iptables Harden Your Linux Installation, Using Command Line Or Firestarter
Introduction
Windows has a standard firewall that according to some isn’t very restricted. Some even say it’s no good at all. In Linux you will not hear this at all. What you will hear instead is how bad a distribution is at setting up iptables restrictions correctly.
If you are an Ubuntu user, then you are already using iptables. You never noticed it but in Ubuntu iptables is setup to let everything go out but let only a few connections in.
For a Linux beginner it can be quite a task to figure out how to work with iptables. Here at Bright Hub we understand this. That is why we have written this introduction to iptables.
After reading this article you will be able to add rules to iptables, open ports you want to have people connect to (think a webserver or a VPN server), and be able to administer your iptables.
Now because I know not everybody is a command line guru, I will also point you towards a great GUI option.
How does iptables work?
You can see iptables as a rule set. In iptables we talk about chains of rules. These chains of rules together build up your firewall. The chains are named:
- PREROUTING - Rules in this chain will be applied before the packet gets routed.
- INPUT - This packet will be locally delivered.
- FORWARD - This chain applies after a packet is routed wen not delivered locally.
- OUTPUT - Every connection going from this machine to other computers in the network or the Internet.
- POSTROUTING - These rules apply after the packet is routed.
This is what a rule might look like:
iptables -A FORWARD -d 192.168.0.120 -p tcp –dport 80 -j ACCEPT
In this case this rule belongs to the FORWARD chain. This rule forwards port 80 on this machine to IP address 192.168.0.120. We can use this rule to create a rule that will drop the connection to port 80.
iptables -A INPUT -p tcp –dport 80 -j DROP
This rule belongs to the chain INPUT. It will DROP all connections to port 80. If you want to see if this worked just run:
sudo iptables -L
This will show you a list per chain of current rules in use. Keep in mind that restriction is your best protection. Only open incoming ports if you have to. These rules are not preserved at boot. If you would reboot your computer now, all of the rules would be gone.
How to Preserve Rules On Boot
The following will work on Ubuntu and possibly other Debian derivations. To accomplish this we need to save the rules sets first. Run:
sudo iptables-save > /etc/iptables.rules
To apply these rules every time Ubuntu boots we need to add some code to /etc/network/interfaces. This is a configuration file, so open it with your favorite text editor.
sudo nano /etc/network/interfaces
Add the following line to the interface you use for outward connections:
pre-up iptables-restore < /etc/iptables.rules
This will apply the rules in iptables.rules every time before the interface becomes active.
But What if you are not a Console Guru?
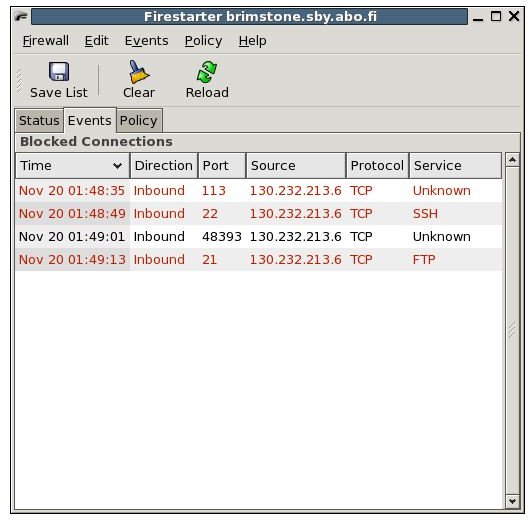
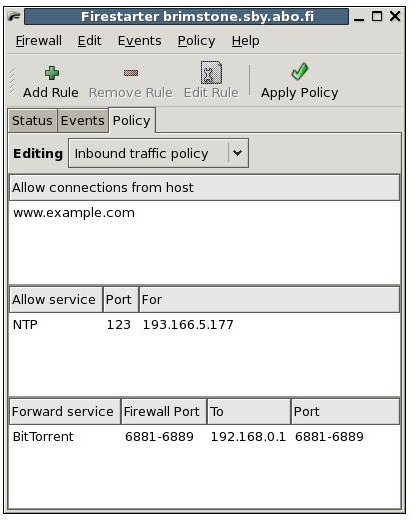
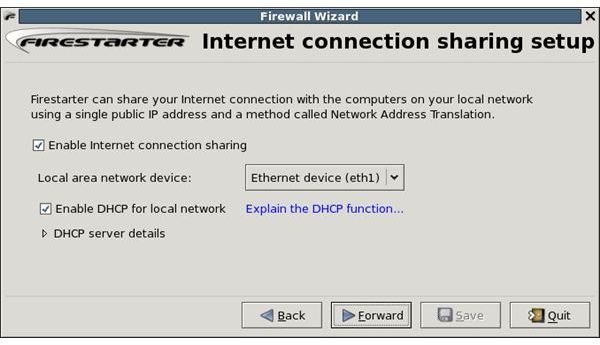
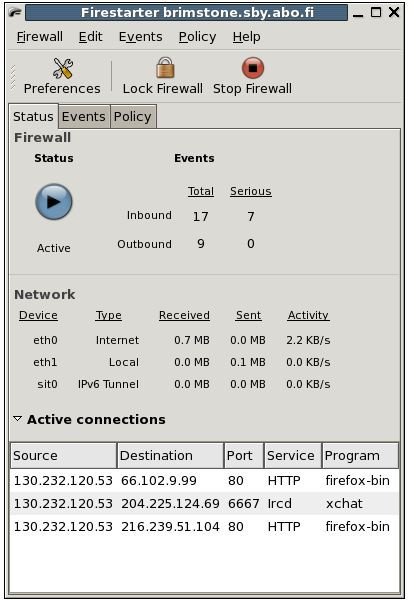
There are several GUI options you could use. But I like to recommend an option that I have found easiest to use: Firestarter is a GTK (Gnome) GUI, but it also works great on Qt (KDE). Firestarter takes care of all of the iptables stuff described above; it saves the rules and applies them at boot of the operating system. It is easy to set new rules for outgoing and incoming connections. The default screen of Firestarter shows the status of the firewall, a blue icon means the firewall is active and a red one means the firewall is inactive. “Active connections” shows current connections to your computer. There are three tabs to Firestarter: Status, Events, and Policy. The Status tab you are now on. The Events tab shows all events currently going on. The Policy tab is where you create your rules. The tab has three sections, allowing you to allow connections from hosts, Allow services, and Forward services. Remember to hit the Apply Policy button to make sure the policy is in use. See screenshots below.
Images of Firestarter