Network Security and Defensive Countermeasures
Types of Network Attacks and Prevention Technologies
Network attacks are (and have been) a common problem for computer users. For this reason, we must combat network security incidents, threats, and events when under attack. Here, users will first learn about some of the more familiar network attacks and know of ways to counteract them. Users will also be told of the importance of setting up important security controls and defensive countermeasures to prevent network attacks.
Here are some Network Security Incidents and Attack Intrusions that have occurred to date:
-
Distributed denial-of-service (or DDoS) attacks, which gets its victim to open an email attachment with embedded malicious code in attempt to plant a Trojan hourse that can launch the DDoS attack. Such an attack can saturate the network and reject incoming data until it can clear its overload, flood a connection (Syn Flood attack), or cause buffer overflows (where the attacker feeds a program far more data then it can handle causing data to spill over).
-
Man-in-the-middle (MITM) attacks, which has a third party (outsider or hijacker) intruding in a session between two entities. Such an attack (session hijacking) allows the attacker to intercept and read someone elses messages or carry on in the session in the name of the other entity. This is also an example of spoofing: obtaining the network authentication credentials of an entity to carry out an attack under the entity’s identity.
-
Password attacks, which has an attacker guessing the password for a system or of a user; thus allowing an attack on the network. An example of this is a brute force attack, where the attacker tries to decipher a password.
Note: Both networks and data are vulnerable to attacks. And, as a result, the attack could corrupt or destroy data or the network itself.
There are a lot more network attacks not mentioned here that have done harm in a computing network environment, but the purpose of this article is to inform you of network security and defensive countermeasures, so with this in mind, I turn your attention to an important message from Microsoft: “Without security measures and controls in place, your data might be subjected to an attack.” [1]
Here are some important security controls and defensive countermeasures to prevent network attacks:
-
Install and Configure a Firewall (and/or VPN). It is important to determine the type of firewall (packet filtering gateway, stateful inpection firewall, bastion host, as well as others) to use and where to place it on a network (in or outside the perimeter of the network environment). When configured and deployed properly, firewalls (placed between network segments) can screen and filter traffic as well as block a wide range of attacks and protect an environment connected to a network. An alternative would be to implement a VPN. A virtual private network (VPN) could provide an encrypted tunnel inside the perimeter to pass network communication traffic.
-
Deploy a Network-based Intrusion Detection (NID) or Network Intrusion Prevention Systems (NIPS) device. Attached to a network, it can monitor activity and examine traffic patterns throughout the network. It can effectively defend and prevent against network attack intrusions and malicious or suspicious events. The benefit of using a NID or NIPS is that it operates in real time which helps protect the network. It will also raise an alarm that can alert the network administrator if suspicious activity occurs.
-
Use network security tools (free or commercial). To search for network security tools, computer users may be interested in Sectools.org, which shares their “Top100 Network Security Tools” with the public. Their Web site provides a valuable list of tools that will help ensure the security of all computer users.
Network Security and Defense
Here’s How to Secure a Network from Being Attacked …
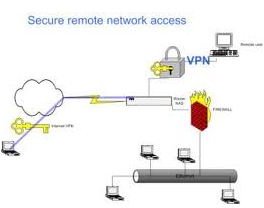
To secure a network and prevent attack intrusions, it will require either one or more of these security controls and defensive countermeasures. To design such a secure environment, refer to the diagram below.
Image credit: WindowSecurity
* The diagram shows that a firewall is part of the network and a VPN is for remote access.
Ideal software solutions for the network include: Sygate Personal Firewall Pro 5.5 or Kaspersky Internet Security, which includes a firewall with an Intrusion Detection System (IDS).
Prevention Methods for Network Users and Enterprises
To prevent network attacks, users should consider performing the following.
Risk Analysis. A continuous risk assessment can help minimize network security risks by examining the risks that a user or an organization face. This is a well-known planning tool that forms the basis for risk management and prevention.
Security Policy. A security-related policy with Incident handling and escalation procedures is important for handling network security incidents and attacks. Having a policy available for network users provides the necessary resources, steps, and actions to effectively respond to such security events.
Security Awareness Training. If network users are aware of security incidents, threats, and attack intrusions, they will likely know what to do and how to act before, during, and after a network attack. This may be the most effective defense countermeasure for network security. As affirmed by SANS, “Security Awareness is a critical part of an organization’s information security program; it is the human knowledge and behaviors that the organization uses to protect itself against information security risks.” [2] Awareness training can raise the level of general interest and concern among enterprises and network users.
Resource and Reference Section
[1] Common Types of Network Attacks: https://technet.microsoft.com/en-us/library/cc959354.aspx
[2] SANS Security Awareness Training: https://www.sans.org/security_awareness.php
-
How to Prevent Denial of Service Attacks: https://learn-networking.com/network-security/how-to-prevent-denial-of-service-attacks
-
Incident Handling Guidelines: https://security.tamu.edu/Security_for_Faculty___Staff/What_You_Should_Know/Incident_Handling_Guidelines.php
-
Risk Analysis Techiques: https://www.drj.com/new2dr/w3_030.htm