How to encrypt emails with PGP Desktop Email
What is PGP Desktop Email Encryption?
This article explains how to secure emails with PGP Desktop Email, a feature found also in PGP Desktop Home, PGP Desktop Professional and PGP Desktop Corporate PGP Desktop 9.9 editions and bundles.
I will throw a light on PGP Desktop Email‘s encryption and signing as well as the inverse operation of email decryption and verification, which in all is called PGP Messaging (because some instant messaging programs can be encrypted, too) and applies to email text messages as well as their attachments. PGP Desktop Email uses so called public key encryption, also known as asymmetric encryption, for message confidentiality and sender authentication. Public key encryption essentially means that the key to encrypt a message is public (non-secret) and different from the private (secret) key used to decrypt an electronic mail much like an open padlock which everybody can close but only the owner with his key can open.
Let’s assume Alice and Bob want to secure their email exchange by PGP cryptography to prevent Charlie from prying on confidential emails, or to add a level of trust to email recipients who can verify the sender’s identity.
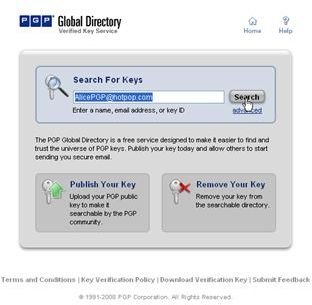
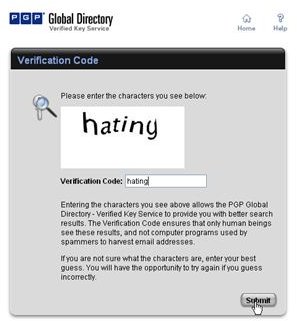
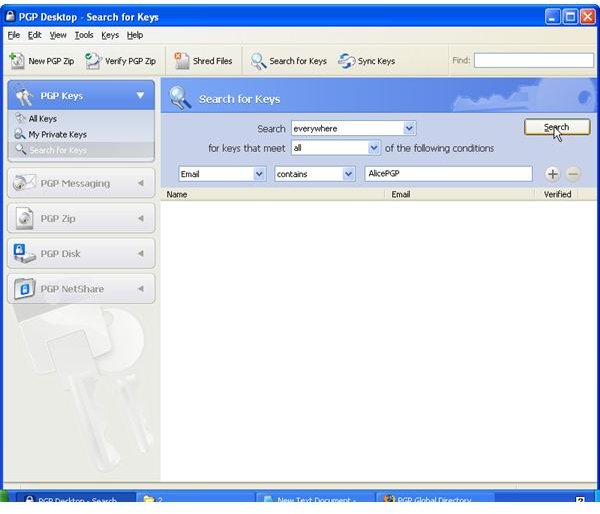
Key Generation and Validation, PGP Global Directory
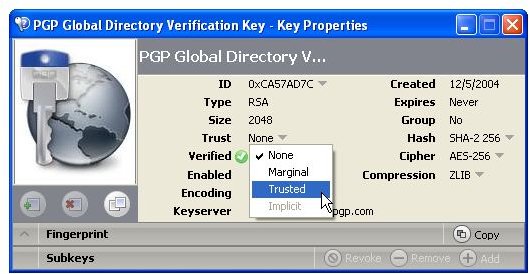
During the installation of PGP Desktop on her client (Mac OS X or Windows XP and Vista) computer Alice is asked to create a private/public keypair if she doesn’t already have one. The key generation requires the user name and email address for identification and validation as well as a secret passphrase which is a ‘password’ in the form of a memorable sentence used to protect the private key of the keypair. In the course of the installation PGP Desktop, by default, publishes new public keys on the PGP Global Directory, an open repository for keys. Later, the owner of the keypair, Alice, is supposed to click the validation link in an email from PGP Corporation so that anyone can search and download her validated public key to send Alice confidential messages which only she as the holder of the private key can read. It is also necessary for Alice to download and import the PGP directory verification key which she has to sign and assign full trust.
