How Does Network Security Work?
Network security, as defined in the first article in this series, is a critical component of business operations. However, implementing it can be overwhelming for someone not familiar with the terminology and concepts. This is true even if an organization decides to work with a security vendor instead of designing and implementing controls in-house. You want to know what you are purchasing, why you care, and how each control fits into the overall network protection strategy. The rest of this article helps reach those goals.
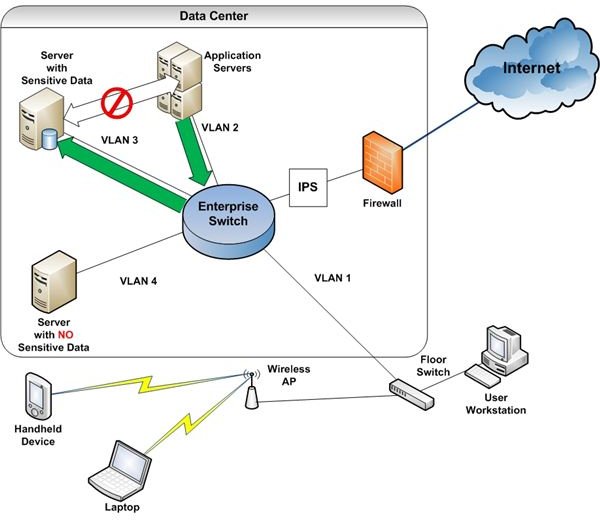
Before diving in to the technical discussion, I recommend printing Figure 1. I use this diagram to discuss network security terms and concepts.
Types of Controls
Like end-user device security, network security consists of three primary types of controls: administrative, physical, and technical. Administrative controls consist of security policies and supporting procedures used to control user behavior, including how your IT staff implements new technology.
Physical security controls include locks, fences and other devices used to delay the progress of someone attempting to gain physical access to network components.
Technical controls, the subject of this article, are devices, configurations, etc. used to protect data stored on or moving through your network.
Technical Controls - Basic Concepts
The first concept to understand is defense in depth or layered security. Figure 2 depicts a network-level layered security model.
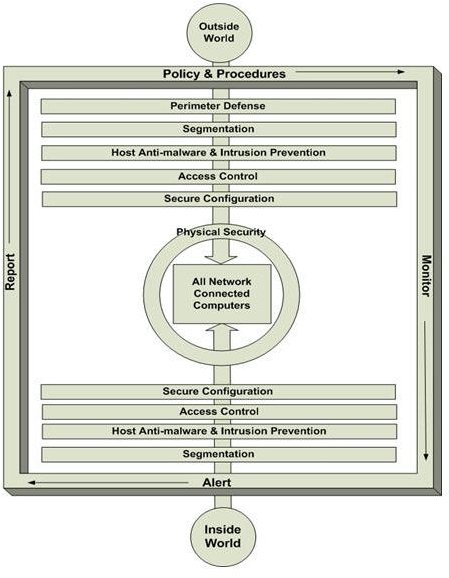
There are two paths to sensitive data: from the outside and from the inside. When we think of network security, we usually think about non-employee attackers stealing our data or disrupting computer services. However, most problems are caused by employee behavior- intentional or unintentional. So technical controls have two purposes.
First, we need to keep unauthorized personnel from getting to sensitive information. Second, we have to help good employees do the right thing while thwarting malicious activities of other employees.
We accomplish both objectives with layers of controls which support each other. In other words, if a control fails to work as expected, other controls should step up and fill the gap. This is why control implementation must consider both prevention and detection.
At a high level, controls protecting data and critical systems from both internal and external access must:
- control access to the company network;
- place the most sensitive information on servers with “special” security;
- control malware and intrusive activities;
- control access to devices;
- harden devices with secure configurations; and
- control physical access to critical infrastructure.
Perimeter Defense
Often, managers typically think setting up a secure perimeter around the network is “network security.” While it is an important component, it should only be the first layer of defense between an external entity and sensitive data.
I define perimeter security as any control or set of controls which:
- controls which computers gain access to the network;
- controls which users gain remote or local access to the network; and
- monitors for anomalous network behavior.
Referring to Figure 1, the firewall and IPS (Intrusion Prevention System) fulfill these requirements. The firewall contains rules which determine the types of network traffic allowed to pass from the Internet to the company network. These rules are usually based on IP address ranges, ports and protocols.
The IPS filters permitted traffic looking for signs of malicious intent, including:
- malformed network data;
- files matching the characteristics of known malware;
- repeated attempts to reach protected devices; and
- evidence of port scanning, a tell-tale sign that someone is trying to map the network prior to an attack.
An IPS device can block questionable traffic, alert security, or both.
Another perimeter security device in our example is the Wireless AP (Access Point). Laptops, handheld devices and some desktops attach to the company network via wireless technology. While wireless is a great technology for connecting mobile devices, it can also be a gaping hole in your perimeter defense.
To ensure your APs don’t allow unauthorized access, make sure wireless traffic is encrypted and requires strong keys. For more information on wireless security, see Introduction to Wireless Security.
