Understanding the Security Aspects of Network Profiles in Windows Vista
Introduction
Probably the single most serious flaw with Windows XP was its rather lax security policies. With the release of Vista, Microsoft attempted to address most of these security concerns. One of these new measures was the option to create Network Profiles.
When a user connects to a network for the first time, Windows puts together all the information related to that particular network in one place. This collection of information includes things like the network name, service set identifier (SSID), network adapter used to connect to the network, default icon, and default printer, among other data. This is what is known as a Network Profile. Creating a network profile allows the system to store the user’s preferences for that particular network, and subsequently it will be able to connect and load all the user preferences automatically.
In Windows Vista, network profiles allow the system to distinguish between the various kinds of networks to which a system can potentially connect. These being one of three kinds: private, public and domain. By classifying each network as a certain type, the operating system then treats each network connection appropriately, as Vista applies different security settings to each kind of network.
Creating a network profile
Network profiles are automatically created when a user first connects to a specific network. Usually these profiles correspond to the
wireless networks that are within range. It is also possible to create a profile for a network that is not in range at a particular time, but may be later on. This can be done by creating a new network connection, and setting the appropriate authentication and security options.
It is possible to customize the network profile through the Network and Sharing Centre in Control Panel.
Different network profiles
There are three different classifications for Vista network profiles:
-
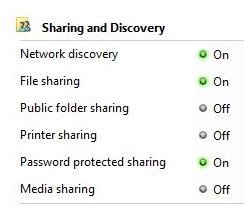
Private network profile – A private network profile indicates trusted network or networks. The default settings on this kind of network are set to the most lenient and therefore maximum sharing is enabled. Network discovery and File sharing is turned on by default, to facilitate easier file sharing and discovery. This is especially useful if the network connects multiple computers that share resources and information. Windows Firewall is also on by default and is set to allow all communication through.
-
Public network profile – Usually a public network is deemed less secure and more prone to security issues than a private network. Ordinarily public Wi-Fi hotspots like at an airport or in a coffee shop would come under this particular classification. A particular characteristic of public network profiles is that they usually have a direct connection to the Internet. Features like network discovery and file sharing are turned off by default. The purpose of these settings is to keep other computers unaware of the existence of the computer, and therefore increase the measure of security. Windows Firewall is turned on to the utmost extent, with blocks applied to all access from other computers. Blocks can be overridden by the user.
-
Domain network profile – This particular network profile is usually configured by a network administrator. Domain networks usually categorize work networks in an office environment. An individual user will probably not be allowed to configure any part of the network, as doing so may compromise the overall information security of an organizational network.
Altering the settings in any particular network profile will reflect in all the network connections with the same network profile.
Conclusion
Simply by classifying certain networks as private or public can mean a great deal in terms of computer security. Public networks are usually fraught with danger, with malicious persons looking to take advantage of the slightest lapse in security. With the discovery turned off, it makes locating the system, and therefore attacking, a remote possibility instead of a probability.