The pictures below illustrate the process for Alice:
Images - Click to Enlarge
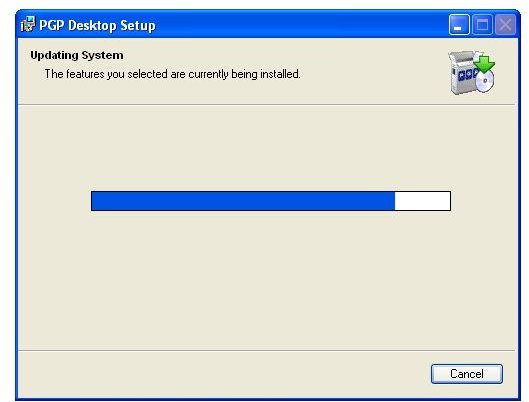
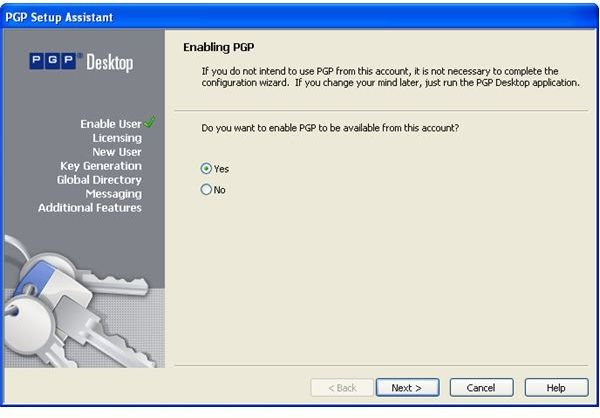
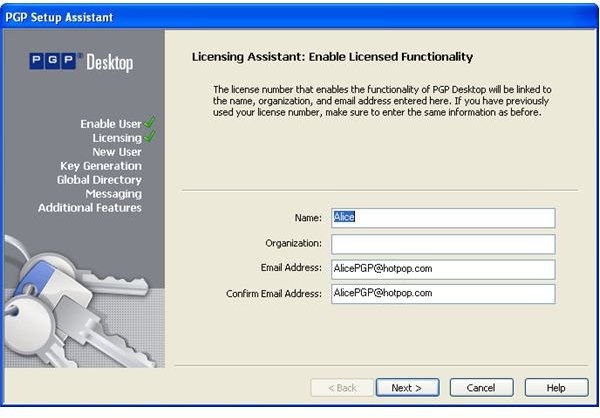
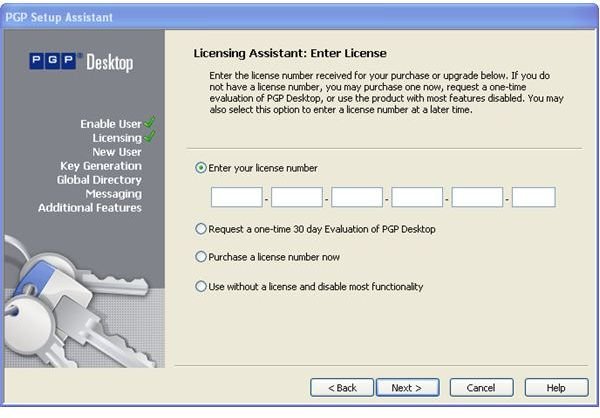
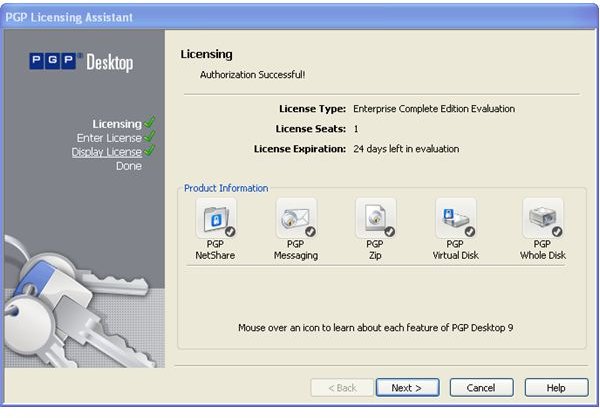
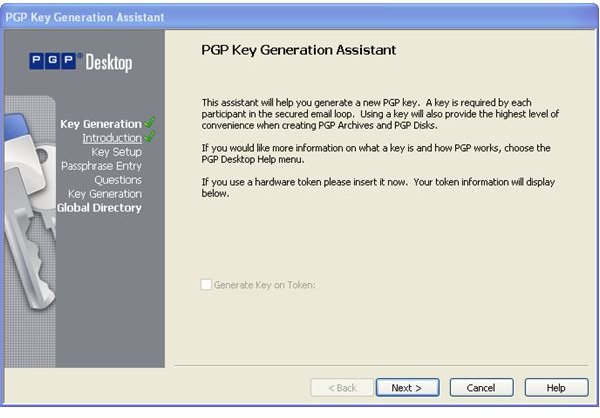
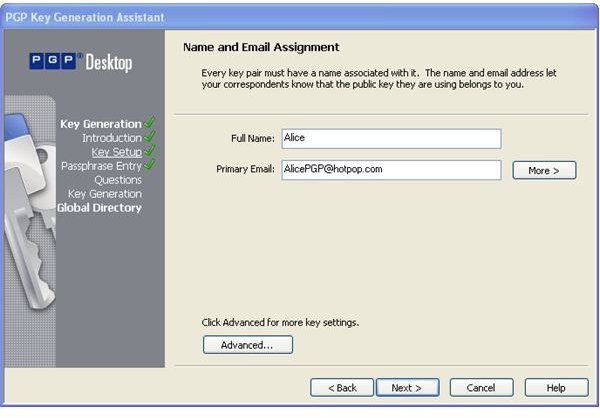
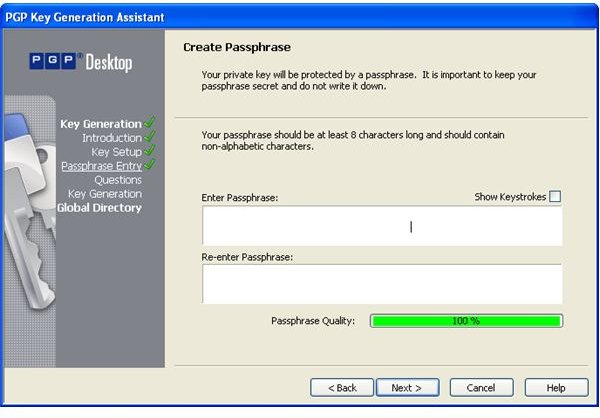
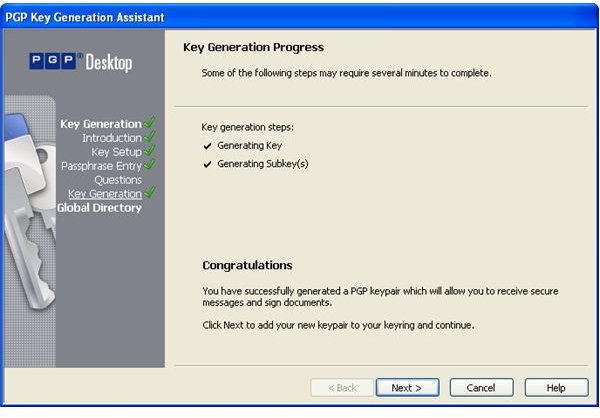
