Monitoring System and Network Security
Why Network and System Security Monitoring?
No organization should assume a piece of hardware or software is operating as expected. You should have processes in place to monitor critical systems, including servers, databases, switches, routers, etc. Monitoring helps ensure you meet your company’s criteria for ensuring the confidentiality, integrity, and availability of data and critical systems.
Effective security monitoring should answer the following questions:
- Are my security controls operating as I expect? Did I improperly configure one or more of them? Did a change in the network infrastructure change their effectiveness?
- Is there unwanted network or system behavior that slipped through my layered defense?
- Are there signs that network or system behavior or resource utilization portend a business continuity event?
- How do the security controls affect business use of the network?
Finally, you don’t need an application for all monitoring tasks. In fact, some monitoring defies automation. Consequently, your approach should include both manual and automated processes. But no matter how you decide to approach this, always follow one very important rule: inspect what you expect.
What Should I Monitor?
Monitoring every device and every application in your enterprise is usually not a cost effective plan. Instead, you should focus on critical infrastructure–including hardware and software–and sensitive data. What you look for depends on what you are trying to protect, but the following list is a good place to start.
- Repeated failed logins. Monitored using logs or tools designed specifically to look for login anomalies.
- Logins at unusual times.
- Large data transfers.
- Unusual connections to external devices or sites. If an attacker comes over the Internet to steal your data or take over your systems, he or she must establish a session at some point. If you can’t shut down all external connections not explicitly allowed via LAN/WAN device configuration, then you need to know when unusual connections come up.
- A significant amount of traffic to known data collection (e.g. spyware) sites.
- Collection of these or other conditions characteristic of an attack against your network or your data.
Monitoring for each of these individually is a Herculean task. However, a good log management process, supported by the right technology, makes this a much easier task.
Monitoring Alternatives
The best way to monitor your entire network, including critical systems and network gear, is with a comprehensive log management solution. Log management provides a way to observe your entire network and allows you to look at individual events within the context of overall network status. Let’s look at how this works.
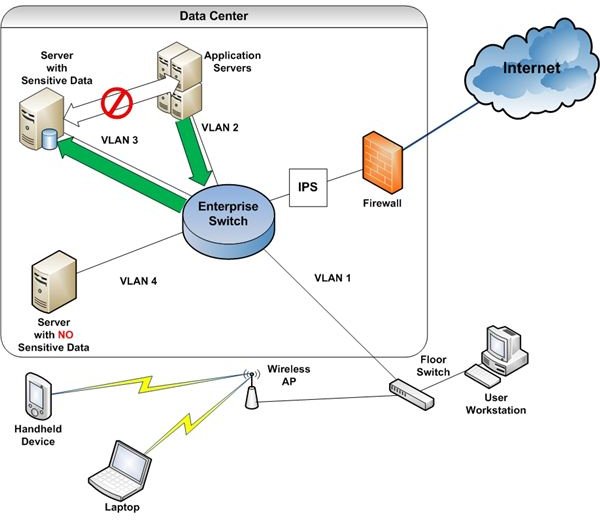
Figure 1 shows a network with a typical defense-in-depth configuration. A firewall controls traffic flowing from the Internet, an intrusion prevention system (IPS) monitors allowed traffic–both in and out–and VLANs control the flow of traffic within the network via access control lists. Finally, the wireless access point controls access with encryption and a strong key.
One way to check whether the controls are operating properly and that nothing unusual is happening on your network is to review logs on each system of interest. In this example, systems of interest include the firewall, the IPS, the switches, and any computer which stores or processes sensitive data. This is time consuming, frustrating, and results in looking at each log in isolation; events occurring on one device are not correlated with events occurring on other devices.
Another approach is implementation of a set of monitoring tools which alert you when specific events occur. This reduces your time commitment and is far less frustrating. However, it still doesn’t result in understanding how all events monitored, including seemingly harmless ones, might show unwanted activity that doesn’t appear by reviewing individual events.
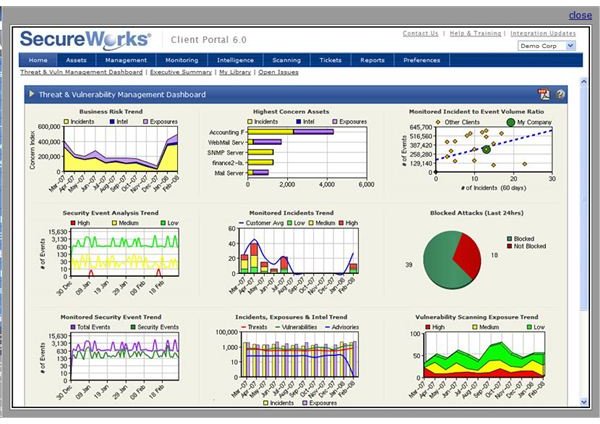
My preferred approach is to collect all the logs in a central log server, correlate events, and present the results via a portal dashboard, as shown in Figure 2 (SecureWorks). This reduces time by providing a single screen a security analyst can watch throughout the day, drilling deeper as necessary. It provides an overall picture of network activity by combining logs from all monitored devices. These systems can alert staff when critical issues arise. They also serve as a single point for managing all identified vulnerabilities and incidents.
However you choose to monitor your network, make sure you do it. Don’t assume your network is secure because you implemented all the appliances and software recommended by “best practice”. And although it is outside the scope of this article, make sure you have a documented and practiced incident response plan.