup worm is. Security experts tell us that it should contact its ‘bot masters at up to 500 of 50,000 estimated possible websites and take on its payload, whatever that is.
One Scenario: How to Get Your PC Infected by Conficker.B or C
It’s Friday evening. Ted is clearing his desk, folding work that’ll keep until Monday, into a side drawer. Some other stuff that he’ll look at over the weekend has already gone into his briefcase. He bends down and presses the power button on his backup power supply and listens as the fans and hard drives of his PC spin down. Suddenly, it seems very quiet in his office.
He puts on his overcoat, grabs his hat, and picks up his briefcase. Then he pauses, wondering what he’s forgotten. He stands hesitantly before his now well-ordered desk and sighs as his phone rings. He sets down his briefcase, presses the lit button on the phone, and says, “Hello.”
“Hi, Ted. I’m glad I caught you still in.” It was Marsha in Accounting.
“HI, Marsha,” says Ted. “I was just leaving.”
“I have those figures you asked for on the Sherman liquidation. Want me to email it to you or send it to the printer?”
“Great.” Ted considers. “Let me come over, and you can give it to me.”
“Okay.”
Ted leaned over again and pulled his thumb drive out of his quiescent PC. He slid it into a coat pocket, picked up his briefcase, and made his way to the Accounting Office on the second floor.
He saw with some approval that Marsha’s office space was clean and organized. A veteran PC that had seen better days thumped and hummed on her desktop. A closed Apple Macbook was at her elbow. Ted held out his thumb drive.
“Thanks,” said Marsha. She inserted Ted’s thumb drive and started to save the spreadsheet from Microsoft Excel to the drive.
Unbeknownst to both Ted and Marsha, the spreadsheet file was not the only payload being transferred to the thumb drive. A stealthy trojan known as Conficker.B or Win32\Downadup also transferred itself when the thumb drive was inserted. It also created a new autorun.inf self-starting file to install itself on the next vulnerable PC that it found.
The next PC it found was Ted’s laptop. The trojan tried to install itself, but the laptop had obtained a Windows update back in October, 2008, was running anti-virus, and the trojan could find no purchase. Although Ted viewed the spreadsheet and saved a copy to his laptop, he did not find out that his thumb drive was infected during that weekend.
In fact, the next vulnerable PC the trojan found was Ted’s PC at work on the following Monday. The trojan moved to Ted’s PC when he inserted the thumb drive in order to work with the spreadsheet some more.
Bob, the Information Technology director at Ted’s company, was responsible for maintaining over five-hundred PCs and laptops on the company network. He wanted things to go smoothly, for all those PCs and the machines in the company’s server closet to just work and not take up an unwarranted amount of his time or thought.
Bob had not made it in to the office by the time Ted managed to infect his office PC with the Autorun application that the trojan installed. Part of the control that Bob maintained over the system involved never shutting the systems down. He viewed Windows Updates with a strict, unwavering suspicion. Ted’s company had never deployed the October update that would prevent the trojan from taking advantage of the vulnerability in Windows.
So while Bob was still driving his Volvo toward the company campus, Ted started to work, the servers in the air-conditioned closet hummed and blinked, and Marsha placed her Macbook on her desk and started up her company PC.
After Ted inserted his thumb drive, Windows popped up a dialog, and Ted selected “Open folder to view files.” Everything looked perfectly normal, but the trojan had actually created the entire dialog. When Ted selected view contents, he gave the trojan permission to install on his PC.
The little trojan robot then went to work trying to guess Ted’s network password. It also attempted to protect itself. It checked to see if it could turn off Automatic Updates, which of course, were not enabled on Ted’s company-network-connected PC. It also tried to turn off Windows Defender (not used, either) and Error Reporting Services. While it was at it, it configured Internet Explorer so it could not visit computer security sites like kaspersky.com and symantec.com.
All of this happened in the background. Ted remained blissfully unaware that he had a problem at all until the following Monday, when he powered up his PC and found that he could not log in. He even double-checked his password, which was taped to the bottom of his telephone, but the trojan had finally figured out Ted’s password (“maria83moncheri") and was busy rampaging across the company’s network. Bob in IT would soon be busy.
How Conficker or Downadup Work
Though fictionalized, the preceding story does illustrate what we know now about the way that the Conficker, aka Downadup, worm propagates. One method is through exploiting a vulnerability in the file-sharing services (SVCHOST.EXE) in Windows 2000, Windows XP and Vista. This is what the October, 2008 Microsoft patch MS08-067 was aimed at. (The Windows 7 beta version is already patched.)
Another method is through brute-force guessing of passwords to enter network shares. A third method is through Autorun/Autoplay transmission from USB-based hard drives and thumb drives. MP3 players and USB-connectible digital cameras may also be a vector.