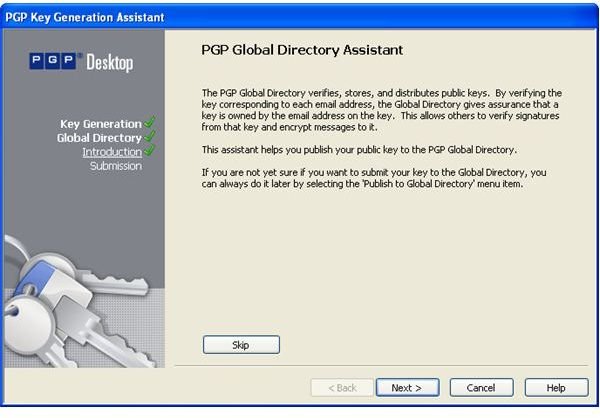
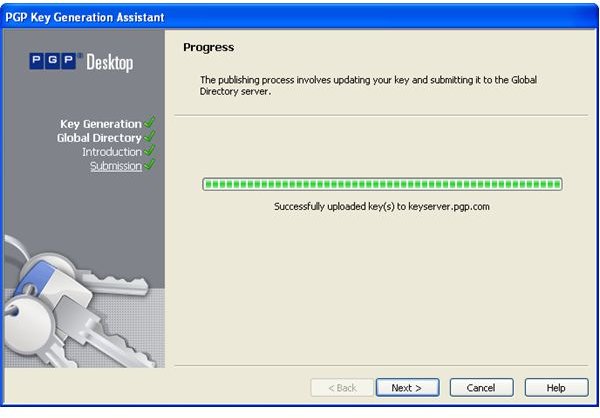
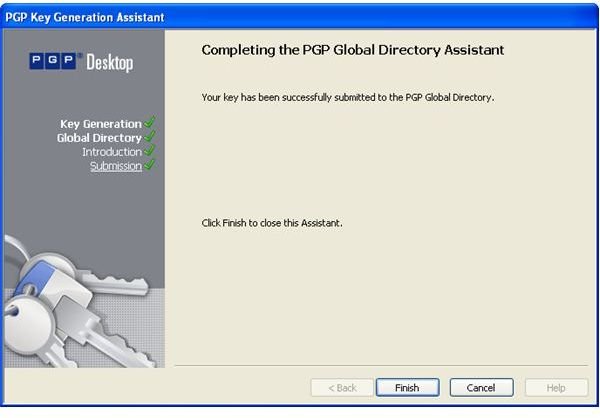
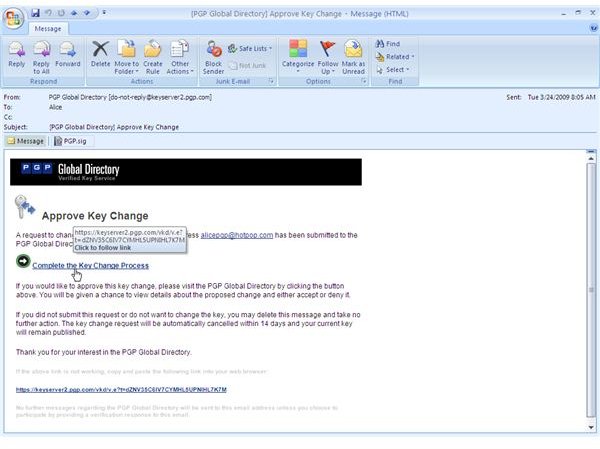
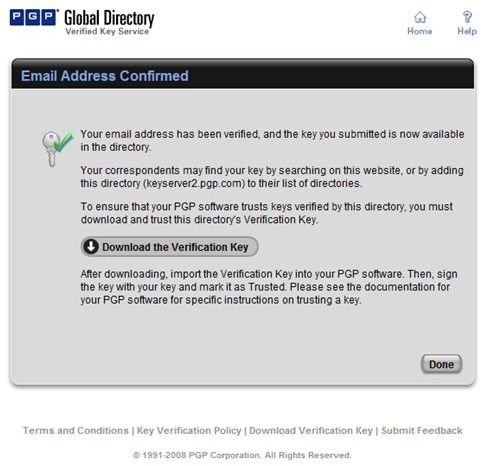
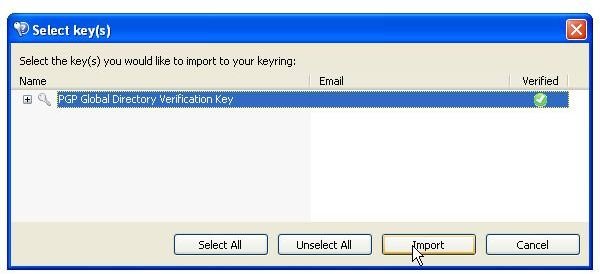
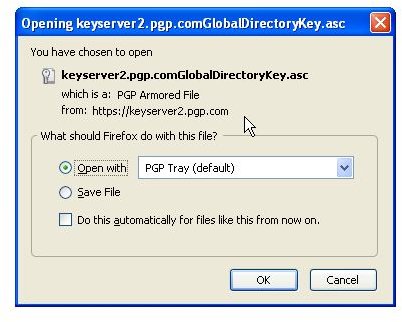
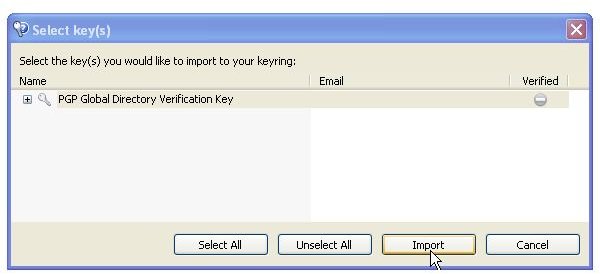
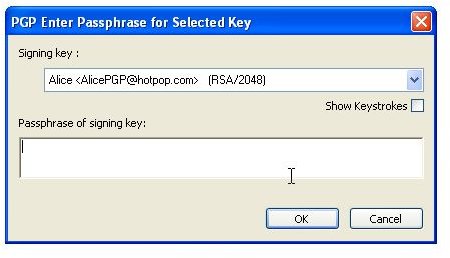
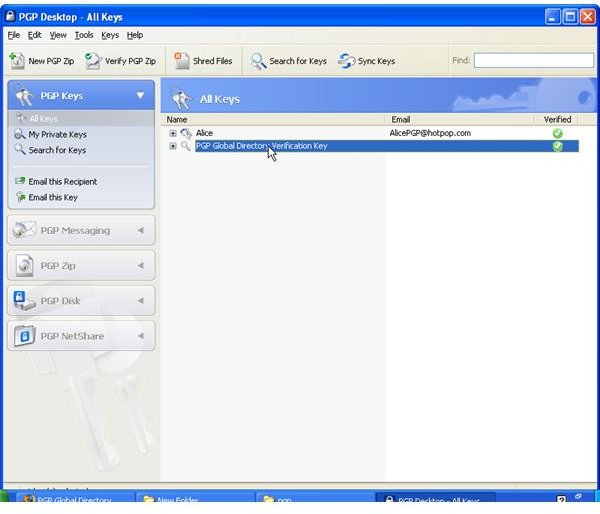
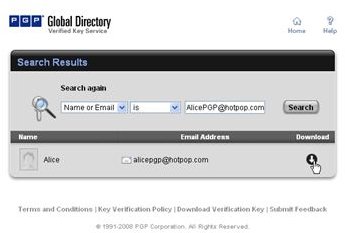
