What Tools Should You Use to Prevent Trojans Infections?
What is a Trojan horse?
A Trojan horse or Trojans are a type of malware that claims to be a legitimate application. It is created to trick
end-users to authorize installation of malicious software. Trojans do not replicate themselves like viruses.
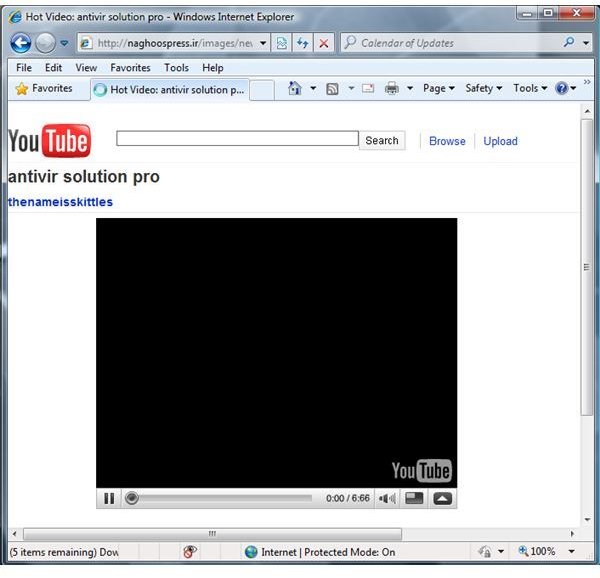
The most popular methods of Trojan distribution are thru e-mail as an attachment, compromised websites or a webpage that is embedded with the malicious code. An example is the image at the left, where a webpage prompts the end-user that a browser plug-in is required to continue view a non-existing video clip. Other distribution of Trojans are by bundling the Trojan in cracked or pirated software, and by exploiting known vulnerabilities in a browser, instant messengers, media player or other applications.
Trojan horses can steal valuable information from the computer or while using the PC. Personal information such as bank accounts, passwords, e-mail or postal address, your social security number and other valuable information are the target data that a Trojan horse wants from any computer. Rogue software or scareware is often installed by Trojans to force an unsuspecting end-user to provide their credit card number, name and address. Once the information is provided, the malware creator has succeeded in stealing the information. Note that it is important not to give any information to any service or software that you did not intentionally install on your computer or did not know the source of the software or a service.
Side-effect of a Trojan horse Infection
A Trojan horse creates a backdoor infection on a computer. A backdoor infection means a successful permission to add, delete or modify system files or settings.
One of the side-effect of a Trojan horse infection is the computer will run according to the backdoor or Trojan horse program. It can prevent a legitimate application from opening or running its task. Often, Trojans will prevent antivirus or anti-spyware programs from connecting to antivirus vendor servers, to prevent updating the virus detection signatures. It can also shutdown the targeted antivirus software to stop protecting the PC. Also, Trojan horses can prevent an antivirus program from scanning the PC.
Another side-effect of a Trojan infection is to redirect end-users to visit some webpage, redirects web-searchs (see Google search redirect virus) or redirects the homepage to unwanted websites.
Note that some Trojans include a keylogger and/or a rootkit. A rootkit infection is hidden, and some free antivirus software do not remove, but only detect. A keylogger is known to be removed by a antivirus program but if the Trojan horse was not prevented by the antivirus software, the user’s private information is at risk.
How to Remove Trojans Using Free Trojan Remover
Most of the commercial and free antivirus programs have the ability to prevent, detect and remove Trojans. Below are the free antivirus
programs with Trojan removers:
- Ad-Aware
- AntiVir Desktop
- Avast
- AVG Free Antivirus
- ClamAV
- Comodo Antivirus
- Microsoft Security Essentials
- PC Tools Antivirus Free
All of the above are antivirus programs that can be use to remove viruses, spyware, adware, worms and other types of malware. They can be use as a free Trojan remover, as well.
A quick scan on a computer should be enough to start scanning the computer for a Trojan horse infection. The removal process may require a computer restart, especially if the Trojans is actively running in the background, if the antivirus program has failed to end the running process during the removal.