Even worse, on the millions of PCs that Conficker has already infected, it has not yet been activated to carry out its real purpose. In other words, it’s like a loaded gun that nobody has pulled the trigger on yet. What that real purpose will be – relaying spam or downloading more malware – only the malware designer currently knows.
Next: How to Determine if Your PC is Infected, How to Remove Conficker.B, and How to Prevent an Infection
How to Determine if Your PC is Infected
Microsoft says that there are common symptoms that are consistent with a Conficker.B worm infection.
The following Windows services will be disabled or fail to run.
- Windows Security Center Service
- Windows Update Auto Update Service
- Background Intelligent Transfer Service (BITS)
- Error Reporting Service
Users may not be able to connect to security-related services containing any of the following strings in the URL:
virus, spyware, malware, rootkit, defender, microsoft, symantec, norton, mcafee, trendmicro, sophos, panda, etrust, networkassociates, computerassociates, f-secure, kaspersky, jotti, f-prot, nod32, eset, grisoft, drweb, centralcommand, ahnlab, esafe, avast, avira, quickheal, comodo, clamav, ewido, fortinet, gdata, hacksoft, hauri, ikarus, k7computing, norman, pctools, prevx, rising, securecomputing, sunbelt, emsisoft, arcabit, cpsecure, spamhaus, castlecops, threatexpert, wilderssecurity, windowsupdate
In a company network, domain controllers may respond slowly to client requests, and users may notice excessive network congestion.
How to Remove Conficker
To remove the worm, one needs first to install the October patch from Microsoft that closes the vulnerability. Since Microsoft websites are in the list that the virus blocks, you’ll need to do this from an uninfected machine. Then go to this page and click the name of your operating system to download the correct version of the tool. Select SAVE when you download it. I suggest that you consider burning the update file to read-only media such as a CD or DVD. Transporting it via a USB thumb drive or USB hard drive is definitely not recommended as one could get into an “infect me, disinfect you, infect me, disinfect me, infect you” sort of vicious loop.
For Conficker.B:
After you’ve downloaded the patch, go ahead and get the Malicious Software Removal Tool as well. You can download it here. Install the patch first by running it directly from the CD or DVD, and then run the Malicious Software Removal Tool the same way to remove Conficker. (Bright Hub also has detailed information about how to run a deep scan using the Malicious Software Removal Tool as well as Windows Defender.)
For Conficker.C:
If you are unable to run the Malicious Software Removal Tool, it is likely that Conficker is preventing it from starting. This indicates that your infection is of the .C variant. For this one, we suggest using the Symantec removal tool released on March 30, 2009. It works on all three variants. As with the Malicious Software Removal Tool, you’ll need to download the Symantec tool on another computer and, preferably, run it from read-only memory like a CD or DVD. Then run the October 2008 patch from Microsoft to close the vulnerability.
How to Prevent an Infection
Other than choosing strong passwords for your network access, running name-brand antivirus, and keeping up-to-date with Windows Update, what else can you do to prevent an infection by Conficker/Downadup or similar viruses?
Since one vector that Conficker uses is through Autorun/Autoplay, you can decrease your chances of getting this and similar future viruses by disabling Autorun and Autoplay on your PC, at least for USB drives. The best way to do this depends on the version of Windows you have.
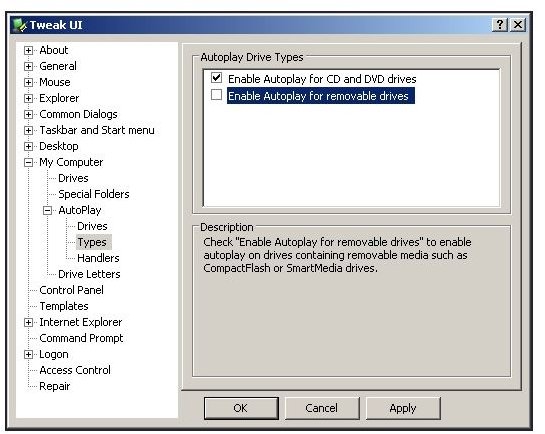
Windows XP Home Edition
The TweakUI “Power Toy” utility from Microsoft is an easy way to disable Autorun in the Windows XP Home version. After downloading it and running the installer, go to Start → All Programs → Powertools for Windows XP → TweakUI. In TweakUI, go to My Computer → Autoplay → Types in the left-hand pane. You’ll see two options: “Enable Autoplay for CD and DVD drives” and “Enable Autoplay for removable drives.” There are a lot of other neat tweaks to explore in TweakUI, so feel free to explore. Remember to click OK when you’re finished.