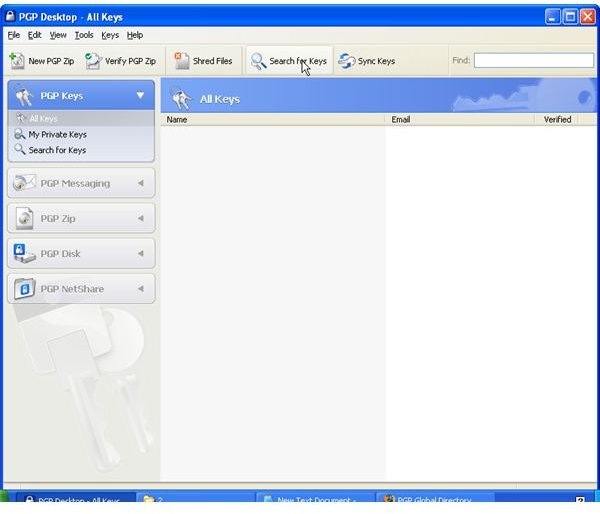
Key Verification, Key Search
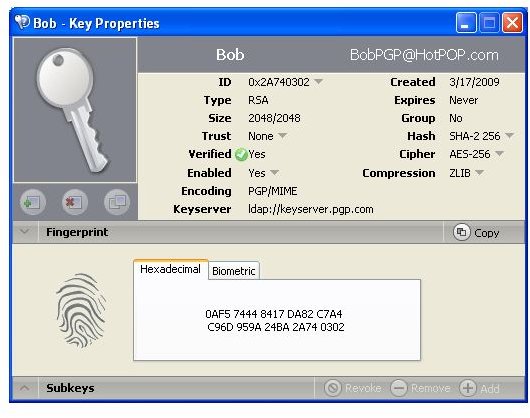
Alternatively, public keys can be sent trough, for instance, unencrypted mail for manual import into PGP Desktop and verification by the receiver over the phone by means of comparing the fingerprint of the received key with the sender’s key fingerprint, a hash value in hexadecimal format or word list format. For the key to be trusted the values must be identical.
