What is a Network Intrusion Detection System (NIDS)?
Identifying ID, IDS, IPS, and IDPS?
Intrusion Detection (ID) entails the process of monitoring and analyzing network system events for signs of incidents (e.g., violations or imminent threats).
IDSs use both hardware and software to detect intrusion by triggering alarms when something appears out of the ordinary (e.g., intruders or internal attacks) either on a network or a host. Simply put, IDSs are designed to detect attacks (not prevent them from occurring).
To prevent attacks or even block suspicious traffic, instead, an Intrusion Prevention System (IPS) is used; an IDPS (Intrusion Prevention and Detection System) is deployed for information gathering, logging, detection, and prevention.
Types of Intrusion-Detection systems
- NIDS Network-based IDS
- It is used to monitor a network & backbone networks
- HIDS Host-based IDS
- It is used to defend & monitor Operating Systems on hosts
- DIDS Distributed-based IDS
- It is used to report to a central management station
- PIDS Protocol-based IDS
- It is used to monitor and analyze the communication protocol between connected devices
- APIDS Application protocol-based IDS
- It is used to monitor and analyze the communication on application specific protocols
All about NIDS
What is NIDS?
It is software and hardware that resides in one or more systems connected to a network.
The purpose of a NIDS?
It examines the network traffic by scanning and utilizing network adapters (running in promiscuous mode) to monitor and analyze the data packets that travel over the network. It can do this in real-time!
In addition to being capable of detecting attacks from the sensors, NIDS also identify attacks by using one of two techniques:
1. Anomaly Detection (Profile-based intrusion detection): it depends on _s_tatistical analysis and works by comparing the observed behavior of the network with models of “normal” behaviors
2. Misuse Detection (signature-based or pattern matching detection): generates alarms when the detect intrusions by matching observed activity with known signatures of intrusions or vulnerabilities.
How to Setup a NIDS?
NIDS are easy to deploy and setup. Normally, it is a dedicated workstation that is connected to the network; but, it can also be a device that has the software embedded in it and is then connected to the network.
A NIDS is either connected to a hub, a network switch to be configured for port mirroring, or is placed as a network tap. It works as a “packet-sniffer.”
Example of NIDS are Snort (freeware) and Sax2. Other network-based IDSs include: Shadow, Dragon, NFR, RealSecure, and NetProwler.
Benefits of a NIDS
NIDS play an important role in the world of network security. They help prevent the consequences caused by undetected intrusions on the network.
Placement of a NIDS can detect
1. Unauthorized users (insiders & outsiders)
2. Abuse or overload from bandwidth and Denial of Service (DoS) attacks
Informative Images
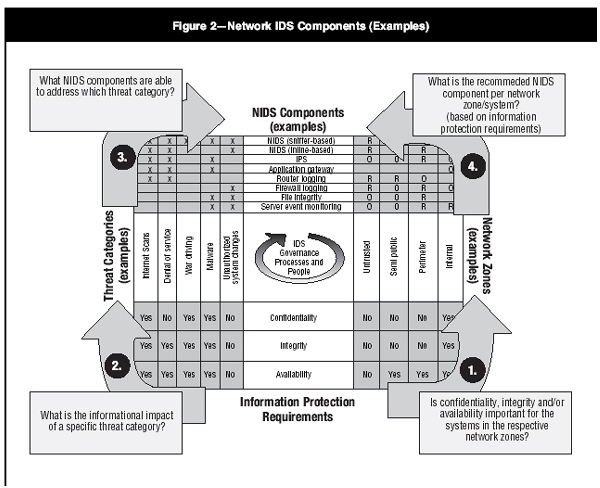
Figure 1: NIDS Components
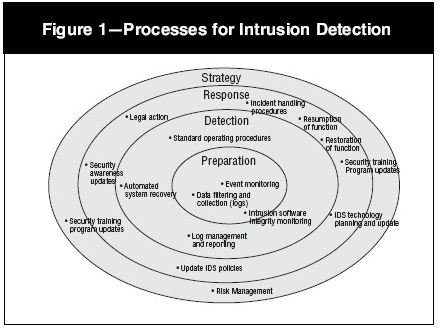
Figure 2: Processes for ID
Source: Information Systems Control Journal, Vol 1, 2006, published by ISACA