Firewalls and IPS devices are not the only controls to secure your network perimeter, but they are the most common. Regardless of the technology deployed, the outcomes should match those described above.
Perimeter controls are important for keeping unwanted stuff- and people- off your network. The remaining control layers discussed in this article are required to protect against inside as well as outside threats.
Common Controls
The remaining controls apply to both connected devices and the network overall. No network is secure if attention isn’t paid to hardening servers, desktops, laptops, etc. These controls and supporting activities fall into the following layers of a defense in depth security strategy:
- Segmentation
- Host anti-virus and intrusion prevention
- Access control
- Secure configuration
- Monitoring, reporting and alerting
Segmentation
The concept of segmentation is simple; separate your critical infrastructure or sensitive data from the general access areas of your network. Deploy stronger- and usually more expensive- controls to protect the segments created. This is easier than it sounds.
The most common method of network segmentation is use of VLANs. VLANs (Virtual Local Area Networks) are network segments created via enterprise switch configuration. Refer to Figure 1.
Each VLAN is assigned an identifier. In this example, it is a single digit number. Access control lists (ACLs) determine if traffic is allowed to pass from one VLAN to another. (For more information about how to use VLANs for secure network segmentation, see Strengthen Data Protection with Network Access Controls.) Note that application servers and the database servers they access are on separate VLANs. VLAN 4 contains no sensitive data, so no special controls are in place. All sensitive information in this example is stored on database servers on VLAN 3.
Individual user devices are blocked from VLAN 3 with an ACL. So the only way to access the database servers is through an application server, and the application servers use service accounts to log into the databases. These service accounts have 24 random-character passwords known only to the security team.
Other “secure segment” controls you might consider include:
- A firewall used as a gateway, providing additional control over traffic entering the secure segment
- An IPS through which all traffic in and out of the secure segment passes, watching for unexpected data transfers/activity
Host Anti-malware and Intrusion Prevention
Every device connected to the network should be “hardened.” Hardening includes installing and maintaining anti-malware software on securely configured- and patched- systems. It also includes using server- or end-user-hosted IPS software. Placing IPS solutions, including software firewalls, on end-point devices accomplishes two security objectives. First, it creates a final defensive line to deal with unwanted malware or human activity that might have made it through all the other layers. Second, it helps isolate unwanted behavior if a connected device is compromised. For example, a worm finding its way onto a desktop will have a hard time connecting to other computers if those devices are locked down and the infected desktop blocks questionable outbound connections.
Access Control
When most people think of access control, they picture logging into their computer in the morning. While this is indeed an example of access control, it is only a small part of an overall network access control strategy.
A comprehensive strategy includes:
- User logins.
- System-to-system authentication. When a computer contacts another computer, especially if sensitive data is involved, the two computers should authenticate each other. This is typically accomplished with certificates or other controls which uniquely identify devices.
- Control of network segment access. The best way to begin protecting your data is to allow only those computers with an absolute business need to even see the data repositories. As we discussed earlier, this is accomplished with a combination of network segmentation, access control lists, and other controls deemed appropriate.
- Restricting physical access to critical infrastructure. Although this article focuses on technical controls, it’s important to include the importance of physical security. No amount of technical security will protect your data if an attacker can gain physical access to your critical infrastructure.
Secure Configuration
Secure configuration, or hardening, of devices is probably the best way to protect your data. It includes:
- Disabling all ports/services not absolutely required
- Applying security patches as soon as is reasonable after release
- For firewalls and other network control devices, beginning by denying all traffic and open only what is required for the business to operate
- As far as is reasonable and appropriate, following vendor recommendations for securing your operating systems, switches, routers, etc.
Monitoring, Alerting, and Reporting
Several years ago, my CIO at the time drilled into my sometimes hard head one very important principle: inspect what you expect. In other words, under no circumstances should you assume that what is supposed to be happening is actually happening. Although this was intended as a general management lesson, it is also an important element of enterprise security.
Your prevention and detection controls don’t always work as designed- or as you think you designed them. So you must always include monitoring, alerting, and reporting as outcomes for every control implementation project. These outcomes include not only whether the controls are actually working; they should also help identify anomalous events that only human intuition and experience might consider a problem event.
The best way to bring all this together is log management. A log management solution aggregates logs to a central repository from all security, LAN/WAN, and other key devices. The aggregated data is then passed through a correlation engine designed to look for collections of events with a high probability of being a security incident.
For more information about log management, see Use security log management to monitor network activity.
The Final Word
Network security is not some monolithic solution you can simply unbox and turn on to protect your data and critical infrastructure. Rather, it is a collection of controls, supporting an overall business strategy, that work together to mitigate risk. So the next time you discuss network security with your manager or your employees, keep in mind the many working parts required to successfully protect your information assets.
This post is part of the series: Understanding Network Security
In this series, we explore the definition of network security, what it means to secure a network and the types of controls available, and necessary, for basic protection.