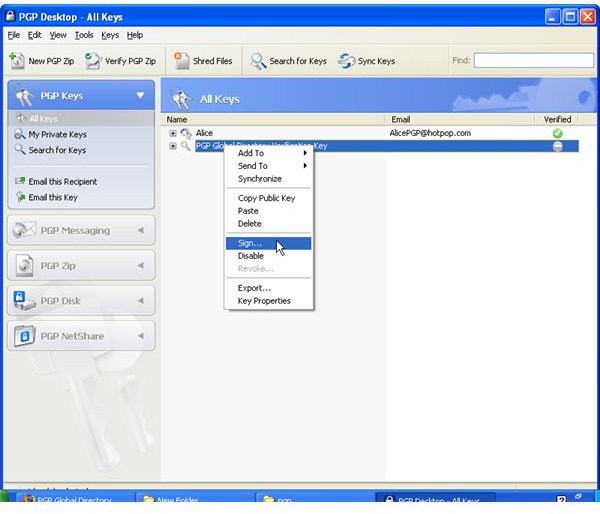
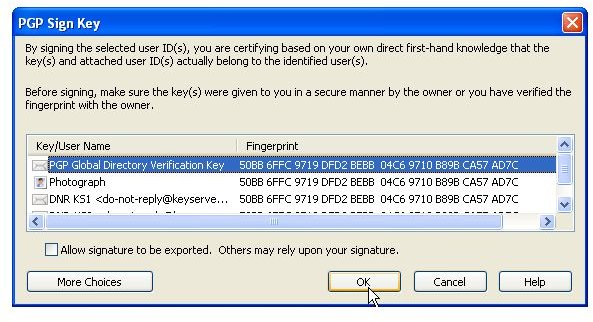
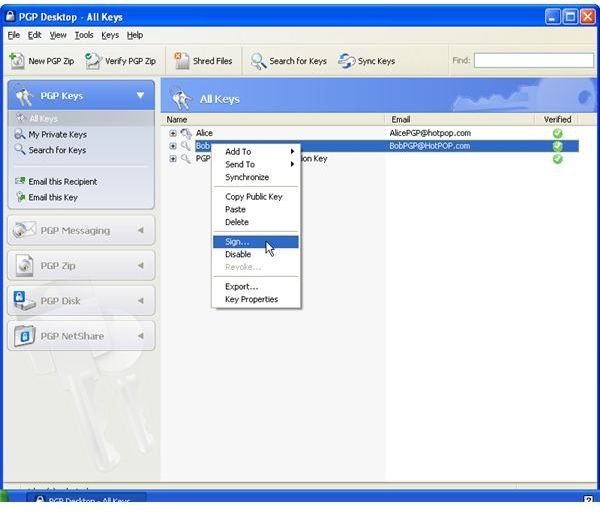
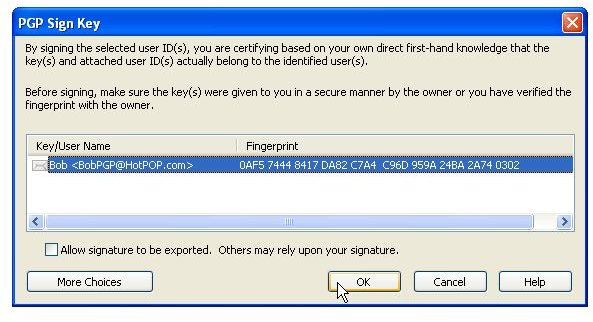
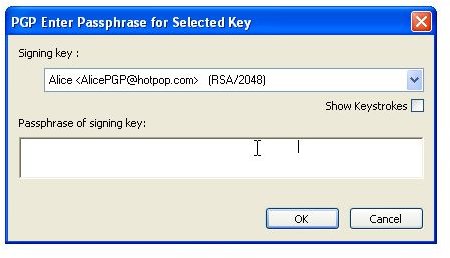
The pictures below show how Bob sends his public key to Alice by unencrypted mail [1,2], and how Alice imports it [3,4]. Then the images depict how Alice checks Bobs fingerprint for verification [5,6] and how she signs [7-9] Bob’s public key so that it becomes validated for her. Additionally, you can see how Bob searches and downloads Alice’s validated public key from the PGP Global Directory [https://keyserver.pgp.com] [10-12] and where he could have done the same through the PGP Desktop Interface [13,14].
