Great Free Computer Network Security Tools
Top Tools for Network Security
The importance of online security can never be repeated enough, with threats coming from viruses and phishing attempts in emails, aggressively coded website scripts, “floating threats” looking for open PCs to compromise and various malware and spyware that can ruin both your PC and your privacy.
However if you’re running a corporate network, what you will be looking for are network security tools that detect intrusions and unusual behaviours, as well as utilities that can detect problems.
While you’re unlikely to find any antivirus, firewall or anti-malware tools that are available for free to corporations, there are various free computer network security utilities that can be used to keep your network as clean as a whistle.
Note that unless stated otherwise, these tools are all open source and require a Linux system for installation and operation. They will work seamlessly with a Windows network, however.
Intrusion Detection
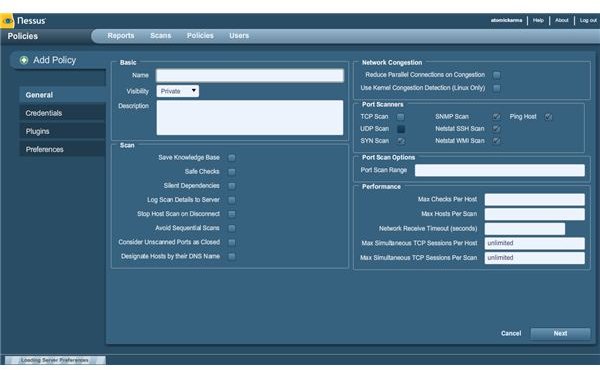
Keeping intruders out is a key aspect of any network admin’s role, and a tool such as Nessus from Tenable can be used to great effect in achieving this. Nessus can be used to scan ports and features a browser-based user interface to setup scans and reports. See our review for more information or visit www.nessus.org/download.
The software is free to download and use, although corporate users will benefit more from the paid version than the free choice, which has limited ability to safeguard a large network.
Nessus is available for Windows, Linux Debian, Ubuntu, Red Hat, Fedora and SUSE, Free BSD and Oracle Solaris as well as Mac OS X.
Screenshot by author
Network Management
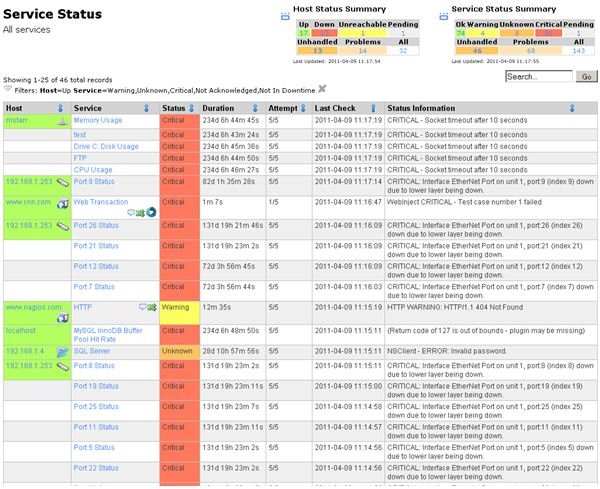
Nagios is arguably the best open source tool available for managing and monitoring networks. It requires a Linux or UNIX system to run but is capable of monitoring any network device, be it a Windows desktop, Windows server, Novell server, and etc.
A typical implementation uses Nagios as a reporting tool for monitoring the reliability of your network across different sites. Any errors that could be cause for concern will be logged for an in-depth review.
Find out more at www.nagios.org.
Image credit: https://www.nagios.com/products/nagiosxi/screenshots
Firewall Interrogation
It is likely that at some point, someone will be try to gain access to your corporate network, either for kicks or cash. As a result you will need to know how your firewall holds up to the probing that will no doubt take place.
While running a traceroute or ICMP tool to scan a network might be foiled by a good firewall, other tools used by those with malicious intent might reveal more than you want them to know about your network. A tool like hping can help you to detect just what information your firewall is divulging.
Find out more about hping at www.hping.org.
Monitoring Traffic
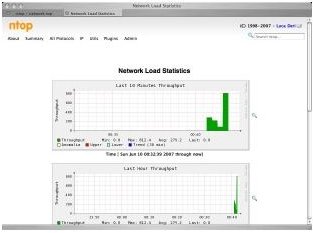
Designed to display a full account of traffic that is currently running on your network, ntop (www.ntop.org) is available for Linux and UNIX as well as Windows, and can be a vital tool in your free computer network security tools arsenal.
The advantages of monitoring traffic across your network are manifold; one particularly popular use is to track inappropriate usage by users who might be abusing their privileges by accessing unsuitable or irrelevant websites.
Image credit: https://www.ntop.org/overview.html
Wireless Detection
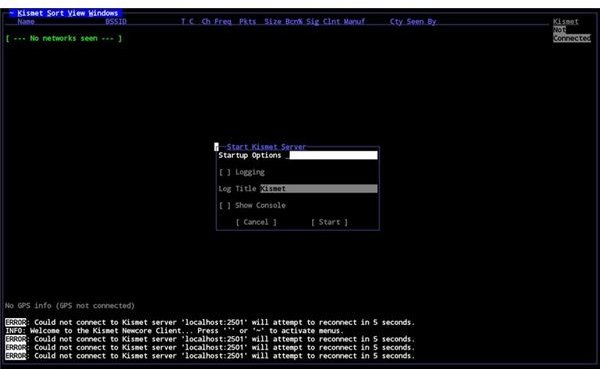
Wireless networks are becoming an increasingly-popular target of hackers, which is why you should spend some time detecting the strength of your wireless network access to detect any vulnerability that might exist.
Probably the best option for detecting and sniffing wireless networks and packets is Kismet (www.kismetwireless.net) although the Windows NetStumbler tool (www.stumbler.net) is also popular.
Image credit: https://www.kismetwireless.net/screenshot.shtml
References
Author’s own experience.