Windows XP Professional
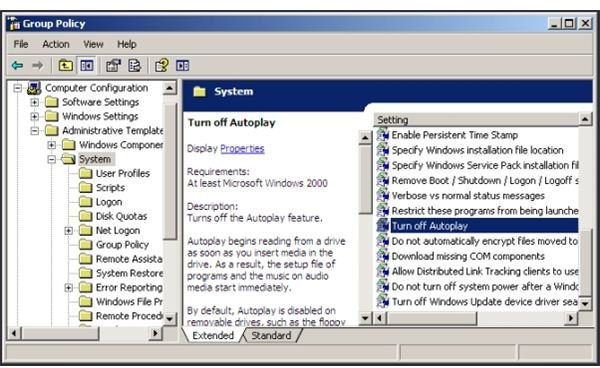
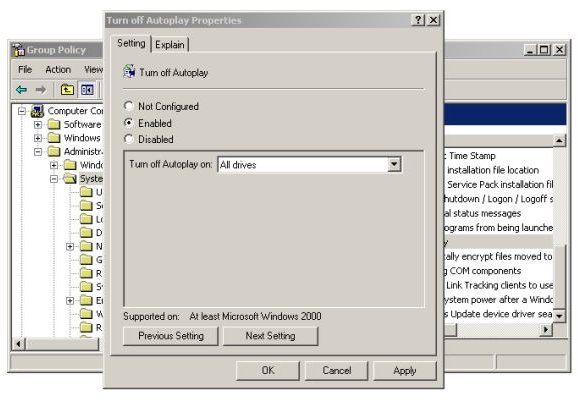
TweakUI, as mentioned above, also works with XP Professional (and is great fun to play with). However, disabling Autorun can also be done with the Group Policy Editor. To run it, click Start → Run and type in “gpedit.msc” and press Enter. Under “Local Computer Policy,” select “Administrative Templates.” Then select “System” and scroll down in the right-hand pane. Find and click “Turn off Autoplay.” Read the information in the new middle pane that appears. When ready, right-click “Turn off Autoplay” and select Settings. You’ll have the choice of turning off Autoplay for “All Drives” or just “CD-ROM drives.”
Removable drives were not much of a big deal in Windows XP days, so you may prefer the options in TweakUI over using the Group Policy Editor.
Vista Enterprise, Business, and Ultimate
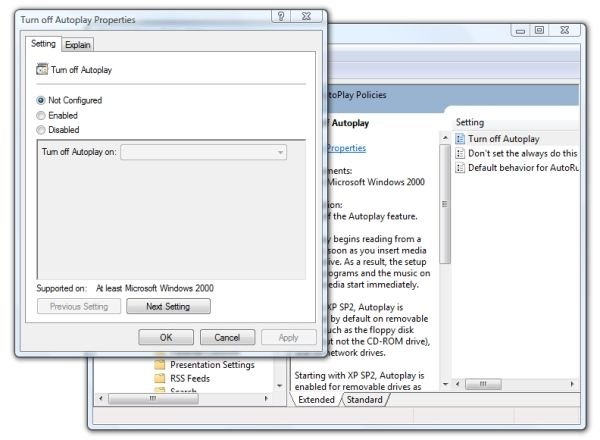
These editions of Vista contain the Group Policy Editor. The steps are the same as for Windows XP Professional above, except that you can type “gpedit.msc” directly into the Vista Start search bar and the path is Local Computer Policy → Administrative Templates → Windows Components → Autoplay Policies. Right-click “Turn off Autoplay” and select Properties to change the settings.
Vista Starter, Basic, and Home Premium
The versions of Vista lack the Group Policy Editor. The closest you can come to disabling Autoplay for thumb drives and external USB hard drives is under Start → Control Panel → AutoPlay. There you can unselect “Use AutoPlay for all media and devices.” Then click “Save.”
Conclusion
When the big security houses first alerted about the Conficker/Downadup trojan, it was moving rapidly through China and Brazil. These were locations where many users might not have legitimate, licensed copies of Windows. Therefore, they were unable to obtain automatic updates from Microsoft.
The movement in the US and Europe is less likely to be happening because of the lack of Windows updates (except for at Bob’s company. We hear he’ll soon be looking for a new job). However, the triple attack vector – network shares with weak passwords, the SVCHOST.EXE vulnerability, and the Flash drive transmission route – are letting the virus have some success in the US. How bad it will get remains to be seen.
US-CERT (the United States Computer Emergency Readiness Team) recommends a further step to avoid all possibility of having Windows parse (read) an autorun.inf file from removable media. They suggest modifying a registry key that tells Windows that an autorun.inf file does not exist on the inserted device. More information about that can be found here.
Finally, Symantec has made available a free “Win32\Downadup” removal tool. You can find the specific directions to run it and a download link here.
Thank you for reading this, and thanks for visiting Bright Hub.