Images - Click to Enlarge
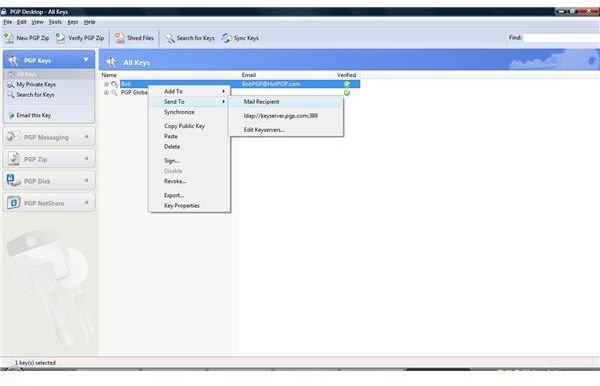
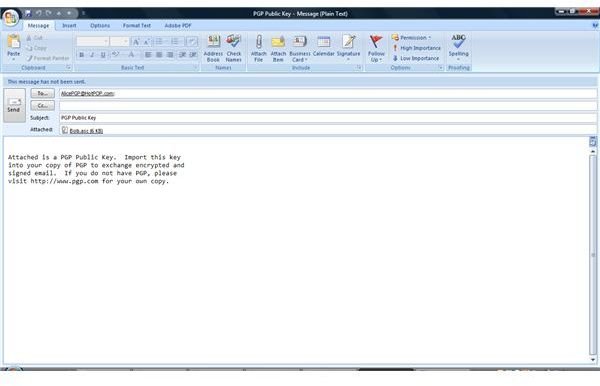
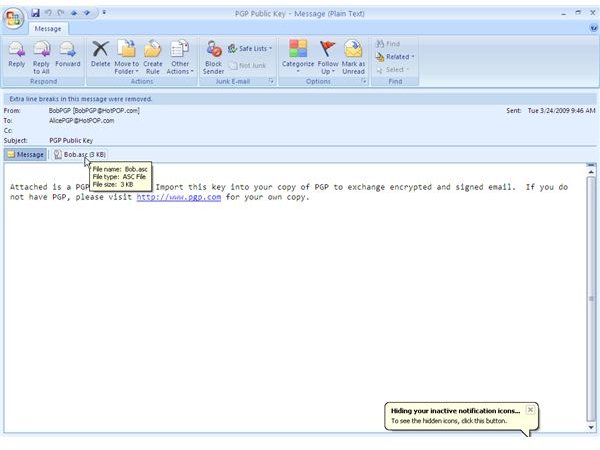
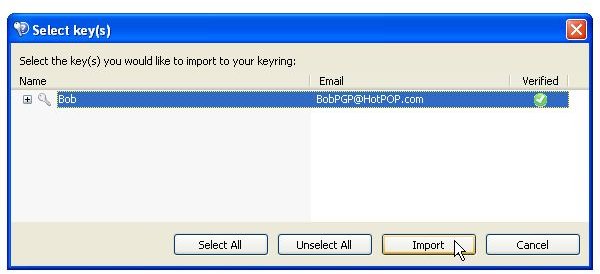
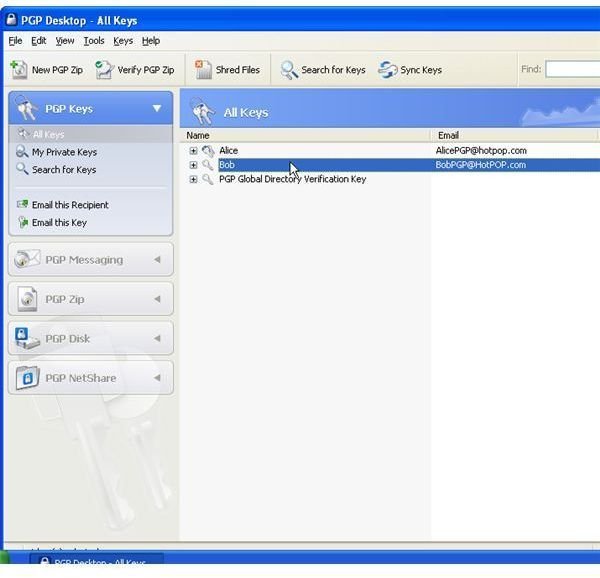
How PGP Desktop Email Secures Email
Provided that PGP Messaging is turned on all traffic between the email client such as Outlook2007 or Windows Mail and the mail server is monitored and PGP Desktop Email will automatically step in should Alice or Bob send or receive an encrypted or signed message. Each email account is considered a service to which PGP Desktop Email applies a number of policies, sequenced sets of instructions, which are automatically processed depending on whether they receive or intend to send emails. In other words, PGP Desktop Email automatically decrypts, verifies, signs and encrypts their email communication, and it does so transparently by PGP notifier (a small text box) popping up.
