Removing Trojan Horses: How to Get Rid of the Amazon EC2 Zeus Trojan
Amazon EC2 and Zeus Trojan
Amazon Elastic Compute Cloud or (EC2) is a web-service to provide virtual computers to developers and professionals and is used as a command and control center for the purposes of a botnet. The report was found by researches of CA Technologies, the makers of CA Antivirus software.
Zeus is known as the King of Crimeware toolkit as per Symantec, and has performed these types of attacks in the past and continues to be in the wild. Zeus Trojan is also known as Kneber, Zbot, PRG, Gorhax, and Wsnpoem by several antivirus vendors. The crimeware toolkit, Zeus is sold to attackers who want to steal valuable information from Internet and computer users. It spreads using email as spam or phishing and drive-by downloads.
An example of the Zeus Trojan distribution is used by sending a fraudulent Facebook, IRS, Microsoft emails or messages with the intention to fool recipients in installing the Trojan or entering personal information such as credit cards, full name, social security number and medical ID numbers. Some reports by antivirus malware research teams are that Zeus can be distributed by visiting websites that were compromised or created. Drive-by downloads are a method by attackers to spread the malware by taking advantage of vulnerability of platforms; for example, browsers, forum software or any software that is not up-to-date, and does not have security updates installed.
Removing the Amazon EC2 Zeus Trojan
The Zeus or Zbot Trojan is not easily detected or prevented by antivirus vendors, especially if the malware is new or a variant. Below is an example of the said Trojan that I tested, by infecting a test system.
The malware executable adds a start-up item, fyvue.exe in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. The Zeus Trojan installer also created a folder in the user accounts Application Data directory:
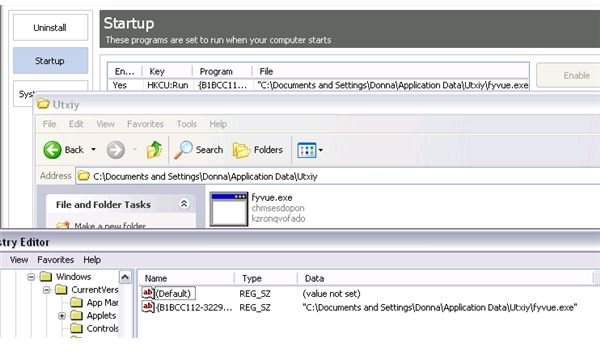
This type of malware is easy to remove, only if you are familiar with the above locations and filenames or folders. Manually deleting Trojan files is recommended only if you know where it hides. The problem is not all antivirus and anti-malware programs can detect all types of threats, especially if it’s a new version, or what we know as variants of malware.
I uploaded the fyvue.exe in a VirusTotal online virus scan service to find out how many antivirus vendors would be able to detect the files added by a Zeus Trojan, which had also been known to affect Amazon web-services. The result is that only 55.8% provided detection or removal of the malware. That’s not good news since 19 out of 43 anti-malware vendors will fail to protect end-users, and in a worst case scenario, the cloud, and business users that depend only on single protection tools could also be infected.
Using Online and On-Demand Scanner
If your antivirus program doesn’t protect the computer from all types of threats, it is wise to regularly scan the computer using on-demand or online scanners. In the above example, if you are using an antivirus program that failed to detect the raw file and processes that were added by the Zeus Trojan installer, you should run a scan using other scanners. Example of these scanners:
-
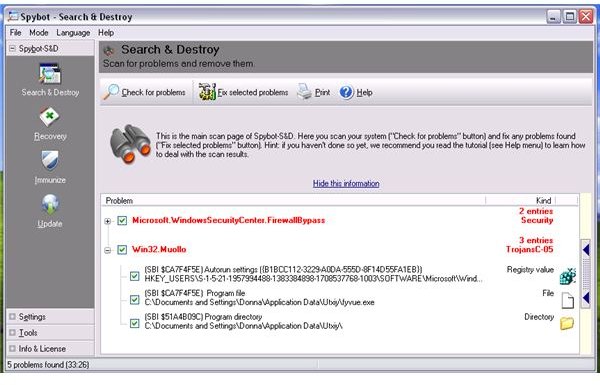
<strong>Spybot - Search and Destroy</strong> (Spybot - S&D) - This program is seldom updated but the below image shows it can detect and remove the Amazon EC2 Zeus Trojan:
-
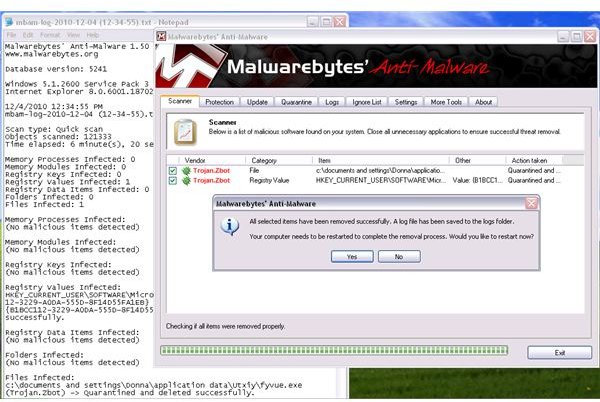
<strong>Malwarebytes Anti-Malware</strong> (MBAM) - One of the most popular anti-malware programs that is known to provide good removal of detected malware and has also detected the Zeus Trojan:
Note that I tried using Ad-Aware, EmsiSoft, SUPERAntiSpyware and Windows Defender to scan the test system with the Zeus Trojan infection, but they all failed to find or detect what Spybot Search & Destroy and MBAM was able to find.
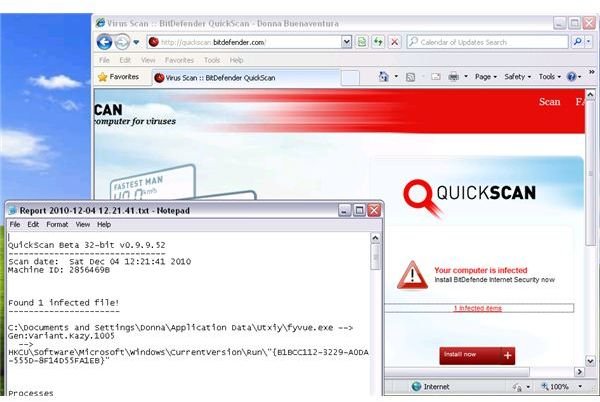
Another example of checking the computer for Trojans, in case the antivirus software misses infections is by running an online scanner e.g. BitDefender QuickScan, Housecall by Trend Micro, or Eset Online Scanner.
Final Words
Removing Trojan horses is easy, as long as the antivirus program has detection and removal abilities. There are several types of Trojan horses which means you need to ensure that protection in Windows is fully covered by an antivirus program, a firewall, on-demand scanners, and security patches. You don’t want any type of Trojans in your PC because you could lose your identity and valuable information. You’re also at risk if you’ve entered online banking and other personal information while the Trojan is logging, recording or sending the information to the attacker.
- Image credits: Screenshots taken by the author, Amazon EC2 logo (https://aws.amazon.com/ec2/)
- Sources: https://community.ca.com/blogs/securityadvisor/archive/2009/12/09/zeus-in-the-cloud.aspx, https://www.symantec.com/connect/blogs/zeus-king-underground-crimeware-toolkits
