Tips for Securing Your Laptop: Wireless Security
Hotspots
Hotspots, or public Wi-Fi, can be found anywhere. There are plenty of free and commercial hotspots to choose from and many people use these hotspots to get more out of their wireless devices. People who take advantage of public, open and free hotspots should be very careful though, because the privacy and security of the user and their computer is often at risk.
What Are the Risks of Using Free Wi-Fi?
Below are the threats and risks of using free, public and open hotspot connections:
- Fake or Rogue Wi-Fi – Attackers will open their connection for anyone to use. They will name their connection as “free Wi-Fi”, “Public Hotspot”, or any other name that can trick users seeking a free connection with a strong signal.
- Eavesdropping or Man–in-the-Middle attack – Attacker that is able to inject, listen or intercept communications between two computers. This type of attack often affects those using an unencrypted Wi-Fi access point or a free or private Wi-Fi connection.
- Malware – If the user unsuspectingly connects to an attacker’s rogue or fake Wi-Fi connection, the attacker is in control of the users’ connection and laptop. It can transfer malicious software (malware) or codes.
When a laptop is connected to fake or rogue hotspot connection, the attacker is in total control of the connected computer. They can log keystrokes, redirect users to unwanted websites, record usernames and passwords in any webpage or application that the connected user uses, infect the computer, listen to conversations when chatting or video conferencing and many more malicious activities that a hacker or intruder can or wants to do.
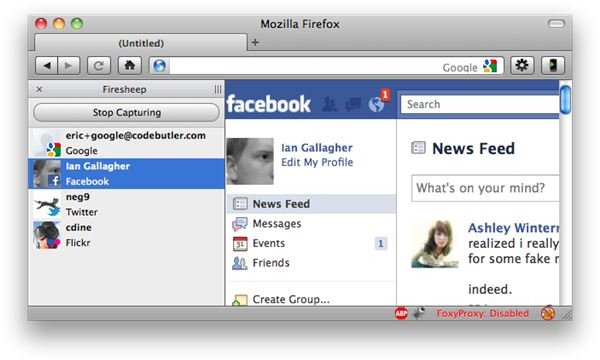
One possible attack involves a hacker using software like FireSheep. FireSheep is a Firefox browser add-on that attackers can use to access accounts belonging to connected users’ on public, free and unsecure Wi-Fi connections. The author of FireSheep has demonstrated how social networking services such as Facebook, Twitter, Google, Amazon, Windows Live, Flickr and similar online services can be targeted by attackers. FireSheep runs on Mac and Windows, which means no one is actually exempted or safe, if the user is not careful where connecting their laptop or Wi-Fi enabled devices such as an iPad, iPhone, Nokia, BlackBerry or other mobile phone.
Laptop Wireless Security
The best laptop security for using Wi-Fi or hotspots is to simply not login to any webpage or online service, when you have to use a public, open, free and unsecure Wi-Fi network. This will help prevent attackers or sniffers from getting what they want – your private and valuable information. To help secure your laptop, mobile phones and yourself, follow the precautions below to prevent or decrease threats:
- Turn-off the Wi-Fi capabilities on a laptop or any device, if not in use.
- Avoid using public connection when using online banking or any services that require personal data to access.
- Configure the Network and Sharing Center in Windows to not automatically connect to any public hotspots. Manually choose which networks you want.
- Keep your computer or device current with updates.
- Use a firewall and antivirus program with real-time protection.
- Use Wi-Fi Protected Access (WPA and WPA2) or Wi-Fi Protected Setup (WPS), and then use a strong passphrase. Also see, WEP, WPA, and WPS - Which to Use?
If you have to use public Wi-Fi to do online banking, use social networking websites, or access any online accounts and services, make sure that you are going to login using SSL or an encrypted connection. That means the webpage or online service is using HTTPS protocol.
If you plan to send and receive email using an email program, use free and secure email certificates so attackers cannot view the e-mails. Also see, How to Enable SSL for a Secure Email Service.
Finally, consider encrypting files or your hard-disk to prevent anyone from viewing the data on your computer. You can just use a program like TrueCrypt or enable BitLocker and BitLocker To Go in Windows.
Image credits: https://codebutler.com/firesheep, https://commons.wikimedia.org/wiki/File:Stiftungsparkassa_hotspot.JPG By Emes (Own work) [GFDL (www.gnu.org/copyleft/fdl.html) or CC-BY-SA-3.0-2.5-2.0-1.0 (www.creativecommons.org/licenses/by-sa/3.0)], via Wikimedia Commons