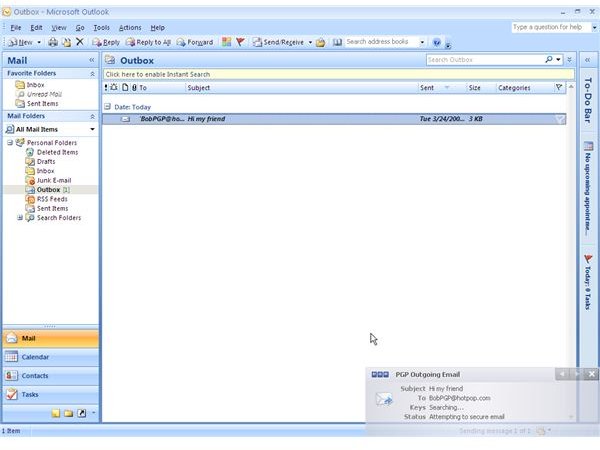
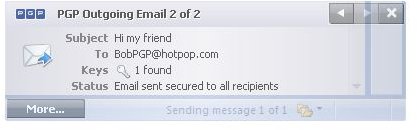
Outgoing Messages - How to Encrypt Emails with PGP Desktop Email
To send secure or encrypted email with PGP Desktop Email the message can be written as usual in the email client software. PGP Desktop Email recognizes the email address on outgoing messages and searches locally stored keys and then PGP Global Directory for the recipient’s public key and applies the default policies outlined below:
-
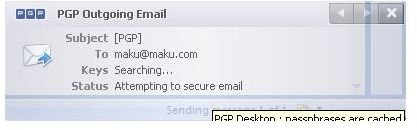
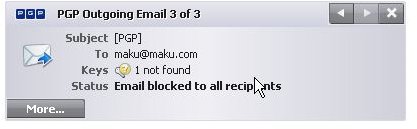
If the email contains [PGP] in the subject line or if the sender marked the email as confidential in the email client software then PGP Desktop Email automatically encrypts the message if the key is found; otherwise PGP Desktop Email prevents the email client from sending the email in absence of trusted public key as encryption is demanded by the sender (required encryption).
-
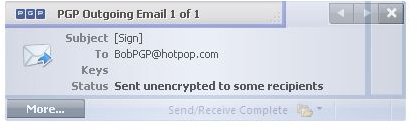
If the policy outlined above does not apply (the email is neither marked confidential nor contains [PGP] in the subject line) then PGP Desktop Email automatically encrypts the email if the recipient’s key is found and permits the email client software to send it, whereas in absence of a trusted public key PGP Desktop Email permits the email client to send the message in the clear (opportunistic encryption).
Please note that PGP Desktop Email defaults as follows:
-
Mail list submissions are only signed and mailing list admin requests are neither encrypted nor signed.
-
Keys are automatically signed upon keypair generation
-
Encrypted mails sent out are automatically signed
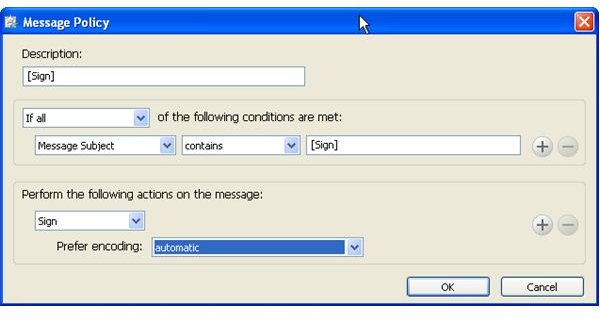
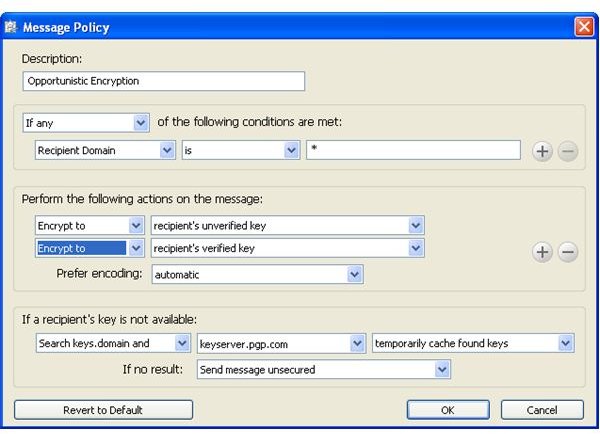
In order for PGP Desktop Email to sign emails without encrypting them one can create a police, for instance, [Sign] similar to [PGP] in the subject line, and set PGP Desktop Email proxy to apply the new policy.
