Build Your Own Firewall Step by Step
DIY Firewall: Where to Start
Numerous firewall options exist on the market, yet you’ve heard or discovered that it’s possible to construct your own firewall from off-the-shelf hardware and Open Source software. Some commercial appliances even base their software architecture on the Open Source firewall elements available, so you believe (accurately) that it’s possible to create a robust and secure network firewall on your own. Thoroughly understanding firewall design, architecture, and implementation is an expert’s task, yet we can use readily available tools and some straightforward best practices to create a working and secure solution ourselves. Engineering and deploying firewalls created from scratch will take more time and effort than installing a commercial product, but the result can be optimized and tuned for your particular technical needs. Furthermore, you’re likely doing it because of the challenge or just for enjoyment of doing it yourself! Let’s take a look at the requirements.
Hardware Requirements
Most modern PCs have far more than enough RAM, CPU speed, and I/O performance to work as a firewall for all but the largest or heavily trafficked networks. Many large businesses did use off the shelf servers as their firewalls–I’ve worked at some of these companies and seen many such firewalls. A bargain PC won’t be your best choice, however, for a couple of reasons. First, you will want to be sure that the motherboard has a high-performance bus controller and that there are enough expansion slots to accomplish what you want. A single free PCI slot simply isn’t (usually) enough. Few expansion slots is often also a sign that the system wasn’t designed for a long life and constant use. Less expensive motherboards simply are more likely to fail, and you don’t want the system burning out in 6 months! Power supplies are another cause of failure, you will want a sturdy power supply that exceeds the minimum needs, provides very reliable output, and will have a long life–it’s going to be running all the time.
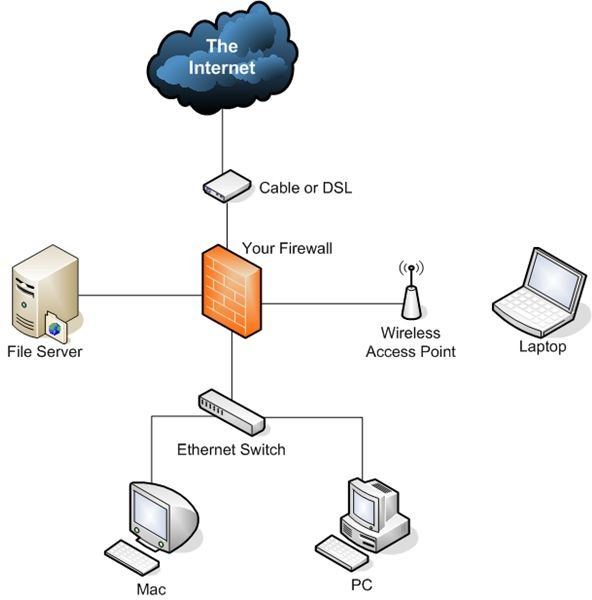
Next you should consider network interface (NIC) options. Most of the time your motherboard will have a single 10/100baseT Ethernet interface already built-in. This can either be a good thing or a bad thing. Sometimes these provide good performance–other times I’ve found they weren’t as good as my added cards. The main point here is that you will want one network interface for each physical network: two at a minimum. One for your internal (or protected) network, and another for the external (or Internet) network. As you’ll see in the design section, this is the minimum; you may want or need several more NICs. If you don’t have that many expansion slots on your motherboard bus, there are cards that have multiple Ethernet interfaces on a single card (two, or even four). While this may seem like a neat idea, I don’t usually recommend it because if that card fails, two (or four) networks go down rather than just one. Will you be able to replace a four-port card quickly if you don’t own a spare? If you are trying to imitate one of the small appliance firewalls, you’ll note that they often just have a single four-port Ethernet card, so it’s not a horrible idea–just one that isn’t ideal. You may want to use a gigabit (1000BaseT) Ethernet interface for your internal networks if you want or need the higher throughput. Home users might consider a Wi-Fi adapter for the internal interface since they may not have or want cabling connecting the firewall to the ideal spot for their wireless router or hub. Routing can become complex, and we’ll need to cover that in a follow-up article.
