Find Out About Network Security and Layers of Defense - The Best Way to an Effective Secure Environment for Your Home or Business
Putting It All Together
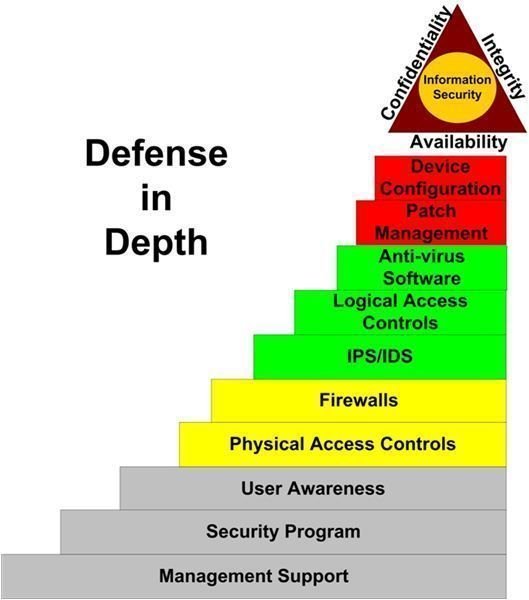
Each of the layers in the JES Model supports the layers below it. Let’s take a quick walk up the model (See Figure 1) to get a better idea of the relationships.
Strong management support is necessary to create a business culture in which information security is integrated into each daily task. Guidance on how to apply security is contained in the security program. It’s through the use of the security program that technical and non-technical employees are given the tools - in the form of policies, standards, guidelines, and procedures - necessary to protect information throughout the enterprise. Employees are trained on and continuously reminded of their roles and responsibilities in the protection of information assets through a strong user awareness program. These first three layers form the administrative foundation of a secure environment.
Physical access controls prevent intruders from performing unauthorized tasks–as defined by policies, standards, and guidelines in the security program–that require actual physical contact with a system. These tasks may include the theft or destruction of one or more components of a system, laptop, PDA, etc. Firewalls are placed at entry points in the network perimeter as well as into subnets containing sensitive data. They allow only the traffic defined in the policies and standards of the security program to pass. Together, physical access controls and firewalls work to prevent unauthorized access to critical areas of the network. But if an intruder cracks a network firewall, he still has no direct access to information resources.
Logical access controls begin their work once the firewalls and physical controls allow general access. In order to directly access information resources on servers and workstations, an intruder must authenticate to the target system. Authentication may include entering a user ID and password, using a biometric device, a token, or a combination these. IPS/IDS devices or software help detect and prevent the activities of threat agents that have gained unauthorized access to the network or to a specific resource. They can also help prevent the installation of malware onto servers and end-user devices. Finally, IPS/IDS solutions can detect and react to attempts to circumvent logical access controls by, for example, dictionary or brute force attacks. Anti-virus (AV) software supports the IPS/IDS layer by detecting trojans, viruses, worms, and non-viral intrusions such as spyware that may have circumvented its controls. AV and IPS/IDS software protect against attempts by intruders to gain access to information or resources that either assist in cracking logical access controls or in bypassing them altogether. All the layers up to this point are designed to prevent threat agents from reaching an information resource or detecting and removing a threat agent from the network.
Patch management and device configuration form the last line of defense against threats. It’s the hardening of systems, through the timely application of patches and the careful configuration of system components that removes the most fundamental security vulnerabilities. Most of the layers below these two serve to protect systems from delayed patch release or implementation as well as weak or nonexistent system security standards and guidelines for secure system configuration.
JES Summary
The JES model is just one way of looking at defense in depth. It allows us to visualize the various methods required to fully protect critical or sensitive information assets.
The controls included in the model begin with administrative support and preparation, followed by general access controls. The upper layers help to defend assets from intruders who make it past the controls implemented in the first five layers. Finally, the last two layers form the fundamental last line of defense through due diligence in patching and configuring system components.