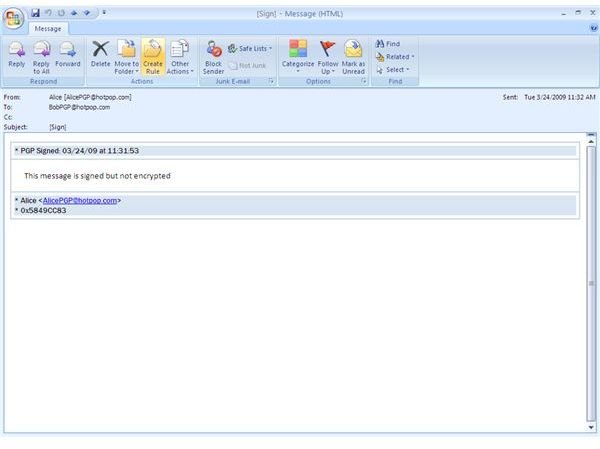
Below you find depictions of the following items: Alice sending an email to Bob which is automatically secured as Bob’s key was found [1,2]; an email with required encryption by means of [PGP] in the subject line for which no key was found and thus was not sent [3,4]; how to configure the [Sign] policy [5], and finally an email from Bob to Alice making use of the [Sign] policy [6]
Incoming Messages - How to Decrypt Emails with PGP Desktop Email
If the incoming email is
-
encrypted but not signed then PGP Desktop Email checks the local keying for the private key, and, if found, uses the cached passphrase to decrypt the mail on the fly or asks to enter the secret passphrase first. If the private key is not present or PGP Desktop Email has been disabled or turned off then the email will be passed encrypted to the email client.
-
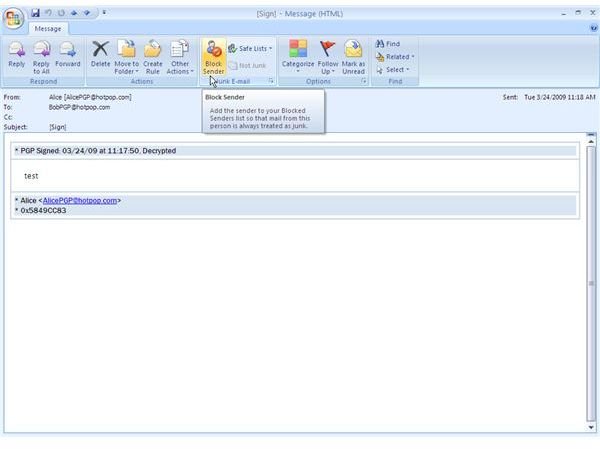
signed but not encrypted then PGP Desktop Email first searches the local keyring for the public key of the sender and then PGP Global Directory in order to verify the signature of the sender.
-
encrypted and signed then PGP Desktop Email tries to decrypt the email as explained above, and only if successful continues with verifying the sender’s signature
-
neither encrypted nor signed then PGP Desktop Email just passes the email to the client software without taking any action
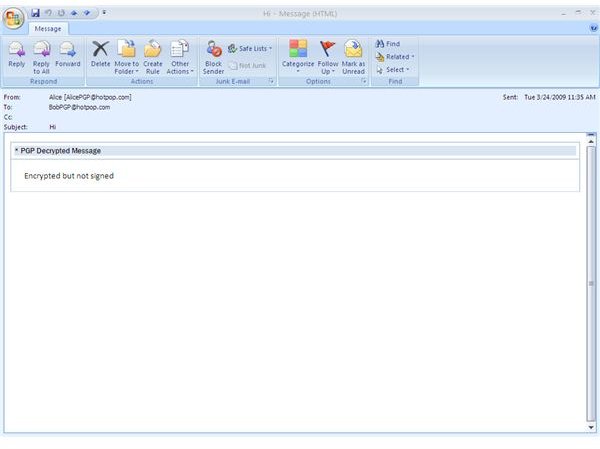
Depicted below you find the example emails sent in the last section now as incoming mail [1,2]. In addition to that can you see another mail sent by Alice which was only encrypted, but not signed [3] due to different policy settings shown, too [4].
Images - Click to Enlarge
Images - Click to Enlarge
Granting Trust to a Key
In addition to certify that a public key belongs to somebody one can entrust the holder of the public key with introducing other people in the future by setting the key’s trust level to either marginal or trusted; default is none. By opting for complete trustworthiness - analog to Alice assign the PGP directory verification key full trust - any new key arriving from that person will automatically be considered valid despite the recipient not having it signed by himself or herself, whereas marginal trust only assigns a degree of trustworthiness to the holder of the public key and “none” speaks for itself.
The Bottom Line
To sum up, PGP Desktop Email provides state-of-the-art secure messaging including automated encryption, decryption, signing and validation of emails based on services and policies. PGP Desktop Email also ships as part of PGP Desktop 9.9 editions and bundles, reviewed in my next article, including share, disk and virtual volume encryption, PGP Zip, Self-Decrypting Archives and PGP Shredder. Why not protecting your sensitive emails like Alice and Bob? Follow these links to download a free trial version of PGP Desktop Email or PGP Desktop 9.9.
References
Writer’s own experience
Screenhots by the writer