Methods of Authentication
Authentication
With the many forms of authentication, administrators and information technology professionals must select what will be the best for them. While maintaining security, administrators must meet the security needs of their organization and the convenience of end users. Productivity can be hindered by too much security and ‘loose’ security can put assets at risk.
Username and Password
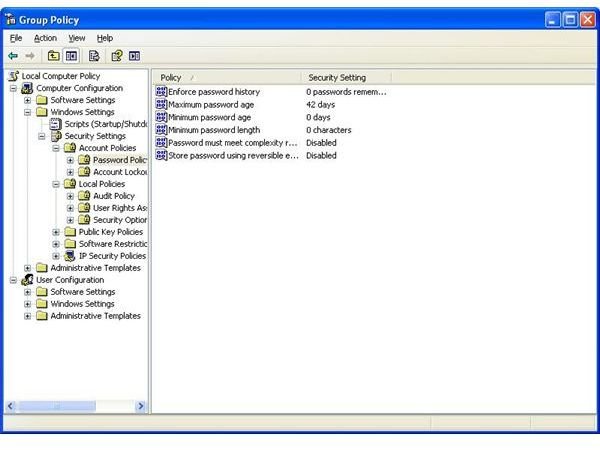
The method of authentication everyone is familiar with is the username and password. While the username often reflect the individual’s name, authentication is based on a database (logical) that contains this information and an encrypted password. End users and administrators should use common sense when selected a password for an operating system or application. Passwords need to be complex and policies need to be set in the group policy editor.
Passwords should contain alphanumeric characters and symbols. Spaces are highly accepted in order to create passphrases. As you know, passwords should not be written down or shared. Even if the scenario you are in becomes inconvienent and you ‘want’ to give your password.
Password Policy
Biometrics
Today, most laptops come with fingerprint biometrics readers. This form of authentication provides the physiological make up of the human body and / or passwords. While biometrics is still in its infancy, improvements are being made to allow for facial recognition, iris and retinal recognition. Other forms are available and many companies are investing money in their research and development departments looking for viable options for this authentication method.
Multifactor Authentication
Multifactor authentication is the act of using more than one authentication method when logging on to a server or a workstation. This form of authentication helps to provide additional security to applications or computers. Generally authentication is made by authentication factors such as biometrics and a password. Some applications use passwords and RSA devices to generate a random set of alphanumeric characters that must be entered.
Kerberos
Kerberos is an open source form of security that is used as a form and method of authentication. This security works by exchanging a shared secret key (or token) that is a trusted third party. When workstations want to communicate with a protected server, a Kerberos server issues a token or ticket. The software and logical portion of a server that ‘looks after’ or governs the distribution of keys is called the Key Distribution Center (KDC). Once a workstation communicates a Kerberos server issues the aforesaid ‘tickets’ through what is known as a Ticket Granting Server. Once this process takes place, the two computers wanting to communicate can do so. Kerberos policies can be found in Active Directory Servers and in the group policy editor.
Group Policy Editor
CHAP
Many information technology professionals hear the term CHAP and don’t realize that this form of authentication is primarily used in dial up connections. With CHAP, this authentication uses a three-way handshake to prevent attacks known as a replay attack.
Conclusion
While there are additional authentication methods and methodologies available, this article focused on basic authentication methods used in computer security. The basic use of these methods helps to provide users with security to protect their transactions and assets. While most computers in small business implement username and password security, many business fail by not providing basic password policies.