Database Security Concepts
In the first article in this series, we saw what database security is and introduced the core concepts of database security. In this part, we’ll continue our look, in somewhat greater detail, at the core concepts that play a vital role in database security.
Image source: bp.blogspot
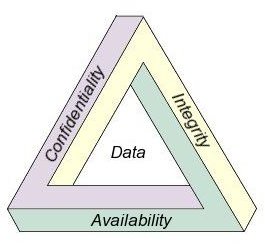
CIA Triad
Confidentiality
In database security concepts, Confidentiality comes first. Confidentiality can be enforced by encrypting the data stored in the database. Encryption is a technique or process by which data is encoded in such a way only authorized users be able to read the data. In other words, encryption means rendering sensitive data unreadable to unauthorized users. Encryption can be done at two different levels: data-in-transit and data-at-rest.
Data-in-transit: This refers to data that is moving within the network. Sensitive data, for example, that is sent through network layers or through the Internet. A hacker can gain access to this sensitive data by eavesdropping. When this happens, the confidentiality of the data is compromised. Encrypting data-in-transit avoids such compromises.
Data-at-rest: It is possible for a hacker to hack the data that is stored in the database. Encrypting data-at-rest prevents such data leakages.
Different encryption algorithms are available, which includes Data Encryption Standards (DES), Triple DES or 3DES, and Advanced Encryption Standards (AES).
Integrity
Integrity can be enforced by setting User Access Controls (UAC) that define which users have to be given what permissions in the database. For example, data related to employee information is stored in a database. An employee may have permission for viewing the records and altering only part of information like his contact details, whereas a person in the human resources department will have more privileges.
What are the steps that have to be taken to ensure integrity of the database?
- Once the database is installed, the password has to be changed. Similarly, periodic checks have to be conducted to ensure the password is not compromised.
- User accounts that are not in use have to be locked. If one is sure that these user accounts will never be used again, then the best step is to remove such user accounts.
- Policies to set strong passwords have to be enforced. A good idea is to have a policy of changing the passwords once per a month.
- There are two types of authentication when it comes to database security, namely, domain authentication and database authentication. Choose which authentication you are going to follow and ensure you stick to it. Having both types of authentication will create greater confusion rather protecting the database.
- Check for the roles each user has and set the rules accordingly. You must ensure that users are given permissions to do what they are allowed to do. I know this is a time consuming job when the database is huge, but once the permissions are set the right way, it is easy to check unauthorized entry or access.
- Does your company have multiple database administrators? If yes, segregate the duties among these database administrators.
Availability
Databases must not have unplanned downtime. To ensure this, following steps have to be taken:
- Restrict the amount of storage space given to each user in the database.
- Limit the number of concurrent sessions made available to each database user.
- Backup the data at periodic intervals to ensure data recovery in case of application issues.
- Databases should be secured against security vulnerabilities.
- To ensure high availability, usage of database clusters is recommended.
Thus it is understood that the database security concept lies with three major concepts: Confidentiality, Integrity, and Availability.
This post is part of the series: Understanding Database Security
An ever increasing number of databases are needed in business, and, with the advent of the Internet, threats or risks to these databases are increasing apace. In this series, we provide a definition of database security, and look at security concepts and the types of threats involved.