10 Common Intranet Security Issues: Is Your Business At Risk?
The Purpose of an Intranet
An intranet is much different from an extranet and the Internet. It is a private network for a small collection of users like employees which have been granted permission by their organization to access the Web, email, and other information services found on the Internet. An intranet is intended for small-scale operations, but it has proven useful for collaboration and sharing resources like computer data, network applications and sharing information among employees. There are other intranet benefits as well, such as saving a business time and money when using one.
*****For those people who are still uncertain why an intranet is important to business, check out this article, “The Purpose of an Intranet.”
According to Oracle, an “Intranet is a network that is “owned” by a single organization that controls its security policies and network management.” [1] In short, it fulfills data and information management requirements. It is deployed for internal users and not external users who are on the outside of the private network, like business partners or other businesses. However, such users can be granted use of an intranet if an organization permits it.
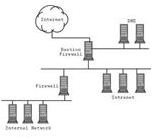
Often, for security reasons, an organization will deploy a demilitarized zone, or DMZ, which is a computer or small subnetwork to protect internal, private networks from being accessed by external users (see image). In addition, an organization may segregate the applications in the intranet, which are on internal severs, from other network systems through the use of firewalls to increase internal security. Firewalls are useful in an intranet for filtering traffic and to effectively manage and control network traffic, but as with any network system (like an extranet), an intranet creates risks and has intranet security issues (as shown in the next sections of the article).
Image Credit Sun.com
10 Common Intranet Security Issues
Here is a list of 10 intranet security issues and what a user and organization do to resolve them:
1. Network security threats. Internal and external threats are common. Some are deliberate threats while others are not. It’s best to use a firewall and some sort of security software like McAfee Network Threat Response.
2. Security breaches. There are times when an intranet will encounter suspicious traffic, such as spam, phishing, spyware, adware and malware, so deploying an effective email filter (and firewall) can help block the suspicious traffic from entering the network.
3. Network attacks. There have been several cases reported of an intranet being attacked. A network-based intrusion prevention system (IPS) or an intrusion detection prevention system (IDPS) can offer great protection. They also can be deployed for monitoring network traffic and detecting and preventing well-known threats and attacks.
4. Unauthorized access. This happens much too often when an internal or external user (not authorized) gains access to data and corporate information stored on an intranet. It may be wise to use some type of authentication like passwords, smart cards, or biometrics; in addition, to deploying a bastion host before a user has access to the intranet.
5. Misuse of user privileges. Too often are users gaining unauthorized access to systems from the Intranet. Businesses may want to use some type of intranet monitoring software to see what their employees are doing on the intranet or on their own PCs.

6. Violations of security policies. At times, users will make illegal attempt to penetrate the network without clearance and permission. Internal users must understand what happens when someone violates the policy in attempt to protect internal IT systems on the intranet.
7. Malicious content. Intranet users are vulnerable to malicious content (viruses, worms, and Trojan Horses) that attach themselves on emails. Businesses and users alike must remember to always maintain and update their security software on every PC and server on an intranet to ensure protection.
8. Usability problems. There are users who still improperly use the intranet. They do not know how to search, retrieve, send or share data and information; often, doing more harm than good on the private network. Some users may need formal training.
9. Weak passwords. Users tend to use weak passwords, write down passwords, never change them, or forget them. Network administrators must encourage users to overcome these issues and have them use hard-to-guess passwords, as well as not to share them, or write them down.
10. Lack of encryption. Many times unsecured “confidential” data is shown to unauthorized users because they do not use encryption. Using SSL digital certificates can help secure the Intranet.
Intranet Tip: Set up firewall rules to allow only those messages that originate from the internal server.
Advice: Any person granted access to an intranet should receive formal security training first. Users need an IT security policy handy to know what to do when there is a security violation, a security threat or attack, or learn how to resolve all other intranet security issues such as those mentioned above.
Solution: Businesses can set up on their own intranet and choose a software solution like Office Ability to overcome some of the common security issues like usability problems, passwords, and encryption, or use HyperOffice, which is a business that offers their own “Securely Hosted Intranet Software Solution” for other businesses.
Image Credit - MorgueFile
Resources & References
[1] Network Considerations: https://download.oracle.com/docs/cd/A97335_02/apps.102/a86202/chap09.htm
- Intranet Journal - https://www.intranetjournal.com/features/isecurity.shtml
- Windows Securit Whitepaper - https://www.windowsecurity.com/whitepapers/guide_to_securing_intranet_and_extranet_servers.html
- Sun - https://www.sun.com/software/whitepapers/wp-security-intranet/protectingfromwithin.pdf