Anti-malware programs are available as free on-demand scanners, and have the ability to remove Trojans; some of there are:
- BitDefender Free
- ClamWin
- EmsiSoft Anti-Malware and EmsiSoft MalAware
- Malicious Software Removal tool
- Malwarebytes Anti-Malware
- PC Tools Spyware Doctor Starter edition
- Spybot - Search & Destroy
- SUPERAntiSpyware Free and SUPERAntiSpyware portable scanner
Commercial and Standalone Trojan Remover Programs
Some security vendors provide commercial standalone tools to remove Trojan viruses. Examples of commercial anti-trojan software are:
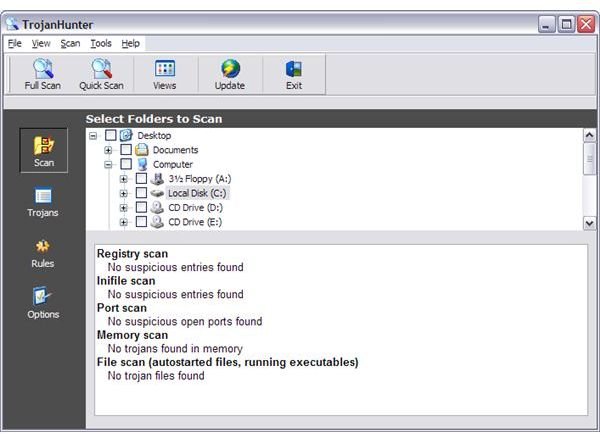
- TrojanHunter - A Trojan remover software that can detect ports used by known Trojans. Most antivirus programs, and free or commercial version include port scanning.
- Trojan Remover - Trojan remover software that is designed to accurately removes infection by a Trojan horse. It can also detect and remove Trojans that include a rootkit, a hidden file that some antivirus fails to remove.
The above Trojan remover software were developed to run along side with antivirus programs. It does not interfere with most antivirus software, but actually provides you an extra layer of protection.
Preventing a Trojan horse Infection
The most common recommendation in preventing a Trojan horse infection is to keep the computer up-to-date. Available security updates for Windows, Mac or Linux operating systems and other installed software in a computer should be installed at earliest available time. Most security updates will prevent exploits that target the vulnerable component or applications, thus preventing infection of a Trojan horse.
It is also recommended you install an antivirus program in any PC to provide real-time protection against Trojans and other types of malicious software. The antivirus software should also be used to regularly scan the computer; not just depend on the on-access protection. A regular system scan allows an end-user to verify that all files are clean and malware-free. It is is also recommended to review the available setting of your antivirus software by ensuring all files with all types of file extension, no extension or double file extensions are scanned.
An extra layer of protection is also recommended, and this is done by using extra security tools or best practices:
- Use a customized Hosts file in Windows, Linux or Mac computers.
- Configure the security settings of all applications by using the maximum available options.
- Disable or remove unneeded browsers, Windows or email plugins.
- Be informed on the latest security and privacy issues that affect installed programs.
- Do not open email attachments from an untrusted sender, and ensure the attachments are scanned by antivirus software before opening, if you are expecting an e-mail attachments.
- Do not fall into clicking or allowing an install of plugins for browser, media player or instant messengers if you are not actually aware what it is for.
- Keep your personal data private by password protecting private information or files, and use a master password.
Firewall programs should also be enabled in Linux, Mac or Windows because Trojan horses often make an outside connection. A firewall program that will monitor outgoing traffic should be used. This prevents a Trojan horse or any applications in general to use an Internet connection without your approval. If a firewall program prompts to allow an outside communication by a program that you did not install or do not know exists in your computer, the antivirus program may have missed the infection already. Immediately run a scan using an on-demand scanner to check the security status of the computer.
Image credits: TrojanHunter screenshot https://www.trojanhunter.com/trojanhunter/, screenshots taken by the author.