Software Components
First you will need to choose an operating system platform for your firewall. Windows is a possibility, but most all of the Open Source firewall applications were designed to run on Linux (or other Unix variants in some cases). Some free firewall packages include the base Linux OS and install completely, without the need for selecting, downloading and installing or compiling individual components, configuring Web management or other controls, and so forth. This can be a big time saver and there are several excellent choices, such as Untangle’s free version (more on Untangle below).
The firewall components and applications you require include a core routing and protocol filtering component, which also can provide network address translation (NAT) functionality. TCP and UDP protocol management beyond basic port filtering is important as well, allowing or restricting particular applications or functions. An interface for creating and managing these rules, usually a Web interface for ease-of-use is also needed. These are required components for any system calling itself a firewall. Firewalls go far beyond this basic functionality, however.
Almost all current firewalls provide virtual private network (VPN) functions. The firewall acts as a VPN endpoint and the rules component helps manage what remote VPN users or sites can and cannot access on the network. Intrusion Detection & Prevention (IDS/IPS) and reporting functions are key components as well. Good reporting visible via a Web interface, and with alerts sent via email is very important. A full-featured intrusion detection system (IDS) like Snort is a great component to integrate, see more about Snort in my review article here. Anti-Virus, other anti-malware, anti-spam and related components can be added, taking some of the burden off internal servers and PCs to protect themselves. Many choices for these components
Check out this review of Untangle to see what their Open Source package has to offer for your firewall. If you don’t want to assemble all the components yourself this is a good choice. Untangle’s base package includes 12 Open Source firewall applications. These free applications provide more than the minimum firewall components, including anti-malware, anti-Spam, IDS, VPN and reporting functions. Advanced networking features including QoS and Voice over IP support provide tools for or ensuring bandwidth is available for sensitive applications such as VoIP) are present and easy to access and configure. Untangle’s web management interface for these security apps is easy to learn and understand. Untangle also offers Untangle for Windows, a free firewall package which runs on a Windows XP computer.
Design Example
Design, Configuration & Testing
Firewall packages and suites of applications can be placed in your existing network behind the Internet router, cable modem or DSL device. Many of the firewall routing designs (especially on Linux, using IPFilter) can use what’s called transparent bridge mode, which requires no changes to your network’s routing or IP configuration. If the existing network configuration or the planned configuration does not include a subnet or block of assigned IP addresses from your Internet Service Provider (ISP) or a device providing Network Address Translation (NAT), you will need to either request a block or range of addresses, or configure NAT on the firewall, (or both). Usually home users have NAT already functioning on their DSL router or broadband device/cable modem, and IP address ranges are not an option. If you are a small business and have a T1 or similar network connection, you already likely have the IP address information you need.
It’s a good idea to create a diagram of the network now, and what it will look like after the firewall is in place, and also to make a list or spreadsheet of the rules that you will need in place for your applications and users to be able to do what they need to do. This can make it much easier to create or rebuild the configuration if you need to, and to visualize what may be wrong if something doesn’t work. If you are working on the project for home use, you can likely create your rules, application protection settings, the rest of the firewall configuration, and put it in place to test what you’ve done as you go. For businesses, you will want to set up a test network and work out problems in advance before putting the firewall in place.
Extras & Next Steps
As we discussed earlier, additional network interfaces allow you to separate protected areas into distinct physical networks, or perhaps add a Wi-Fi zone as a DMZ at your home or work, with separate rules and additional protection. It’s even possible to configure two firewalls in a high-availability (HA) configuration, where if one crashes or is off the 2nd keeps the network and protection up and running. You can also set up multiple protected servers in a cluster or “pool” with a single name and a virtual IP address (VIP) that load balances between them. These are advanced topics, but are all possible with the DIY firewall you are constructing.
Next Steps
Well, that should be enough to get you started–your next steps are to decide what you need, get it, and begin building your own firewall!