The Dangers of Alternate Data Streams - Files Hidden Inside of other Files
File Streaming
Alternate Data Streams with the NTFS file system, can allow someone with malicious intent to hide information (data) behind a file name. It is generally not detectable by untrained users. Users looking for this file will not be able to find it. The only way the file can be seen is if it is accessed using the name of the stream. This file becomes a secret file within a file that only be accessed by using the file name or “secret name” which is the name of the stream itself.
File streaming or Alternate Data Streams only works on a NTFS file systems. Because Windows 2000, Windows XP and Windows Vista are in use today; these are vulnerable systems. Great care needs to be taken in protecting these operating systems from malicious users.
How Streaming Occurs
NTFS is one best file systems available and certainly the most used. So what happens when someone wants to hide a file inside of a file?
The individual hiding a file uses a command prompt in order to start the process.
Command Prompt
Using Notepad to Create the File
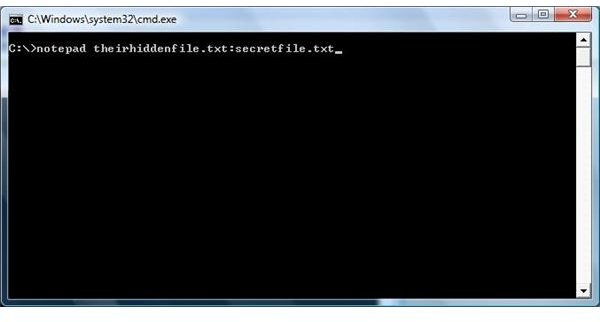
The user then types notepad theirhiddenfile.txt:secretfile.txt at the command prompt. (See Picture Below)
Using Notepad to Create the Files
Working With the File
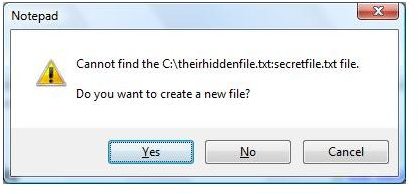
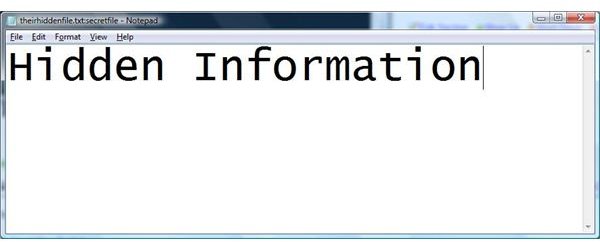
In the above scenario, we use the two files combined together to create the hidden streamed file. The file names can be any name the user wants. Once the user hits enter, the user will be prompted to create a new file and will hit enter, type any information they want to hide and save the file.
Prompt for New File
Examining the File Through Explorer
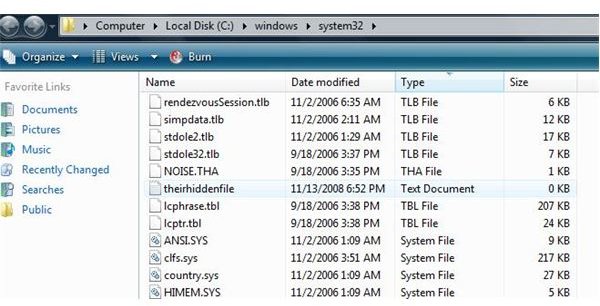
If you examine the file by using explorer at this time, you will see that the file appears to take up 0 space (See Picture Below). If you open the file, you will see the file is blank. Your hidden information is held in the stream or Alternate Data Streams.
Zero File Size!
Using the Open File
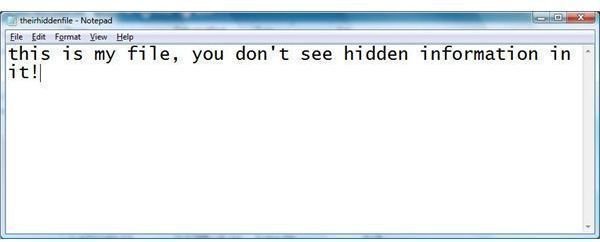
If they use the open file by double clicking, they can enter whatever they wish to. This information can be seen by anyone. The hidden data is in the ‘other’ notepad file. The picture below shows data in the ‘open’ file.
Open or Public File that can be Seen
Adding to the Hidden File
To open the hidden file, simply go to a command prompt and type the same command: notepad theirhiddenfile.txt:secretfile.txt
Information can be entered and modified as necessary thus hiding whatever the user wants.
The Dangers and Detection
Alternate data streams and file streams for Windows NTFS file system is a real threat for administrators. Hiding pornography, company secrets, terrorism and other malicious activities can occur on systems that are not restricted. Most administrators and security analyst don’t think this is used or not widely used. This technology to hide information has been used for years and continues to be used.
There are freeware tools that can help detect these files. Two of these tools are lads and lns . These easy to use tools can detect systems that may have hidden alternate data streams and file streams. These tools should be kept and used by administrators and support personnel.
Prevention
It is very important to give the users of your computers only the necessary rights. Active Directory with the appropriate policies should be in place as necessary. You must keep your computer up to date with all patches and service packs. All add on software including third party software needs to be updated. Restrict the command prompt and prevent users from having this capability.