Managing Linux Firewalls - The Easy Way
Introduction
Iptables is, put simply, a set of rules which define which ports can be accessed by which computers. It is quite an advanced piece of software that can look at the source, destination, and integrity of a packet and compare it to the rules. The rules can then state whether the packets are allowed to continue through or must be dropped.
In this article I will mainly be looking at security issues and questions that come up often and how to manage the advance command-line software through a GUI, if you would like to look into which commands you can use on the terminal see this: Linux iptables - An Introduction.
Iptables
Iptables itself is based off an older package known as ipchains which is no longer actively developed. The main difference between the two is that iptables can now monitor a connection and forward it to a separate port if needed. This is mainly because iptables is a “stateful” firewall and can monitor incoming and outgoing connections as well as packets. Iptables can therefore make better decisions on where a packet is going.
If you do not know what you are doing, iptables can be very difficult to set up but in most cases you do not need to touch it because it is already configured. It is only if you have a private server or service running that iptables really comes into play. You could also use iptables for a redirection if someone has attempted to connect to an older system. This is known as packet forwarding.
Finally, iptables can be used to completely blacklist IP addresses, so if one IP is permanently trying to gain a password to a server you could have a script to block it using iptables after a certain number of attempts. It is also useful because it can block ports from certain IP addresses and allow others, for example if you have a dedicated service such as SSH running which you only want to access from the local network, you can block internet traffic and allow local traffic.
Graphical User Interface
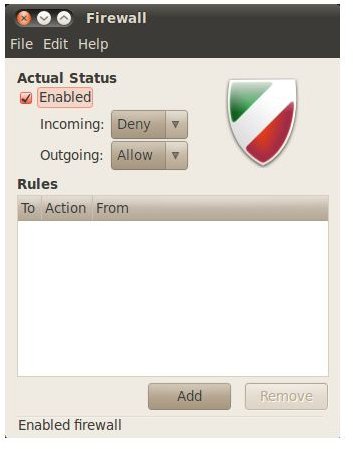
Even the best of script writers have problems configuring iptables correctly, and that is why I think it is important to have this section so that you know there is a simple uncomplicated way for your basic firewall needs. However if you need something more advanced, you should make your own rules. In order to install the “Uncomplicated Firewall,” put the following into your terminal window:
sudo apt-get install gufw
You can then add rules for services and programs and tinker with it to your heart’s content without being too worried about screwing up long commands and having to research what an iptables command means before you insert it into your terminal (because no-one uses commands without knowing what they are, right?).
Conclusion
As you can see, iptables is one of the reasons Linux is so safe from hackers, viruses and malicious software. For the harder, more complicated things such as forwarding and for very intricate systems, I would certainly advise that you create your own iptables rules in the terminal using the guide linked above.
For the simple Joe Blog who has a private web server or private service to test things on, the GUI way will save a massive headache in the long run and will allow him to quickly and easily solve any problems in the firewall setup.